You can start coding right away and understand requirements as you proceed with implementation.
a. True
b. False
Answers
The statement 'You can start coding right away and understand requirements as you proceed with implementation' is true.
When starting a coding project, it's common to iterate and refine your understanding of the requirements as you proceed with the implementation. This iterative approach is often referred to as an iterative or agile development process.
Therefore the answer is a.True
Learn more about coding: https://brainly.com/question/26134656
#SPJ11
Related Questions
What is printed as a result of executing the code segment if the code segment is the first use of a SomeClass object
Answers
Code segments are codes taken out from a more complete code or program
The result of executing the code segment would print 14
How to determine the resultTo determine the result, we simply run the program as follows:
public class SomeClass{
private int x = 0;
private static int y = 0;
public SomeClass (int pX){
x = pX;y++;
}
public void incrementY (){
y++;
}
public void incrementY (int inc){
y+= inc;
}
public int getY(){
return y;
}
public static void main (String [] args){
SomeClass first = new SomeClass (10);
SomeClass second = new SomeClass (20);
SomeClass third = new SomeClass (30);
first.incrementY();
second.incrementY(10);
System.out.println(third.getY());
}
}
The result of running the above program is 14
Hence, the result of executing the code segment would print 14
Read more about code segments at:
https://brainly.com/question/25781514
Rita used information from a blog that someone else wrote. What should she do?
Select all answers that apply.
Rita should use the information and hope that no one recognizes where it came from.
Rita should ask the original author for approval to use the information.
Rita should ask her teacher for approval to use the information.
Rita should give the author credit for their intellectual property by citing the source.
Answers
Answer:
rita should either ask the original author for permission to use her blog, but the best answer woyuld be that she should site her sources.
Explanation:
Modify the binary search algorithm to take the upper of the two
middle array elements in case the input array has even length. In
other words, in the binary search algorithm, replace
Trace the action
Answers
The binary search algorithm can be modified to handle arrays with even lengths by considering the upper of the two middle elements as the pivot. This modification ensures that the algorithm works correctly and efficiently for arrays of any length.
In the traditional binary search algorithm, the pivot is chosen as the middle element of the array. This works well for arrays with odd lengths, but poses a challenge when the array length is even. In such cases, there is no exact middle element. To address this, we can modify the algorithm to consider the upper of the two middle elements as the pivot.
When dividing the array in half during each iteration, we can calculate the middle index as (low + high) // 2. However, for arrays with even lengths, we can modify this calculation to (low + high + 1) // 2 in order to choose the upper middle element as the pivot. By making this modification, the binary search algorithm can handle arrays of any length correctly. This ensures that the search process efficiently narrows down the search space and accurately finds the target element, regardless of the array's length.
Learn more about array here-
https://brainly.com/question/30757831
#SPJ11
Please write 10 sentences for daily journal
Period: construction
Answers
Explanation:
What is 10×148(7-10)+12÷48+1
What is decision support system
Answers
A decision support system (DSS) is a computer program application that helps businesses make better decisions. Large volumes of data are analyzed, and the best solutions are then presented to an organization.
What is decision support system?One might be argued that a DSS is anything that offers logical, quantifiable, and scientific data to assist leaders in making educated decisions. Examples of decision support systems include complex decision support software, manual systems, etc.
Note that it is a group of computerized information systems called decision support systems (DSS) provide assistance for decision-making processes. Interactive computer-based systems and subsystems.
Learn more about decision support system from
https://brainly.com/question/7655444
#SPJ1
(a.)Name the command one would use to repair cross -linked files in graphical user interface software.
Answers
A command one would use to repair cross -linked files in graphical user interface software. is the Running of CHKDSK from Command Prompt.
What is Cross-linked files?Cross-linked files, also known as "linked files," occur when two or more files are connected to each other in such a way that modifying or deleting one file can affect the other files. In general, repairing cross-linked files may involve separating the files and breaking the link between them.
To repair cross-linked files in a GUI software, you may need to use a tool or command specifically designed for this purpose.
