Write a program that reads in 10 numbers and displays the number of distinct numbers and the distinct numbers in their input order and separated by exactly one space (i.e., if a number appears multiple times, it is displayed only once). After the input, the array contains the distinct numbers. Here is a sample run of the program.
Answers
Answer:
Explanation:
The following code is written in Python. It creates a for loop that iterates 10 times, asking the user for a number every time. It then checks if the number is inside the numArray. If it is not, then it adds it to the array, if it is then it skips to the next iteration. Finally, it prints the number of distinct numbers and the list of numbers.
numArray = []
for x in range(10):
num = input("Enter a number")
if int(num) not in numArray:
numArray.append(int(num))
print("Number of Distince: " + str(len(numArray)))
for num in numArray:
print(str(num), end = " ")

Related Questions
What is the difference between popular art and high art?
Answers
Answer:
Explanation: In contrast, popular art often follows proven formulas that have been shown to appeal to large groups
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
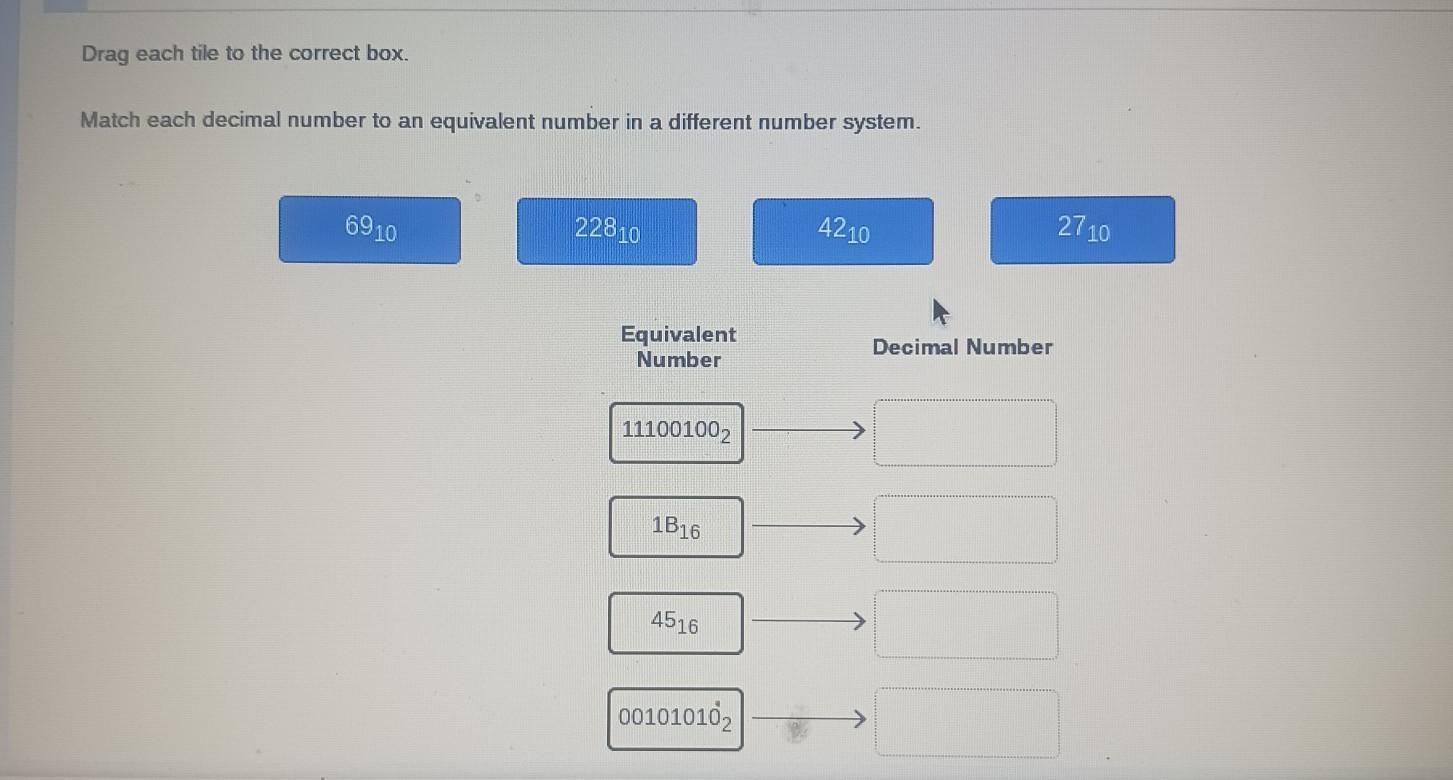
Answers
Explanation:
you can do that with calculator only

Which statements are true about mobile apps? Select 3 options.

