You notice a high number of SQL injection attacks against a web application run by your organization, so you install a web application firewall to block many of these attacks before they reach the server. How have you altered the severity of this risk
Answers
By installing a web application firewall, you have effectively reduced the severity of the risk posed by SQL injection attacks against the web application run by your organization. The web application firewall acts as a protective layer between the attackers and the server, analyzing incoming traffic and blocking any suspicious or malicious requests that could potentially exploit vulnerabilities in the web application.
Here's how the installation of a web application firewall alters the severity of this risk:
1. Prevention of attacks: The web application firewall is designed to detect and block SQL injection attacks in real-time. It examines incoming requests and compares them against a set of predefined security rules. If a request is identified as potentially harmful, it is blocked before reaching the server, preventing the attack from being executed.
2. Mitigation of vulnerabilities: SQL injection attacks take advantage of vulnerabilities in the web application's code or configuration. By blocking these attacks, the web application firewall helps mitigate the underlying vulnerabilities by preventing malicious actors from exploiting them.
3. Reduction of potential damage: SQL injection attacks can lead to unauthorized access to sensitive data, data manipulation, or even complete server compromise. By blocking these attacks, the web application firewall reduces the potential damage that could be caused to the web application and the data it stores.
4. Improved security posture: With the web application firewall in place, your organization demonstrates a proactive approach to security. By actively preventing SQL injection attacks, the severity of the risk is decreased, as potential attackers are deterred and the chances of a successful attack are significantly reduced.
In summary, the installation of a web application firewall reduces the severity of the risk posed by SQL injection attacks by preventing these attacks from reaching the server, mitigating vulnerabilities, reducing potential damage, and improving the overall security posture of the web application.
To know more about malicious visit:
https://brainly.com/question/32063805
#SPJ11
Related Questions
How do I make the text and heading different colors?
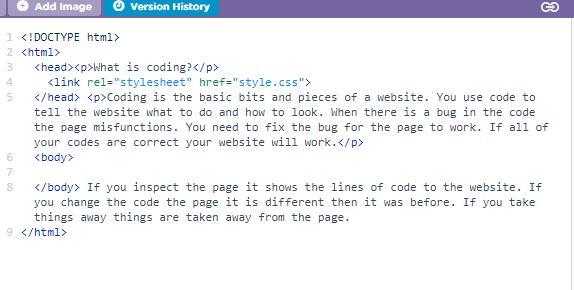
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
e. Define the term ‘user interface’, giving examples.
f. What is a mobile application?
g. Explain briefly what a multi-tasking system is and how it works?
Answers
Answer:
uExplanation:
iiiiiiiiiiiiiiiiiiii
CALCULATE THE MECHANICAL ADVANTAGE (MA).
DATA: F= 135 kg; b= 4*a; L=15 m
Answers
The mechanical advantage (MA) of the lever system in this scenario can be calculated by dividing the length of the longer arm by the length of the shorter arm, resulting in an MA of 4.
To calculate the mechanical advantage (MA) of the lever system, we need to compare the lengths of the two arms. Let's denote the length of the shorter arm as 'a' and the length of the longer arm as 'b'.
Given that the longer arm is four times the length of the shorter arm, we can express it as b = 4a
The mechanical advantage of a lever system is calculated by dividing the length of the longer arm by the length of the shorter arm: MA = b / a.
Now, substituting the value of b in terms of a, we have: MA = (4a) / a.
Simplifying further, we get: MA = 4.
Therefore, the mechanical advantage of this lever system is 4. This means that for every unit of effort applied to the shorter arm, the lever system can lift a load that is four times heavier on the longer arm.
For more such question on system
https://brainly.com/question/12947584
#SPJ8
The complete question may be like:
A lever system is used to lift a load with a weight of 135 kg. The lever consists of two arms, with the length of one arm being four times the length of the other arm. The distance between the fulcrum and the shorter arm is 15 meters.
What is the mechanical advantage (MA) of this lever system?
In this scenario, the mechanical advantage of the lever system can be calculated by comparing the lengths of the two arms. The longer arm (b) is four times the length of the shorter arm (a), and the distance between the fulcrum and the shorter arm is given as 15 meters. By applying the appropriate formula for lever systems, the mechanical advantage (MA) can be determined.
Which sentence combines information about both passages (tricky tomatoes and killer tomatoes)
Answers
The fact that tomato plants constantly communicate about insects describes tomatoes as both killer and tricky tomatoes.