For example, some GUI software may have a "Repair Links" or "Break Links" option that you can use to fix cross-linked files. Other software may have a command-line interface that allows you to use specific commands to repair cross-linked files.
Note that the answer above is general and without more information about the specific GUI software you are using in the above, it is difficult to provide a more specific answer.
Learn more about graphical user interface from
https://brainly.com/question/14758410
#SPJ1
True or False
1. To access backstage view you will click file tab
2. Select file then it will appear the several templates below the blank workbook
option
3. Select template in the backstage view
4. There will be additional information how the template can be used when a preview of
the template will appear
5. Click save to use the selected
Answers
Answer:
Explanation:true
how many of you got the right answer from this app
Answers
Read the mini case study below. It documents a project’s (in some cases catastrophic) failure. In light of this module’s topics, discuss two contributing factors to the failure of this project.
Organization: Dyson Ltd – UK
Project type: Development of an electric car
Project name: The Dyson
Date: Oct 2019
Cost: £500M
Synopsis:
The future of transportation is here to see and it is of course electric! As a result, the development of electric cars has been a growth area for the past ten years and the pace of change continues to grow.
That growth and the potential to revolutionize the car market has interested both newcomers and the incumbents alike. Of the newcomers Tesla has of course made the cut and has proven they have the stamina to stay in the game. Other start-ups and have come, gone, been resurrected and gone again. At the time of writing Rivian, Fisker and other start-ups are still in the game, but they face the monumental challenge of taking on the likes of Volkswagen, Nissan, GM and other organizations that already have the infrastructure to design, build, sell and support vehicles on a worldwide basis.
One of the recent challengers to throw in the towel is Dyson Ltd. James Dyson is one of the UK richest men. An engineer, a techie and an entrepreneur, Dyson made his fortune developing high-end home appliances (most notably vacuum cleaners). Always looking for fields in need of his engineering prowess, Dyson started down the difficult road of developing a from-scratch electric car. The jump from vacuum cleaners to cars is of course massive and the decision to invest in the project was a quantum leap of faith.
Normally such a move would require careful due diligence and active management of the downside risks. It appears, however, that as a privately owned business, Dyson took a different path. In a Mar 2020 interview with business magazine "Fast Company" Dyson was asked about the role up front market analysis plays in developing Dyson products. Dyson replied…
"We never think of the market for the product. It’s not something that guides us. We look for a problem in the product, and then we go to solve the problem. Hand dryers aren’t a particularly big market compared to hair dryers or vacuum cleaners, but that didn’t stop us from wanting to make a hand dryer. Having an interesting technology for products decides what we do, whether the market is small or big."
To be fair, Dyson’s leap of faith did make a lot of progress and reports indicate that his nascent project got as a far as a fully functional vehicle that was near ready for production. However, as costs mounted past the £500M mark, the monumental costs of product launch came into view. Recognizing that to cover the investment and production costs the finished product was likely to have a price higher than the market would bare, the project has been canned.
Note: Dyson is a privately owned company and the cost of the project was apparently born by Mr. Dyson himself. Although Mr. Dyson can certainly afford to absorb the £500M cost, I think we should also remember the time, talent, sweat and tears of the team who work on the project. To see all of that effort wasted is a heart break in its own right. Hopefully some of the technology will still find a way forward and some of that effort will be rewarded, but as it stands, the project may not be catastrophic for Dyson, but it is likely a massive disappointment for those who vested themselves in the project’s success.
Answers
The failure of the Dyson electric car project can be attributed to a combination of factors. The lack of thorough market analysis and consideration of the competitive landscape prevented Dyson from adequately positioning their product in the automotive market.
Two contributing factors to the failure of the Dyson electric car project are:
Lack of market analysis and consideration of competitive landscape:
Dyson's approach of focusing primarily on solving a problem rather than considering the market demand and competition played a significant role in the project's failure. The decision to develop an electric car without thoroughly analyzing the market and understanding the challenges posed by established automotive manufacturers with global infrastructure put Dyson at a disadvantage. While Dyson had a track record of innovation and success in the home appliances industry, the automotive sector is highly complex and competitive. Not adequately assessing the market dynamics and competition hindered their ability to develop a competitive product and establish a viable market position.