Answers
The statements are true about mobile app development are;
Software development kits can provide a simulated mobile environment for development and testingMobile app revenues are expected to growWhether a mobile app is native, hybrid, or web, depends on how the app will be used and what hardware needs to be accessed by the appHow is this so?According to the question, we are to discuss what is mobile app and how it works.
As a result of this mobile app serves as application that works on our mobile phone it could be;
nativehybridwebTherefore, Software development kits can provide a simulated mobile environment.
Learn more about mobile apps at:
https://brainly.com/question/26264955
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
Which of the following statements are true about mobile app development? Select 3 options.
• Software development kits can provide a simulated mobile environment for development and testing
• Testing is not as important in mobile app development, since the apps are such low-priced products
• Mobile apps can either take advantage of hardware features or can be cross-platform, but not both
• Mobile app revenues are expected to grow
• Whether a mobile app is native, hybrid, or web, depends on how the app will be used and what hardware needs to be accessed by the app
Drag the tiles to the boxes to form correct pairs.
Match the camera mode setting with the correct definition
single shot
Sets a time delay on the closing of the shutter
allowing you to be part of the shot.
continuous shot
Lets you take one shot per press of the
shutter button
self-timer
Lets you take multiple pictures for as long
as you have the shutter button pressed down.
Answers
Here are the answers
#Single shot
Lets you take one shot per press of theshutter button#Continuous shot
Lets you take multiple pictures for as longas you have the shutter button pressed down.#Self timer
Sets a time delay on the closing of the shutterworking with the tkinter(python) library
make the window you create always appear on top of other windows. You can do this with lift() or root.attributes('-topmost', ...), but this does not apply to full-screen windows. What can i do?
Answers
To make a tkinter window always appear on top of other windows, including full-screen windows, you must use the wm_attributes method with the topmost attribute set to True.
How can I make a tkinter window always appear on top of other windows?By using the wm_attributes method in tkinter and setting the topmost attribute to True, you can ensure that your tkinter window stays on top of other windows, even when they are in full-screen mode.
This attribute allows you to maintain the window's visibility and prominence regardless of the current state of other windows on your screen.
Read more about python
brainly.com/question/26497128
#SPJ1
3. Never
to any instant messages, phone call, video call, or screen
staring requests from someone you do not know.
A. reply
B. refuse
C. forward text
D. accept pictures
Answers
Answer:
\(\color{Blue}\huge\boxed{Answer} \)
B.Refuse
Answer:
Never reply to any instant messages, phone call, video call, or screen staring requests from someone you do not know.
Hope it helps u ARMY!!
A common technique for masking contents of messages or other information traffic so that opponents can not extract the information from the message is __________ . Group of answer choices analysis integrity masquerade encryption
Answers
the answer is encryption!
i hope this helps! :]
A technician is installing new power supplies for the application engineering team's workstations. The management team has not yet made a decision about installing dual graphics cards, but they want to proceed with the project anyway. Which of the following power supplies would provide the BEST solution?
Answers
Answer:
a
Explanation:
The 500W redundant power supply. is the most ideal decision, offering adequate power and reinforcement in the event of a power supply disappointment. Hence, option C is the right answer.
Which of the following power supplies would provide the best solution?The BEST answer for the professional to install new power supplies for the application engineering team's workstations would be choice C: 500W redundant power supply.