Which claim is corroborated by deadly and difficult tomatoes alike?The attack on the housewife by the tomato that starts the movie. The fact that what the police initially thought was blood was actually tomato juice intrigues them. Attacks are becoming more frequent, so the government steps in.
What Is Tomatoes Sentence?Letters create words, and then words create sentences. In most cases, a sentence finishes with a full stop and always starts with a capital letter. The Naming and Doing components of a sentence are always present.
To know more about tricky tomatoes visit :-
https://brainly.com/question/21335974
#SPJ4
A computer is performing a binary search on the sorted list of 7 numbers below.
What is the maximum number of iterations needed to find the item?
[1, 5, 20, 50, 51, 80, 99]
A. 1
B. 3
C. 6
D. 7
Answers
Answer:
B
Explanation:
Binary search will start in the middle of the list, find which side the value is at, then look at the middle of those values. This is incredibly efficient for larger values (Although it needs to be sorted) and practical in many instances. Let's say that the desired number is 1, the binary search would look at "50" first, then proceed to compare with "5" and finally on it's third iteration, pick 1.
The maximum number of iterations needed to find the item is; Option B: 3
We are given the list of numbers as;
[1, 5, 20, 50, 51, 80, 99]
Now, when conducting binary search, it usually starts in the middle of the list of given numbers.Thereafter, the next step is to find the side that the value being searched for is located before looking at the middle of those values.Now, if the number being searched for in the given list is 1, it means that the binary search would first look at the middle number which is 50. Thereafter, it will proceed to compare it with the second number 5 and the lastly with the third iteration, will be 1.Thus,the number of iterations needed to find the item is 3 iterations.
Read more about binary search at; https://brainly.com/question/24786985
Could someone please tell me why the highlighted statement is returning 0.00000 instead of 9.1 (my input)? (IN DETAIL)
p.s. this is C programming language.

Answers
Answer:
You need to change the data type of "points" to a double.

What is burning in Computers and technology
Answers
So that is why people talk about "burning" songs or files to CDs. They could just say they are "writing" the data to a CD, and it would make sense, but people seem to think "burning" sounds cooler.
Answer:
Burn-in is a test in which a system or component is made to run for an extended period of time to detect problems. Burn-in may be conducted to ensure that a device or system functions properly before it leaves the manufacturing plant or may be part of a repair or maintenance routine.
Explanation:
hope this helps
All blueprints based on the actor class have the input enabled by default. Choose one • 1 point true false
Answers
Answer:
true
Explanation:
All blueprints based on the actor class have the input enabled by default, is the true statement.
What is blueprints?In blueprints, a kind of construction sketch, the location of components like doors, windows, sinks, and appliances as well as the design of the structure are all indicated. Simply put: A set of blueprints are required to build a structure.
To this day, any floor plan is still referred to by the informal term "blueprint" and even less formally, any type of plan. Working engineers, architects, and drafters regularly use the terms "drawings," "prints," and "plans." It has largely been replaced by the use of digital, computer-aided building designs.
A blueprint is a detailed action plan or a replica of a building or engineering plan with white lines on a blue background.
Thus, it is a true statement.
For more information about blueprints, click here:
https://brainly.com/question/15718773
#SPJ5
You have written a search application that uses binary search on a sorted array. In this application, all keys are unique. A co-worker has suggested speeding up access during failed searching by keeping track of recent unsuccessful searches in a cache, or store. She suggests implementing the cache as an unsorted linked-list.
Select the best analysis for this scenario from the list below:
A. In some circumstances this may help, especially if the missing key is frequently search for.
B. An external cache will always speed up the search for previously failed searches, but only if an array-based implementation is used.
C. This is a good idea as the the linked-list implementation of the cache provides a mechanism to access the first item in O(1) steps.
D. This is always a bad idea.
Answers
The option A is the correct answer.Option A is the best analysis for this scenario from the list below. Here's why:Explanation:The binary search algorithm is used to find a particular key in a sorted array. In the case of a failed search, it takes log2 n comparisons to determine that the key is not present in the array.
If the application frequently searches for the missing key, the time required to access the array can be reduced by storing recent unsuccessful searches in a cache or store.In certain scenarios, such as when the absent key is often looked for, this might help.
An unsorted linked-list can be used to implement the cache. In such a case, the linked-list implementation of the cache provides a way to access the first item in O(1) steps. It is preferable to keep an external cache. However, it will only speed up previously unsuccessful searches if an array-based implementation is employed.