Mounting costs and pricing challenges:
Although the project made substantial progress and reached the stage of a fully functional vehicle near production readiness, the costs associated with launching the product became a significant concern. As the costs exceeded £500 million, the realization that the final product would likely have a price higher than what the market would bear posed a major obstacle. Dyson's decision to halt the project can be attributed to the realization that the financial viability of the electric car was questionable due to the high production costs and anticipated pricing challenges. Failing to align the project's costs with market expectations and feasible pricing strategies contributed to its ultimate discontinuation.
The failure of the Dyson electric car project can be attributed to a combination of factors. The lack of thorough market analysis and consideration of the competitive landscape prevented Dyson from adequately positioning their product in the automotive market. Additionally, the mounting costs and pricing challenges posed significant financial risks and made the project economically unviable. While the project may not have had catastrophic consequences for Dyson as a company, it was undoubtedly a disappointment for the team involved and a missed opportunity to leverage their technological advancements in the automotive industry.
To know more about electric car visit
https://brainly.com/question/30016414
#SPJ11
jannah is working on setting up one of the features on her digital camera because she wants to have a dated analog of the images she takes so that she can see exactly when shots were taken. what feature is jannah setting up?
Answers
The feature Jannah is setting up analog dates of the image is timestamp.
What is timestamp?A timestamp is a token or packet of information used to ensure timeliness; It includes timestamped data, such as a time, as well as a signature generated by a Trusted Timestamp Authority (TTA).Timestamps are used for a variety of synchronization purposes, such as identifying the exact date and time of an event. A timestamp that includes a date in the form of a calendar date and a time in the form of a time of day.The TIMESTAMP data type is used for values that include both a date and a time component. The range of TIMESTAMP is from '1970-01-01 00:00:01' UTC to '2038-01-19 03:14:07' UTC. A DATETIME or TIMESTAMP value can have a trailing fractional seconds part with a precision of up to microseconds (6 digits).To learn more about timestamp refer to :
https://brainly.com/question/12950658
#SPJ4
Which of the following would be a type of constraint?
Naming the columns
Declaring a data type
Creating a table
Naming the table
Answers
The correct option is "Declaring a data type."
Declaring a data type is a type of constraint in database management systems. Constraints are rules or conditions applied to the data stored in a database to maintain data integrity and enforce certain restrictions. When declaring a data type for a column in a database table, you are specifying the type of data that can be stored in that column. This serves as a constraint because it restricts the type of values that can be inserted into that column.
Naming the columns, creating a table, and naming the table are not examples of constraints. They are elements of database design and administration, but they do not enforce any restrictions or rules on the data itself.
Learn more about data type here:
https://brainly.com/question/30615321
#SPJ11
The moment the frame information is stripped away from an ip packet, we move out of:___.
Answers
The moment the frame information is stripped away from an IP packet, we move out of: A. The link layer and into the Internet Layer.
What is the OSI model?OSI model is an abbreviation for open systems interconnection and it comprises seven (7) main layers, which typically starts from the hardware layers (layers in hardware systems) to the software layers (layers in software systems)
The layers of the OSI model.Basically, there are seven (7) layers in the open systems interconnection (OSI) model and these include the following in sequential order;
Physical LayerData link LayerNetwork LayerTransport LayerSession LayerPresentation LayerApplication LayerIn Computer networking, immediately the frame information is stripped away from an internet protocol (IP) packet, we transition out of the data link layer and into the Network Layer (Internet Layer) in accordance with the OSI model.
Read more on OSI model here: brainly.com/question/26177113
#SPJ1
Complete Question:
The moment the frame information is stripped away from an IP packet, we move out of:_____
The link layer and into the Internet Layer.
The link layer and into the Transport Layer.
The Transport layer and into the Session Layer.
The Physical Layer and Transport Layer
WILL MARK BRAINLIEST!!
What will be displayed after this code segment is run?
luckyNumbers + 15, 33, 25
INSERT lucky Numbers, 2, 13
APPEND lucky Numbers, 3
REMOVE lucky Numbers, 1
DISPLAY LENGTH luckyNumbers
Please explain!! :)

Answers
Answer:
Output: 4
Explanation:
You start with [15,23,25]
You insert 13 at index 2 [15,13,33,25]
Append 3 [15,33,25,3]
Output length of array: 4
The output that will be displayed after the code segment is run is 3
The flow of the algorithm is as follows:
luckyNumbers <- 15, 33, 25:This above line initializes a list
INSERT lucky Numbers, 2, 13:The above line replaces the number in the 2nd index with 13.
So, the list becomes 15, 33, 13
APPEND lucky Numbers, 3The above line appends 3 at the end of the list.
So, the list becomes 15, 33, 13, 3
REMOVE lucky Numbers, 1The above line removes the number in the 1st index
So, the list becomes 15, 13, 3
DISPLAY LENGTH luckyNumbers
The above line prints the count of numbers in the list i.e. 3
Hence, the output that will be displayed after the code segment is run is 3
Read more about algorithms at:
https://brainly.com/question/24793921
what is the proper way of creating a thread class if the class has already inherited members from another class?
Answers
The proper way to create a thread class when the class already inherits members from another class is to extend the Thread class in your class and override the run() method.
What is Threads?
Threads is an operating system feature that enables multiple tasks to be performed at once. It is an approach to concurrent programming that allows a program to divide itself into two or more simultaneously running tasks. These tasks are known as threads and are executed concurrently. Threads are a lightweight alternative to processes, making them ideal for applications that require multiple computations to be performed simultaneously. Threads allow for efficient multitasking and can reduce the amount of time it takes to complete a task.
To know more about Threads
https://brainly.com/question/13155644
#SPJ4
A network administrator is looking at the security of their Domain Name System servers and is researching common attacks against DNS. Which of the following is NOT as common of an attack geared towards DNS services?
Question options:
a. Flood attacks
b. Rogue server
c. Zone transfer
d. Cache Poisoning
e. SMB attacks
Answers
The type of attack that is not as common of an attack geared towards DNS services when an administrator is researching is SMB attacks. The correct option is e.
The domain name system (DNS) is a naming database for the internet that converts human-readable domain names to numerical IP addresses. It's also a distributed database that's managed in a hierarchy by a collection of domain name servers. The domain name system is a significant aspect of the internet because it allows people to locate web servers using easy-to-remember domain names rather than IP addresses. It also makes it easier for network administrators to manage and monitor their networks.In addition, it can enhance the speed of DNS queries, since DNS caching can be used to store results for a period of time. This, in turn, reduces the load on authoritative servers and shortens response times. The cache, on the other hand, must be managed properly to ensure that stale information is not used. Attacks that target DNS systemsThe security of DNS servers is crucial, and the following types of attacks are commonly targeted at DNS:Cache Poisoning: Attackers provide incorrect DNS data in order to redirect traffic to a malicious server.Flood attacks: Attackers use a large number of requests to consume system resources and deny service to legitimate users.Rogue server: Attackers create rogue DNS servers that can cause data theft, malware distribution, or other forms of attack.Zone transfer: Attackers extract the entire zone file from a DNS server to learn about the server's domain and structure, which can be used in other attacks.SMB attacks: The Server Message Block protocol is used by attackers to exploit vulnerabilities in DNS servers that use Microsoft technology.Therefore, the correct option is e ''SMB attacks.''Learn more about DNS here: https://brainly.com/question/27960126
#SPJ11
1. (A+B)(B'+C)(C+A)
2. A'B'C'
3. (X+Y)(X'+Z)(Y+Z)
4. A'B'C'+A'BC'+A'BC+ABC'
Answers
you need to put your question
You invited your product owner to the upcoming iteration retrospective. She thanked you for the invitation and told you that she would look forward to the session and would like to adopt good ideas. Which ESVP role closely relates to this attitude?