A 1000W 24-pin measured power supply might be unreasonable for the workstations, possibly prompting failures and higher power utilization.
A 220VAC 9000J flood defender isn't a power supply; it just safeguards against voltage spikes.
A 2000VA uninterruptible power supply (UPS) may give reinforcement power in the event of blackouts, however, it isn't guaranteed to address the requirement for dual graphics cards.
The 500W repetitive power supply offers adequate power limits with respect to the workstations and overt repetitiveness, guaranteeing persistent activity regardless of whether one power supply falls flat. This considers potential double illustration cards from here on out, settling on it as the most reasonable decision for the task.
Learn more about power supply here:
https://brainly.com/question/29979352
#SPJ2
Worth 10 points
(Sum series)
Write a method to compute the following series:
m(i) = 1/2 + 2/3 +......+ i/(i+1)
Class Name: Exercise06_13
Answers
In Java:
public class Exercise06_13 {
public static void main(String[] args) {
System.out.println(Series(Just put whatever number you want here, and it will print out the number in the series.));
}
static float Series(float i){
return (i / (i + 1));
}
}
I hope this helps!
Describe how smartphones communicate. List and describe four popular types of messages you can send with smartphones. Write one well-written paragraph and answer the above question to earn 10 points.
Answers
The way that smartphones communicate is that people connect with each other and with businesses has been changed by mobile messaging. However, users and businesses can choose from a variety of mobile messaging types.
The Kinds Of Mobile Messaging are:
SMS & MMS MessagingPush Notifications.In-App Messages.RCS.What is the messaging about?Brief Message Service (SMS): One of the most popular types of mobile communications is SMS. A basic text message sent via a cellular signal is known as an SMS, or short messaging service.
SMS is completely text-based and has a character restriction of 160. Users in the United States who don't have an unlimited messaging package pay cents per message.
Therefore, in Notifications through Push: It's possible that you mistakenly believe that the thing that's flashing on your cell phone's screen is a text message. Similar to SMS messages, push notifications are pop-up windows that appear while you're using your phone or on the lock screen rather than in your inbox with other texts.
Learn more about Mobile Messaging from
https://brainly.com/question/27534262
#SPJ1
You need to migrate an on-premises SQL Server database to Azure. The solution must include support for SQL Server Agent.
Which Azure SQL architecture should you recommend?
Select only one answer.
Azure SQL Database with the General Purpose service tier
Azure SQL Database with the Business Critical service tier
Azure SQL Managed Instance with the General Purpose service tier
Azure SQL Database with the Hyperscale service tier
Answers
The recommended architecture would be the Azure SQL Managed Instance with the General Purpose service tier.
Why this?Azure SQL Managed Instance is a fully managed SQL Server instance hosted in Azure that provides the compatibility and agility of an instance with the full control and management options of a traditional SQL Server on-premises deployment.
Azure SQL Managed Instance supports SQL Server Agent, which is important for scheduling and automating administrative tasks and maintenance operations.
This would be the best option for the needed migration of dB.
Read more about SQL server here:
https://brainly.com/question/5385952
#SPJ1
What is the output?
numB = 25
while numB > 13:
numB = numB - 5
print(numB)
Output:
Answers
Answer:
The answer is 10
Explanation:
i got it right on the assignment
Answer: 10
Explanation: got it right on edgen
literature of climate change
Answers
The complete question may be like , Describe the literature on climate change and its impact on the environment and human society.
The literature on climate change and its impact on the environment and human society is extensive and diverse. Researchers, scientists, and scholars from various disciplines have contributed to understanding the causes, consequences, and potential solutions to climate change.
Scientific literature on climate change provides evidence of the warming trend in global temperatures and attributes it primarily to human activities, particularly the burning of fossil fuels and deforestation. This literature includes studies on the greenhouse effect, rising sea levels, melting glaciers, and changes in precipitation patterns.