To know more about key visit:-
https://brainly.com/question/31937643
#SPJ11
how do you know that a song is included speed
Answers
Answer:
the tempo determines the performance speed of the music. So when you count how many beats are in one minute of a song played at a specific tempo, you can quickly determine the Beats Per Minute or BPM. And if you're pressed for time, count the beats in 15 seconds of music, and then multiply that number by 4.
Explanation:
marks as an brilliant
Why are charts and graphs included in documents rather than just raw data?
Answers
Answer:
It's more organized and easier to look at
Explanation:
If it was just the raw data, it would take more time to analize, rather than it already being in a chart or graph
Exercise 6.8.6: Totals of Lots of Rolls 5 points
Use the previous program that rolls a 6-sided die 100 times.
This time, instead of printing out the result of EACH roll, only print out the sum of the rolls for each number.
For example:
You rolled 24 ones.
You rolled 15 twos.
etc.
Write down the summary from one of the simulations to use in the next exercise.
Help plz
Answers
Answer: good luck
Explanation:
The development of computer languages is classified into two categories .
true or false
Answers
Answer:
False
Explanation:
Mark me as a brainliest
after reviewing your slide, you realize that it could be improved. what steps do you take to make the two text boxes beneath the header more effective? select all that apply. 1 point ensure the text does not simply repeat the words you plan to say edit the text to fewer than 25 words total use abbreviations to reduce the amount of text edit the text to fewer than five lines total
Answers
After reviewing your slide, you realize that it could be improved. To make the two text boxes beneath the header more effective on must:
A slide is a single presentation page. A slide deck is a collection of slides that are used together. A slide show is an electronic device or projection screen presentation of a sequence of slides or photographs.
Avoid paragraphs, quotes, and even whole phrases when creating a fantastic slide presentation. Restrict your slides to five lines of text and make your arguments with words and phrases.
Key topics will be easier to consume and keep for the audience. Use your slides for more than just speaker notes or to portray an outline of your presentation.
Learn more about text boxes:
https://brainly.com/question/20034650
#SPJ1
Modify the binary search algorithm to take the upper of the two
middle array elements in case the input array has even length. In
other words, in the binary search algorithm, replace
Trace the action
Answers
The binary search algorithm can be modified to handle arrays with even lengths by considering the upper of the two middle elements as the pivot. This modification ensures that the algorithm works correctly and efficiently for arrays of any length.
In the traditional binary search algorithm, the pivot is chosen as the middle element of the array. This works well for arrays with odd lengths, but poses a challenge when the array length is even. In such cases, there is no exact middle element. To address this, we can modify the algorithm to consider the upper of the two middle elements as the pivot.
When dividing the array in half during each iteration, we can calculate the middle index as (low + high) // 2. However, for arrays with even lengths, we can modify this calculation to (low + high + 1) // 2 in order to choose the upper middle element as the pivot. By making this modification, the binary search algorithm can handle arrays of any length correctly. This ensures that the search process efficiently narrows down the search space and accurately finds the target element, regardless of the array's length.
Learn more about array here-
https://brainly.com/question/30757831
#SPJ11
it converts Assembly Language into machine language?
Answers
Answer:
An assembler.
Explanation:
Input is (as with any programming language) files with lists of instructions (typically assembler mnemonics), output is a binary format representing these instructions in machine language.
Ive accidently said yes to a 30 day free trial for amazon music and i have cancelled it but i went on my alexa abd it still plays unlimited music?? Plz someone help!!
Answers
Answer:
It might take some time to cancel
you want addem to now add all three values and return the sum and changeem to change x and y, but leave z alone. which should you do? a. redefine addem and changeem without referencing super.addem( ) or super.changeem( ) b. redefine addem to return the value of z super.addem( ), but leave changeem alone c. redefine changeem to call super.changeem( ) and then set z
Answers
Leave changeEm alone and redefine addEm to return the value of z + super addEm.
To accomplish polymorphism, what is used?Runtime polymorphism can be attained using Method Overriding. Method When a child or subclass has a method with the same name, inputs, and output as the parent or superclass, that method overrides the superclass function. This is known as overriding.
How is polymorphism achieved and what is it?Many classes that are related to one another by inheritance result in polymorphism, which is characterised as having "many forms." As was explained in the chapter before, we can use inheritance to take characteristics and methods from one class and apply them to another. Polymorphism employs a variety of methods to complete distinct tasks.
To know more about polymorphism visit:-
https://brainly.com/question/29850207
#SPJ4
HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!
Express the diagram in the form of a logic statement. [2]
P = ________________________
3. (a) Complete the truth table below for the logic circuit which is made up of NAND gates only.
![HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!Express the diagram in the form of a logic statement. [2] P = ________________________3.](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/NoE1DnieovxjZViB66UnB8fBINlICMCx.jpeg)
Answers
Answer:
different or difference between Dot-matrix and Daisy-wheel printer
Which properties of the word "readability” changed? Check all that apply.
Answers
Answer:
case
color
size
style
Explanation:
What is BASIC programming language?
Answers
BASIC,
in full (Beginner's All-purpose Symbolic Instruction Code,) computer programming language developed by John G. Kemeny and Thomas E. Kurtz at Dartmouth College in the mid 1960s.
FORTRAN
FORTRANComputer Programming History: FORTRAN was the first computer programming language that was widely used. A Brief History of Computer Programming Languages: Computer code is the foundation of computers, enabling them to do the tasks humans need them to do
FORTRANComputer Programming History: FORTRAN was the first computer programming language that was widely used. A Brief History of Computer Programming Languages: Computer code is the foundation of computers, enabling them to do the tasks humans need them to doplease make me brainalist and keep smiling dude I hope you will be satisfied with my answer
Write a program to declare an integer array of size 10 and fill it with random numbers using the random number generator in the range 1 to 5. The program should then perform the following: . Print the values stored in the array Change each value in the array such that it equals to the value multiplied by its index. Print the modified array. You may use only pointerioffset notation when solving the programt Example run: The sales red the fa (& 7 4- 8 A hp 144 ( 9 Add text 1 Draw P
Answers
We declare an integer array 'arr' of size 10. We then use the 'srand' function to seed the random number generator with the current time to ensure different random numbers on each program run.
Here's a program in C that fulfills the requirements you mentioned:
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
int main() {
int arr[10];
srand(time(NULL)); // Seed the random number generator
// Fill the array with random numbers between 1 and 5
for (int i = 0; i < 10; i++) {
arr[i] = rand() % 5 + 1;
}
// Print the original array
printf("Original Array: ");
for (int i = 0; i < 10; i++) {
printf("%d ", arr[i]);
}
printf("\n");
// Modify each value in the array by multiplying it with its index
for (int i = 0; i < 10; i++) {
arr[i] = arr[i] * i;
}
// Print the modified array
printf("Modified Array: ");
for (int i = 0; i < 10; i++) {
printf("%d ", arr[i]);
}
printf("\n");
return 0;
}
We fill the array with random numbers between 1 and 5 using the rand function. To limit the range, we use the modulo operator (%) to get the remainder when divided by 5 and add 1 to shift the range from 0-4 to 1-5.
We then print the original array using a for loop. After that, we modify each value in the array by multiplying it with its index. Finally, we print the modified array.
Each array element is accessed using pointer arithmetic notation, 'arr[i]', where 'i' represents the index of the element.
Upon running the program, you should see the original array printed first, followed by the modified array.
To know more about integer array
brainly.com/question/32893574
#SPJ11
Which CompTIA A+ exam puts a lot of emphasis on operational procedures, such as safety and environmental issues, communication, and professionalism?
a. 220-902
b. 920-202
c. 901-290
Answers
The CompTIA A+ exam that puts a lot of emphasis on operational procedures, such as safety and environmental issues, communication, and professionalism is a. 220-902.
The CompTIA A+ certification is a widely recognized credential for entry-level IT professionals. It consists of two exams: 220-901 and 220-902. While both exams cover a range of topics related to hardware, software, networking, and troubleshooting, the 220-902 exam specifically focuses on operational procedures and best practices.
This exam assesses a candidate's knowledge and understanding of various operational aspects, including safety protocols, environmental considerations, effective communication techniques, and maintaining professionalism in the IT industry. It emphasizes the importance of following industry standards, policies, and procedures to ensure a secure and efficient working environment.
By passing the 220-902 exam, candidates demonstrate their competence in handling operational procedures, understanding safety measures, and maintaining professional conduct within an IT setting.
To know more about CompTIA A+
brainly.com/question/32840630
#SPJ11
smart tv has _____ intergrated with it
Answers
Answer:
an operating system
Explanation:
Embedded computers usually are small and have limited hardware but enhance the capabilities of everyday devices. True or false?.
Answers
Embedded computers usually are small and have limited hardware but enhance the capabilities of everyday devices: True.
What is a computer?A computer can be defined as an electronic device that is designed and developed to receive data in its raw form as an input and processes these data through the central processing unit (CPU) into an output (information) that could be used by an end user.
What is a computer hardware?A computer hardware can be defined as a physical component of an information technology (IT) or computer system that can be seen and touched such as:
Random access memory (RAM).Read only memory (ROM).Central processing unit (CPU)KeyboardMonitorMouseMotherboard bios chipGenerally, embedded computers such as robotic vacuum cleaners, smart wrist-watches, home security systems, etc., usually are small and have limited hardware, but are designed and developed to enhance the capabilities of everyday devices.
Read more on embedded computers here: https://brainly.com/question/14614871
#SPJ1
Write code which takes a sentence as an input from the user and then prints the length of the first word in that sentence
Answers
Answer:
import java.util.*;
class StringProgram
{
public static void main(String s[])
{
Scanner sc = new Scanner(System.in);
System.out.print("Enter a Sentence: ");
String str= sc. nextInt();
// trim the white spaces at the beginning and at the end.
str = str.trim();
int c=0;
int i=0;
while(str.charAt(i++)!=' ')
++c;
System.out.println("Length of the first word in the sentence is: "+c);
}
}
Explanation:
Which letter shows the ball when it has the maximum kinetic energy
Answers
Answer:
D.
Explanation:
Kinetic energy can be defined as an energy possessed by an object or body due to its motion.
Mathematically, kinetic energy is given by the formula;
\( K.E = \frac{1}{2}MV^{2}\)
Where;
K.E represents kinetic energy measured in Joules. M represents mass measured in kilograms. V represents velocity measured in metres per seconds square.Generally, when the final velocity at which a physical object moves is equal to zero (0), then it possess maximum kinetic energy.
Hence, the letter which shows the ball when it has the maximum kinetic energy in the graph attached is D.

Write about Alarm System and evacuation protocol in detail
( WRITE BY USING COMPUTER PLEASE !!! )
Answers
Alarm systems and evacuation protocols play a vital role in ensuring the safety of individuals by promptly detecting hazards and facilitating organized evacuations during emergencies.
An alarm system is a mechanism that uses an alert to warn people of a potential danger. The most frequent use of an alarm system is to warn of a fire, but it may also be used for other purposes, such as notifying of a break-in or detecting dangerous gasses.
The system may be designed to detect the occurrence of an event or to provide an audible or visual signal when a predetermined threshold has been surpassed, such as when a sensor registers a certain level of heat or smoke. An evacuation protocol, on the other hand, is a sequence of procedures that are followed in the event of an emergency or catastrophe, such as a fire or gas leak. The goal of an evacuation protocol is to safely and efficiently evacuate individuals from a hazardous area and to provide them with the appropriate care and assistance.
The procedures in an evacuation protocol vary depending on the nature of the emergency, but the general process typically includes a warning signal, an assessment of the situation, and a plan to evacuate. For example, if a fire alarm system is activated, the evacuation protocol may involve sounding an alarm, alerting emergency personnel, and evacuating individuals to a designated safe area.
To know more about Alarm systems visit :
https://brainly.com/question/29834691
#SPJ11
In general, mainframe or server production programs and data are adequately protected against unauthorized access. Certain utility software may, however, have privileged access to software and data. To compensate for the risk of unauthorized use of privileged software, IT management can:______________
a. Keep sensitive programs and data on an isolated machine.
b. Restrict privileged access to test versions of applications.
c. Prevent privileged software from being installed on the mainframe.
d. Limit the use of privileged software
Answers
Answer:
a. Keep sensitive programs and data on an isolated machine.
Explanation: In general, mainframe or server production programs and data are adequately protected against unauthorized access. Certain utility software may, however, have privileged access to software and data. To compensate for the risk of unauthorized use of privileged software, IT management can:______________
When data is anonymized, the PII is eliminated or encrypted. PII includes names, Social Security numbers, addresses, and more and stands for ______ identifiable information.a. powerb. personallyc. publiclyd. private
Answers
When data is anonymized, the PII is eliminated or encrypted. PII includes names, Social Security numbers, addresses, and more and stands for personally identifiable information. The answer is (b).
PII refers to any information that can be used to identify an individual. This includes both direct identifiers such as name, address, and Social Security number, as well as indirect identifiers such as IP address and location data. Anonymization is the process of removing or encrypting PII from data sets to protect individuals' privacy and prevent unauthorized access to sensitive information.
You can learn more about personall identifiable information at
https://brainly.com/question/30023988
#SPJ11