Answers
The ESVP role that closely relates to the attitude of the product owner in this scenario is "S" - Supporter. In the ESVP model, which stands for Expert, Supporter, Visionary, and Pragmatist,
the Supporter role is characterized by a positive attitude towards change and a willingness to adopt new ideas or approaches. Supporter individuals are typically open-minded, cooperative, and willing to collaborate with others to achieve team goals.
In this scenario, the product owner's response of thanking for the invitation, expressing a positive attitude towards the upcoming iteration retrospective, and mentioning a willingness to adopt good ideas aligns with the characteristics of a Supporter role in the ESVP model. The product owner's openness and willingness to embrace new ideas and collaborate with the team during the retrospective reflect a supportive and cooperative mindset towards the agile team's improvement efforts.
Learn more about product owner here:
https://brainly.com/question/16412628
#SPJ11
If you give someone ______ to your device, they can control it through another phone or computer.
Answers
If you give someone Remote access to your device, they can control it through another phone or computer.
What is Remote entry?An authorized user can use remote access to connect to a computer or network from a different location using a network connection. Users can connect to the systems they require through remote access even if they are physically far away.
Therefore, the dangers to remote access are:
There is a risk of device loss or theft due to a lack of physical security safeguards.as the data is transmitted through a public internet, eavesdropping.unapproved access to systems or data, possibly while oblivious to the screen.If someone gets access to the gadget, they could watch and change the data.Learn more about Remote access from
https://brainly.com/question/28900477
#SPJ1
7.2 code practice edhesive. I need help!!
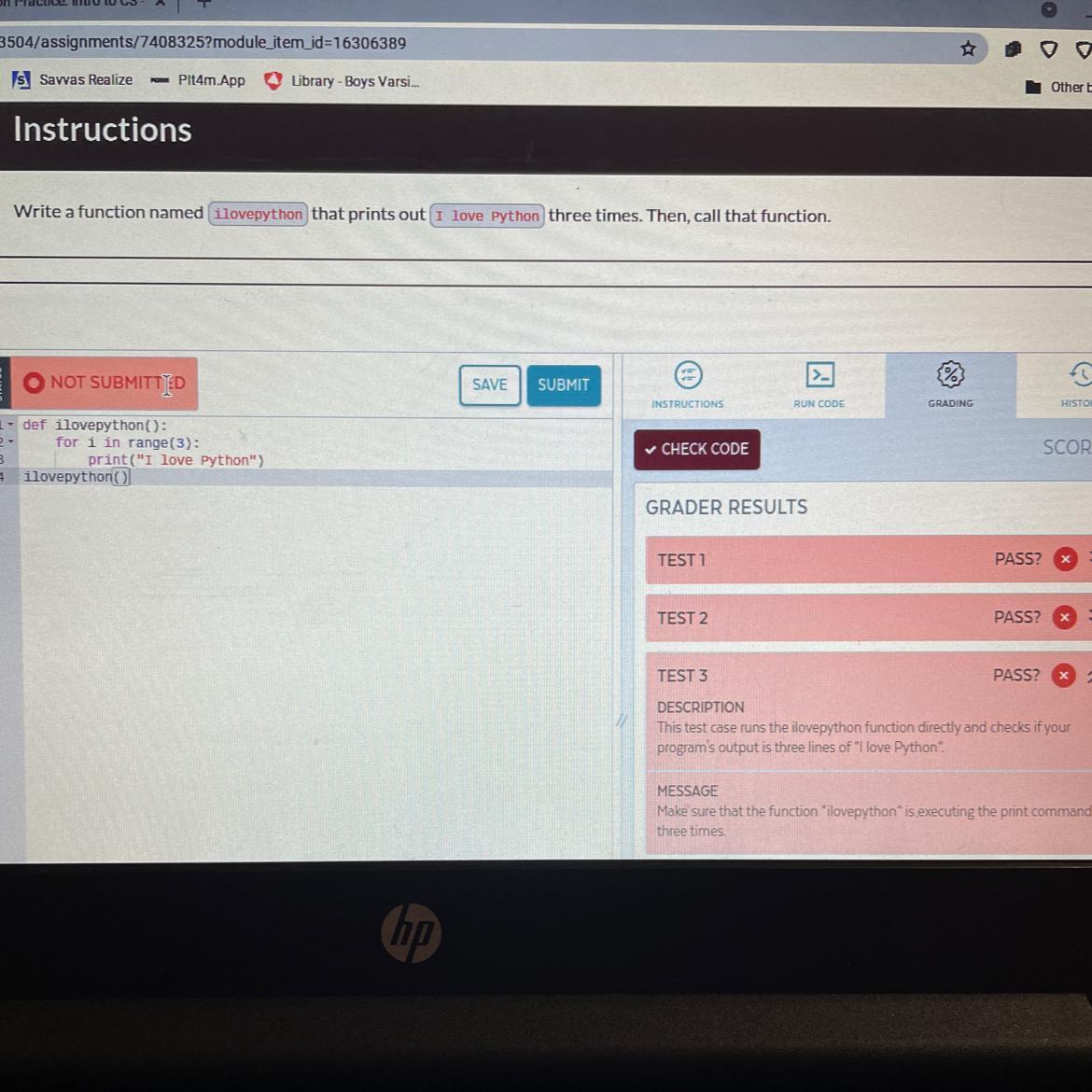
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
Which actions help to protect a computer and keep it running properly? Check all that apply.
performing regular scans
deleting any unwanted files
backing up files and other data
saving Internet browsing history
saving and storing all junk files
Answers
saving and storing all junk files
deleting any unwanted scans
Answer:
ABC
Explanation:
100% EDGE 2022
Say you have an array for which the ith element is the price of a given stock on day i. If you were only permitted to complete at most one transaction (ie, buy one and sell one share of the stock), design an algorithm to find the maximum profit.
Answers