The impacts of climate change on the environment are well-documented in the literature. It highlights the loss of biodiversity, increased frequency and intensity of extreme weather events such as hurricanes and heatwaves, shifts in ecosystems and species distributions, and disruptions to natural habitats. Additionally, studies explore the potential consequences of climate change on agriculture, water resources, and coastal areas.
Literature also delves into the social and economic implications of climate change. It examines the disproportionate effects on vulnerable populations, including low-income communities and developing countries. The literature explores the linkages between climate change and public health, migration, social inequality, and food security. Moreover, economic analyses assess the costs of climate change mitigation and adaptation strategies.
The literature on climate change also covers policy frameworks and international agreements aimed at addressing the issue. It explores mitigation measures such as transitioning to renewable energy sources, enhancing energy efficiency, and reducing greenhouse gas emissions. Adaptation strategies, including building resilience, developing climate change adaptation plans, and implementing sustainable practices, are also discussed.
In summary, the literature on climate change encompasses a wide range of topics, including scientific research, environmental impacts, social consequences, economic analyses, and policy considerations.
It provides a comprehensive understanding of the challenges posed by climate change and offers insights into mitigating its effects and fostering a sustainable future.
For more questions on climate
https://brainly.com/question/17922964
#SPJ11
TRUE OR FALSE: COMPUTER SCIENCE!
Computer Software consists of system software and
application software.
True
False
Answers
Answer:true
Explanation:
Answer:
false it is not true.
it is different on its own
An array is a fixed-size container which stores a collection of values of the same type.
a. True
b. False
Answers
In which of the following situations must you stop for a school bus with flashing red lights?
None of the choices are correct.
on a highway that is divided into two separate roadways if you are on the SAME roadway as the school bus
you never have to stop for a school bus as long as you slow down and proceed with caution until you have completely passed it
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school bus
Answers
The correct answer is:
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school busWhat happens when a school bus is flashing red lightsWhen a school bus has its flashing red lights activated and the stop sign extended, it is indicating that students are either boarding or exiting the bus. In most jurisdictions, drivers are required to stop when they are on the opposite side of a divided highway from the school bus. This is to ensure the safety of the students crossing the road.
It is crucial to follow the specific laws and regulations of your local jurisdiction regarding school bus safety, as they may vary.
Learn more about school bus at
https://brainly.com/question/30615345
#SPJ1
Given three subroutines of 550, 290, and 600 words each, if segmentation is used then the total memory needed is the sum of the three sizes (if all three routines are loaded). However, if paging is used, then some storage space is lost because subroutines rarely fill the last page completely, and that results in internal fragmentation. Determine the total amount of wasted memory due to internal fragmentation when the three subroutines are loaded into memory using each of the following page sizes:
a. 100 words
b. 600 words
c. 700 words
d. 900 words
Answers
Typically, external fragmentation wastes one-third of memory. Internal fragmentation occurs when space inside a designated region is wasted. Thus, option D is correct.
What wasted memory due to internal fragmentation?The mounted-sized block is allotted to a method whenever a request for memory is made. Internal fragmentation is the term used to describe the situation where the memory allotted to the method is a little bigger than the amount requested.
Normally, memory is allocated in uniformly sized blocks, but sometimes a process doesn't use the entire block, leading to internal fragmentation.
Memory fragmentation occurs when a memory allocation request can be satisfied by the whole amount of accessible space in a memory heap, but no single fragment (or group of contiguous fragments) can.
Therefore, when the three subroutines are loaded into memory using each of the following page sizes 900 words.
Learn more about memory here:
https://brainly.com/question/16953854
#SPJ5
Effects of disregarding to ignoring computer problems
Answers
-It can cause damage to essential computer hardware.
-It can also lead to electric shock circuit that may cause fire.
-Loss of information and data.

the study of sound and sound wave is called
Answers
Answer: Acoustics
Explanation:
Acoustics is simply refered to as a branch in physics that studies sound and its wave.
Acoustics studies mechanical waves in liquid, solid state or gaseous state. Topics such as infrasound, vibration and ultrasound are studied. Someone who works in the acoustics field is referred to as an acoustician.