To find the maximum profit from buying and selling a stock in an array, we can use a simple algorithm that iterates through the array while keeping track of the minimum price encountered so far and the maximum profit that can be achieved.
We can initialize two variables, "min_price" and "max_profit," to store the minimum price and maximum profit values, respectively. Initially, set the minimum price as the first element of the array and the maximum profit as zero. Next, iterate through the array starting from the second element. For each element, calculate the potential profit by subtracting the minimum price from the current element. If this potential profit is greater than the maximum profit, update the maximum profit.
Additionally, if the current element is less than the minimum price, update the minimum price to the current element. By doing this, we ensure that we always have the lowest price encountered so far. After iterating through the entire array, the maximum profit will be stored in the "max_profit" variable. Return this value as the result. This algorithm has a time complexity of O(n), where n is the length of the array. It scans the array once, making constant time comparisons and updates for each element, resulting in an efficient solution to find the maximum profit from buying and selling a stock.
Learn more about algorithm here-
https://brainly.com/question/31936515
#SPJ11
Tech Town has been hit with a bad storm and the town is suffering from severe flooding. The kids have no way to get to school.Tech Town has been hit with a bad storm and the town is suffering from severe flooding. design a solution to solve the problem. i have to collect supplies around your house for your solution. What could i build?
Answers
Answer:
May 28, 2020 — What's left of Tropical Storm Bertha will move through the Ohio Valley and ... the southern storm system to create severe weather for the Northeast on ... in Sacramento of 103 degrees, even Death Valley hit a record high of ... Las Vegas got to 107, missing the record just by 1 degree. ... Do Not Sell My Info ...Hurricane Sandy was the deadliest and most destructive, as well as the strongest hurricane of ... The eighteenth named storm, tenth hurricane, and second major hurricane of the year, ... Its storm surge hit New York City on October 29, flooding streets, tunnels and subway lines and cutting power in and around the city.
Explanation:
write a program to print the smallest number among three numbers
Answers
Answer:
min(a_list)
sort(a_list); a_list[0]
if this is cheating use conditionals, PYTHON
What are the pros and cons for E-trade?
Answers
Answer:
Pros Cons
• Free stock and ETF trading • Higher fees for non-free mutual funds
• Some mutual funds and bonds are free
• Low non-trading fees
Answer:
Pros-Quick, easy purchases, ability to know what's available, access to limitless products.
Cons-Potential to get hacked, get scammed by false advertising, amount of time to receive product
Explanation:
Its not a great list but I really hope this helps
Solution of higher Differential Equations.
1. (D4+6D3+17D2+22D+13) y = 0
when :
y(0) = 1,
y'(0) = - 2,
y''(0) = 0, and
y'''(o) = 3
2. D2(D-1)y =
3ex+sinx
3. y'' - 3y'- 4y = 30e4x
Answers
The general solution of the differential equation is: y(x) = y_h(x) + y_p(x) = c1e^(4x) + c2e^(-x) + (10/3)e^(4x).
1. To solve the differential equation (D^4 + 6D^3 + 17D^2 + 22D + 13)y = 0, we can use the characteristic equation method. Let's denote D as the differentiation operator d/dx.
The characteristic equation is obtained by substituting y = e^(rx) into the differential equation:
r^4 + 6r^3 + 17r^2 + 22r + 13 = 0
Factoring the equation, we find that r = -1, -1, -2 ± i
Therefore, the general solution of the differential equation is given by:
y(x) = c1e^(-x) + c2xe^(-x) + c3e^(-2x) cos(x) + c4e^(-2x) sin(x)
To find the specific solution satisfying the initial conditions, we substitute the given values of y(0), y'(0), y''(0), and y'''(0) into the general solution and solve for the constants c1, c2, c3, and c4.
2. To solve the differential equation D^2(D-1)y = 3e^x + sin(x), we can use the method of undetermined coefficients.
First, we solve the homogeneous equation D^2(D-1)y = 0. The characteristic equation is r^3 - r^2 = 0, which has roots r = 0 and r = 1 with multiplicity 2.
The homogeneous solution is given by, y_h(x) = c1 + c2x + c3e^x
Next, we find a particular solution for the non-homogeneous equation D^2(D-1)y = 3e^x + sin(x). Since the right-hand side contains both an exponential and trigonometric function, we assume a particular solution of the form y_p(x) = Ae^x + Bx + Csin(x) + Dcos(x), where A, B, C, and D are constants.
Differentiating y_p(x), we obtain y_p'(x) = Ae^x + B + Ccos(x) - Dsin(x) and y_p''(x) = Ae^x - Csin(x) - Dcos(x).
Substituting these derivatives into the differential equation, we equate the coefficients of the terms:
A - C = 0 (from e^x terms)
B - D = 0 (from x terms)
A + C = 0 (from sin(x) terms)
B + D = 3 (from cos(x) terms)
Solving these equations, we find A = -3/2, B = 3/2, C = 3/2, and D = 3/2.
Therefore, the general solution of the differential equation is:
y(x) = y_h(x) + y_p(x) = c1 + c2x + c3e^x - (3/2)e^x + (3/2)x + (3/2)sin(x) + (3/2)cos(x)
3. To solve the differential equation y'' - 3y' - 4y = 30e^(4x), we can use the method of undetermined coefficients.
First, we solve the associated homogeneous equation y'' - 3y' - 4y = 0. The characteristic equation is r^2 - 3r - 4 = 0, which factors as (r - 4)(r + 1) = 0. The roots are r = 4 and r = -1.
The homogeneous solution is
given by: y_h(x) = c1e^(4x) + c2e^(-x)
Next, we find a particular solution for the non-homogeneous equation y'' - 3y' - 4y = 30e^(4x). Since the right-hand side contains an exponential function, we assume a particular solution of the form y_p(x) = Ae^(4x), where A is a constant.
Differentiating y_p(x), we obtain y_p'(x) = 4Ae^(4x) and y_p''(x) = 16Ae^(4x).
Substituting these derivatives into the differential equation, we have:
16Ae^(4x) - 3(4Ae^(4x)) - 4(Ae^(4x)) = 30e^(4x)
Simplifying, we get 9Ae^(4x) = 30e^(4x), which implies 9A = 30. Solving for A, we find A = 10/3.
Therefore, the general solution of the differential equation is:
y(x) = y_h(x) + y_p(x) = c1e^(4x) + c2e^(-x) + (10/3)e^(4x)
In conclusion, we have obtained the solutions to the given higher-order differential equations and determined the specific solutions satisfying the given initial conditions or non-homogeneous terms.
To know more about Differential Equation, visit
https://brainly.com/question/25731911
#SPJ11
if a router does not send an icmp message regarding a dropped packet, caused by the size exceeding the maximum transmission unit (mtu), what is that router called?
Answers
A router is referred to as a black hole router if it does not transmit an icmp message in response to a dropped packet whose size exceeds the maximum transmission unit (mtu).
What occurs if the MTU is exceeded?An incoming packet may be smaller than the MTU for a network device, but if the device encapsulates it and the new total packet size is more than the MTU of the outgoing interface, the device may fragment the packet into two smaller packets before delivering the data.
What is the router's MTU size?The largest size packet that can be sent in bytes without fragmentation is known as the MTU, or Maximum Transmission Unit. 1500 bytes is the maximum size permitted via Ethernet and by the majority of internet service providers.
To learn more about router visit:
brainly.com/question/29869351
#SPJ4
Procedural abstraction allows the programmer to change the internals of the procedure without needing to notify users of the change as long as it does the same thing as before. Why would a programmer want to make changes to a procedure if it already works as intended
Answers
Answer:
All of the options are true
Explanation:
The technical information section of Carmine's GDD is fairly brief because his team has included a separate document that explains all the technical information in far greater detail. What is this separate document referred to as?
tech addendum
technical debriefing
amendment to the technical
technical bible
Answers
Answer: tech addendum
Explanation:
The separate document that explains all the technical information in far greater detail is referred to as the technical addendum.
An addendum simply refers to an attachment that modifies the conditions of a contract or gives more information about the contract.
In this scenario, since the technical information section of Carmine's GDD is fairly brief, the tech addendum will explain all the technical information in far greater detail.
Please create 2 SMART Goals you believe will help you improve your digital footprint and post them in this discussion. Then select 2 classmates' SMART Goals and provide them with feedback on the strength of their goals.
Answers
Creating SMART goals is an effective way to improve one's digital footprint. Two SMART goals that can help in this regard are:
1. Goal: Increase my professional online presence by regularly publishing informative blog posts on relevant industry topics on my personal website.
- Specific: Publish at least two well-researched and valuable blog posts per month.
- Measurable: Track the number of views, comments, and social media shares for each blog post.
- Achievable: Allocate dedicated time each week for conducting research, writing, and editing blog posts.
- Relevant: Enhance my credibility and expertise in the industry, and attract potential clients or employers.
- Time-bound: Start implementing this goal from next month and continue for the next six months.
2. Goal: Improve my social media engagement and visibility by actively participating in industry-related discussions on LinkedIn.
- Specific: Join and contribute to at least three relevant LinkedIn groups, and post insightful comments or share valuable resources.
- Measurable: Monitor the number of likes, comments, and connections gained through LinkedIn interactions.
- Achievable: Set aside specific time slots each week for engaging with LinkedIn groups and connections.
- Relevant: Build a professional network, establish myself as a thought leader, and gain exposure to potential opportunities.
- Time-bound: Begin engaging on LinkedIn within the next two weeks and maintain consistent involvement for the next three months.
Learn more about SMART
brainly.com/question/24611078
#SPJ11
sql was developed under the name ____ at the ibm san jose research facilities.
Answers
SQL (Structured Query Language) was developed under the name SEQUEL (Structured English Query Language) at the IBM San Jose research facilities in the 1970s.
It was designed as a standardized language for managing and manipulating relational databases.
SQL allows users to create, modify, and query databases using commands such as SELECT, INSERT, UPDATE, and DELETE.
The language has become a standard for database management systems and is widely used in both commercial and open-source software.
With SQL, users can retrieve specific information from databases, organize and sort data, and create relationships between different tables.
SQL has greatly simplified the process of managing large amounts of data and has become an essential tool for businesses and organizations of all sizes.
Learn more about SQL at https://brainly.com/question/24180759
#SPJ11