In MIPS, all operation codes (op-codes) use ______ only.
A- 5 bits
B- 8 bits
C- 6 bits
D -32 bits
Answers
Answer:
5 bits
Explanation:
ue82ijevw8ey जभछतड।णृबदजठणब
11. Which one of the following buttons is used for paragraph alignment?

Answers
Answer:
C
Explanation:
Option A is used for line spacing.
Option B is used for right indent.
Option C is used for right paragraph alignment.
Option D is used for bullet points.
The button used for paragraph alignment would be option C.
The is context sensitive, meaning it will display options that relate to an active tool.
Answers
Answer:
Option bar
Explanation:
The Options Bar seems to be the parallel bar in photo editing software that operates under it's main menu. You will use the Software panel to turn it on and off, but if you're not seeing it on your phone, you probably want Software > Settings to power it on. The role of the Options Bar is to customize the tool settings when you're about to use.
Answer:
(A) The ribbon
Explanation:
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
The acquisition of knowledge is learning true or false
Answers
Answer:
True
Explanation:
What function is used to draw a line in the frame?
Fill in the blank:
NOTE:it is not DrawLine
phyton
Answers
Answer:
The function used to draw a line in a frame in python is the "line()" function.
Example:
from tkinter import *
root = Tk()
canvas = Canvas(root, width = 300, height = 300)
canvas.pack()
line = canvas.create_line(0, 0, 300, 300)
root.mainloop()
Fill in the blank:
line = canvas.create_ ________(0, 0, 300, 300)
The blank should be filled with a line.
Explanation:
PLEASE ANYONE HELP ME. PLEASE I BEG OF YOU.
Give an illustration of the agile model in game development.
Answers
The illustration of the Agile Model in Game Development is expressed below. With it, game developers can efficiently manage risks, respond to player preferences and deliver a high-quality game that meets market demand.
How does the Agile Model contribute to game development?The Agile Model as commonly used in game development, is characterized by its iterative and flexible approach. It focuses on delivering frequent increments of playable content and incorporating feedback throughout the development process.
The Game development teams using Agile work in short sprints typically use two to four weeks long where they plan, develop, test and release small portions of the game. This allows for continuous improvement, adaptability to changes and collaboration between developers, designers, and stakeholders.
Read more about agile model
brainly.com/question/30126132
#SPJ1
Does modern technology make our lives better,worse ,or doesn’t really make a change in your life ?Whats your opinion ?
Answers
How does Accenture work to build trust in Artificial Intelligence (AI)?
Answers
https://brainly.in/question/35275070
Accenture work to build trust in Artificial Intelligence (AI) through investing in differentiated intellectual property.
What is a differentiated intellectual property?Intellectual property serves as a creations of the mind as well as inventions that is bee used in commerce.
With the creation of this differentiated intellectual property, it help the Accenture to be able to establish trust because there is a law that protect any intellectual property in the the country.
Read more on intellectual property here: https://brainly.com/question/1078532
#SPJ2
ctu how to read values into a list
Answers
To read values into a list, you can follow these general steps:
1. Create an empty list to store the values.
2. Determine the source of the values, such as user input, a file, or an external data stream.
3. Use appropriate methods or functions to fetch the values from the source. For example, if reading from user input, you can use the input() function to prompt the user for values.
4. Assign the fetched value to a variable.
5. Append or add the value to the list using the list's append() or extend() method.
6. Repeat steps 3 to 5 as needed, depending on the number of values you want to read.
7. Once all the values have been read and added to the list, you can perform further operations or manipulations on the list as required.
Remember to handle any necessary error-checking and validation to ensure that the values being read are of the expected type or format. By following these steps, you can successfully read values into a list in a general way, regardless of the specific programming language or context you are working with.
For more questions on Append, click on:
https://brainly.com/question/31788450
#SPJ8
Example of mediated communication and social media
Answers
Answer: mediated communication: instant messages
social media: social platforms
Explanation:
