Which best describes the arts, A/V technology, and communication cluster?
careers that are focused on performing for and communicating with others
careers that combine technologies to make video recordings possible
careers that report information to the public
careers that allow people to express themselves through art
please hurry its timed thank you
Answers
Answer:
A. Careers that are focused on performing for and communicating with others.
Explanation:
The best description of the arts, A/V technology, and communication cluster is careers that are focused on performing for and communicating with others. The correct option is A.
What is a communication cluster?Using Fiber Channel and SAS adapters, traditional networking interfaces like IP-based networks and storage interface communication are used for cluster communication.
The following four professional paths make up the information technology cluster: interactive media, network systems, programming, and software development. Information support and services are also included.
A pool of high-performance computing (HPC), GPU, or optimized instances connected by a high-bandwidth, ultra-low-latency network is referred to as a cluster network.
Therefore, the correct option is A. careers that are focused on performing for and communicating with others.
To learn more about communication clusters, refer to the link:
https://brainly.com/question/28716835
#SPJ6
Related Questions
full form of http.
wrong answer will be reported
Answers
Answer:
The full form of HTTP is Hypertext Transfer Protocol.
Explanation:
It is an application protocol.It is used for data communication.It is used for transferring hypertext documents on the World Wide Web.URGENT! REALLY URGENT! I NEED HELP CREATING A JAVASCRIPT GRAPHICS CODE THAT FULFILLS ALL THESE REQUIREMENTS!

Answers
In the program for the game, we have a garden scene represented by a green background and a black rectangular border. The cartoon character is a yellow circle with two black eyes, a smiling face, and arcs for the body. The character is drawn in the center of the screen.
How to explain the informationThe game uses Pygame library to handle the graphics and game loop. The garden is drawn using the draw_garden function, and the cartoon character is drawn using the draw_cartoon_character function.
The game loop continuously updates the scene by redrawing the garden and the cartoon character. It also handles user input events and ensures a smooth frame rate. The game exits when the user closes the window.
This example includes appropriate use of variables, a function definition (draw_garden and draw_cartoon_character), and a loop (the main game loop). Additionally, it meets the requirement of using the entire width and height of the canvas, uses a background based on the screen size, and includes shapes (circles, rectangles, arcs) that are used appropriately in the context of the game.
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
You may need to use the appropriate appendix table or technology to answer this question.
Advertisers contract with internet service providers and search engines to place ads on websites. They pay a fee based on the number of potential customers who click on their ad. Unfortunately, click fraud—the practice of someone clicking on an ad solely for the purpose of driving up advertising revenue—has become a problem. Businessweek reports that 40 percent of advertisers claim they have been a victim of click fraud. Suppose a simple random sample of 360 advertisers will be taken to learn more about how they are affected by this practice. (Round your answers to four decimal places.)
(a)What is the probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud?
(b)What is the probability that the sample proportion will be greater than 0.45?
Answers
To find the probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud, we need to calculate the margin of error.
The margin of error is given by the formula:
Margin of Error = z * sqrt((p * (1-p)) / n)
Where:
- z is the z-score corresponding to the desired level of confidence (typically 1.96 for a 95% confidence level)
- p is the estimated population proportion experiencing click fraud (0.40 in this case)
- n is the sample size (360 in this case)
Calculating the margin of error:
Margin of Error = 1.96 * sqrt((0.40 * (1-0.40)) / 360)
Margin of Error ≈ 0.0359
The probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud can be calculated as the sum of the probabilities within the range p ± margin of error.
P(p - 0.04 ≤ sample proportion ≤ p + 0.04) = P(p - 0.04 ≤ sample proportion) - P(p + 0.04 < sample proportion)
Using the standard normal distribution, we can calculate these probabilities.
P(p - 0.04 ≤ sample proportion) = P(z ≤ (sample proportion - p) / sqrt((p * (1-p)) / n))
P(p + 0.04 < sample proportion) = P(z ≤ (sample proportion - p) / sqrt((p * (1-p)) / n))
We use the z-score formula to convert the sample proportion into a standard normal distribution.
To know more about sample proportion visit :-
https://brainly.com/question/11461187
#SPJ11
----------------------------
Please summarize into 1.5 pages only
----------------------------
Virtualization
Type 2 Hypervisors
"Hosted" Approach
A hypervisor is software that creates and runs VM ins
Answers
Virtualization: It is a strategy of creating several instances of operating systems or applications that execute on a single computer or server. Virtualization employs software to reproduce physical hardware and create virtual versions of computers, servers, storage, and network devices. As a result, these virtual resources can operate independently or concurrently.
Type 2 Hypervisors: Type 2 hypervisors are hosted hypervisors that are installed on top of a pre-existing host operating system. Because of their operation, Type 2 hypervisors are often referred to as "hosted" hypervisors. Type 2 hypervisors offer a simple method of getting started with virtualization. However, Type 2 hypervisors have some limitations, like the fact that they are entirely reliant on the host operating system's performance.
"Hosted" Approach: The hosted approach entails installing a hypervisor on top of a host operating system. This hypervisor uses hardware emulation to create a completely functional computer environment on which several operating systems and applications can run concurrently. In general, the hosted approach is used for client-side virtualization. This method is easy to use and is especially useful for the creation of virtual desktops or the ability to run many operating systems on a single computer.
A hypervisor is software that creates and runs VM instances: A hypervisor, also known as a virtual machine manager, is software that creates and manages virtual machines (VMs). The hypervisor allows several VMs to execute on a single physical computer, which means that the computer's hardware can be utilized more efficiently. The hypervisor's role is to manage VM access to physical resources such as CPU, memory, and I/O devices, as well as to provide VM isolation.
Know more about virtualization, here:
https://brainly.com/question/31257788
#SPJ11
As you create the slides, miniature views of the individual slides are displayed in the Notes pane.
Answers
Answer:
False.
Explanation:
PowerPoint application can be defined as a software application or program designed and developed by Microsoft, to avail users the ability to create various slides containing textual and multimedia informations that can be used during a presentation.
Some of the features available on Microsoft PowerPoint are narrations, transition effects, custom slideshows, animation effects, formatting options etc.
Basically, the views that are available on the Microsoft PowerPoint application includes;
1. Slide Sorter.
2. Notes Page.
3. Reading Pane.
4. Presenter view.
Slide transition is an inbuilt feature of a presentation software that automatically changes the slides at regular intervals.
As a user create slides, miniature views of the individual slides, referred to as thumbnails are displayed in the Slide Tab or Thumbnail pane.
On the other hand, the Notes pane is typically designed for typing remarks or notes that the presenter could share with the audience during a presentation.
how was the background for the revolution of 2007 prepared
Answers
Answer:
Answer is in the attachment.
Hope this helps..
When computing complexity, long running operations that occur infrequently may be
A. amortized
B. make the complexity non-linear.
C. made available to static members
D. ignored
E. None of the above.
Answers
A. amortized. When computing complexity, long-running operations that occur infrequently may be amortized, meaning that their cost is spread out over multiple operations to reduce their impact on overall complexity.
It's crucial to consider both frequently occurring operations and less frequently occurring ones when calculating an algorithm's complexity.
An algorithm's overall performance can be significantly impacted by long-running actions that happen infrequently.
Ignoring these processes could result in an erroneous complexity estimation.
An amortized analysis is a method for examining how well algorithms function when they occasionally perform expensive actions.
The cost of the operations is averaged across a series of executions, taking into consideration both frequent and rare operations.
By taking into account both the frequent and infrequent actions, we are able to better comprehend the algorithm's overall performance.
Making the operation accessible to static members or making the complexity non-linear may not be enough to solve the problem of rare, lengthy operations.
On the other hand, amortized analysis can assist in offering a more accurate evaluation of the algorithm's overall performance and complexity.
Learn more about the amortized analysis :
https://brainly.com/question/31479691
#SPJ11
pls answer i need to turn it in today!!
In computing flowcharts how are decisions represented?
What is the command used most for decisions?
Answers
Answer:
See Explanation
Explanation:
How decisions are represented?
In flowcharts, decisions are represented using diamond shapes (see attachment)
Decisions could be conditional statement or repetition operations which may have the form of loops or iterations.
Either of theses are represented using the diamond shapes.
Take for instance:
To check if a is greater than b... Simply write if a > b i the diamond box
Command used for most decisions
Most decisions are conditional statements; hence, the if command is often used for decisions.

what line do you start with to show that what follows after that line consists of html tags
Answers
The main answer in one line is: The DOCTYPE declaration signals that the following content consists of HTML tags.
What line signifies that the content following it consists of HTML tags?To indicate that what follows after a specific line consists of HTML tags, you typically start with the DOCTYPE declaration, which defines the version of HTML being used.
The line that indicates the following content consists of HTML tags is the DOCTYPE declaration.
It is usually the first line in an HTML document and specifies the HTML version being used.
The DOCTYPE declaration helps the browser interpret and render the HTML correctly by indicating the specific set of rules and standards to follow.
For example, a commonly used DOCTYPE declaration for HTML5 is `<!DOCTYPE html>`.
Learn more about declaration signals
brainly.com/question/30122799
#SPJ11
have you gone/done into things that you forget to close/settle?
Answers
Answer: AT SOME CIRCUMSTANCES YES
Explanation: WELL ONE EXAMPLE WAS OUR GAMING GROUP WHICH WAS MADE OF ABOUT 2 YEARS AGO AND THERE ARE STILL TO PEOPLE IN THE GROUP WHEN WE DON'T EVEN USE ANYMORE , CAN YOU BELIEVE IT ?
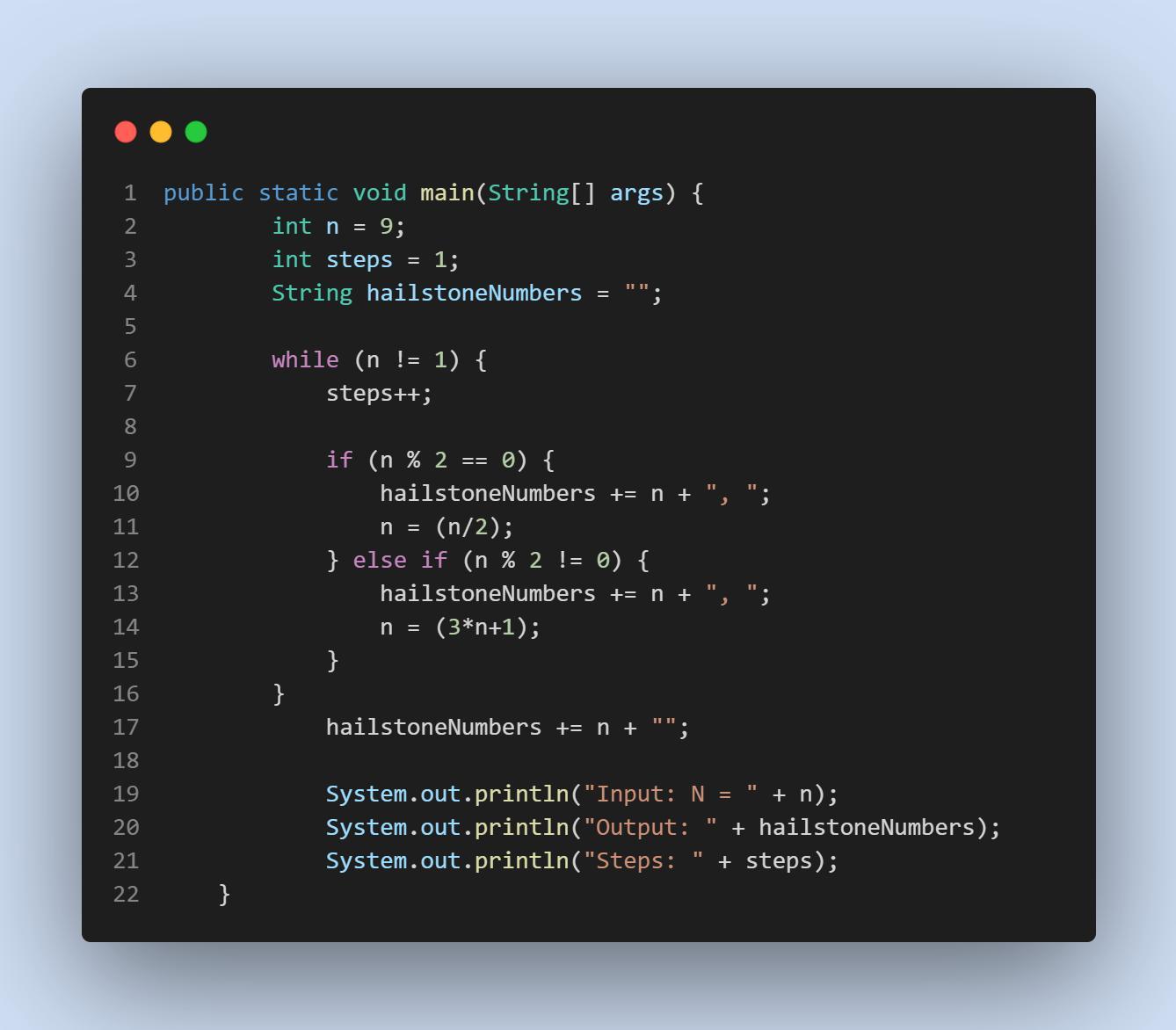
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
Explain the advantages and disadvantages of forwarding an email.
Answers
Save Time. Another advantage is that these services help save your employees time. ...
Avoid Missing Important Emails.
Email forwarding won't work if you have a mail product set up on the domain name. Mail for your domain name can only be sent to one place. ...
Forwarding does not allow you to customize spam settings. ...
Forwarding will only deliver attachments up to 10MB. ...
Wildcard forwarding is not supported.
Which contributions did johannes kepler make? select three options. he revived aristotle’s model of the solar system. he solved ptolemy’s model by proving elliptical orbits. he proved galileo’s calculations were incorrect. he determined that planets move faster when closer to the sun. he discovered laws of planetary motion.
Answers
Answer:
2
4
5
Explanation:
Kepler's laws of planetary motion are rules that describe how the planets move within the solar system in astronomy and classical physics.
What is Planetary motion?The astronomer Tycho Brahe made observations in the 16th century, and these observations were analyzed by the German astronomer Johannes Kepler, who announced his first two laws in 1609 and a third rule nearly ten years later, in 1618.
Kepler never assigned a number to these rules or made a clear distinction between them and his other discoveries.
According to Newton, the motion of bodies subject to central gravitational force need not always follow the elliptical orbits specified by Kepler's first law but can also follow paths defined by other, open conic curves.
Therefore, Kepler's laws of planetary motion are rules that describe how the planets move within the solar system in astronomy and classical physics.
To learn more about Planetary motion, refer to the link:
https://brainly.com/question/3488967
#SPJ5
Which of these code snippets is the most readable, according to the JavaScript coding style conventions that we recommend here?
Choose 1 answer:
Choose 1 answer:
(Choice A) var addUp = function(a, b) {
var c = a + b;
return c;
};
A
var addUp = function(a, b) {
var c = a + b;
return c;
};
(Choice B) var addUp = function(a, b) {
var c = a + b;
return c;
};
B
var addUp = function(a, b) {
var c = a + b;
return c;
};
(Choice C) var addUp = function(a, b) { var c = a + b; return c; };
C
var addUp = function(a, b) { var c = a + b; return c; };
Answers
Your answer: Choice A All the given code snippets have the same function, which adds two numbers and returns the result. However, the readability of the code is what makes a difference.
Choice A is the most readable because it follows proper JavaScript coding style conventions, such as:
1. Using a descriptive variable name: "addUp" clearly indicates the purpose of the function.
2. Proper indentation: Each line in the function has a consistent and logical level of indentation, making the code easy to read and understand.
3. Line breaks: Each statement in the function is on a separate line, which helps to visually separate different parts of the code and makes it easier to read.
Choices B and C are identical to Choice A, but Choice C has everything on a single line, which makes it harder to read and understand at a glance. Therefore, Choice A is the most readable option according to JavaScript coding style conventions.
Learn more about snippets here:
https://brainly.com/question/3232885
#SPJ11
jerome is working on a hardware problem with his computer. he has determined that the problem is with either the video card or the hdmi cable connecting the video card to the monitor. jerome has both an hdmi cable and a video card that he can use to fix the problem. what would be the problem with jerome replacing the video card first?
Answers
If Jerome replaces the video card first without testing the HDMI cable, he may still have the same problem even with a new video card. The issue could be with the HDMI cable itself, and replacing the video card would not solve the problem. This would result in a waste of time and money. It is always best to troubleshoot and isolate the problem before replacing any hardware component.
.Learn more about hardware here:
brainly.com/question/32073195
#SPJ11
Abby wants a high-end computer system for her home office that can be upgraded. Which of the following should she choose?
Laptop
Gaming Console
Desktop
Server

Answers
Describe, with examples, the way in which a defect in software can cause harm to a person, to the environment, or to a company
Answers
Answer:
Losing jobs. Fire. Destruction of property.
Explanation:
Having a company shut down due to lack of protection and having people testify products unsafe. If software blows up it could cause desturction of property therefore causing the effect of many people losing their jobs.
For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


What are three ways that media access control is used in networking? (Choose three. )
a) Networks with controlled access have reduced performance due to data collisions.
b) 802. 11 utilizes CSMA/CD.
c) Media access control provides placement of data frames onto the media.
d) Data link layer protocols define the rules for access to different media.
e) Ethernet utilizes CSMA/CD.
f) Contention-based access is also known as deterministic
Answers
The three ways that media access control is used in networking are c) Media access control provides placement of data frames onto the media.
Media access control (MAC) is responsible for determining when and how data frames are transmitted onto the media. It establishes rules and protocols for accessing the media, ensuring that multiple devices can share the same medium efficiently and avoid data collisions.
d) Data link layer protocols define the rules for access to different media.
Data link layer protocols, such as Ethernet, Token Ring, or Wi-Fi (802.11), define specific rules and mechanisms for accessing different types of media. These protocols outline how devices contend for access, handle collisions, and ensure efficient transmission over the media.
e) Ethernet utilizes CSMA/CD.
Ethernet, a widely used networking technology, employs the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) method. CSMA/CD is a contention-based access mechanism where devices listen for carrier signals on the network and transmit data only when the medium is clear. If a collision occurs, CSMA/CD detects it and initiates a retransmission process to avoid data loss.
It's important to note that options a) and f) are incorrect. Option a) suggests that networks with controlled access have reduced performance due to data collisions, which is not accurate. Controlled access mechanisms, such as reservation-based protocols, can actually enhance performance by minimizing collisions. Option f) is incorrect because contention-based access refers to access methods where devices contend for access without predetermined rules or schedules, and it is not synonymous with deterministic access.
Learn more about data frames here
https://brainly.com/question/29928884
#SPJ11
Enrique, a web developer, is creating a new website for a customer and is using Ruby to provide dynamic content for the web
pages. Which language type is he using?
Scripting
Compiled
Assembly
Machine
Answers
The development of the web pages for the website with the Ruby language is using scripting.
What is Ruby?Ruby is the computer programming language and is used for the development of websites, software, and other applications with simple syntax.
The development of the website by Enrique is based on the formation of the syntax with the works that form the running of the application. He has been using scripting for the development of web pages. Thus, option A is correct.
Learn more about the Ruby language, here:
https://brainly.com/question/9966767
#SPJ1
Sean wants to build a robot. What part of the robot will he need to include that enables the robot to process sensory information?
Answers
To enable a robot to process sensory information, Sean will need to include a sensor system as part of the robot. The sensor system will provide input to the robot's central processing unit (CPU) or microcontroller, allowing it to perceive and respond to its environment. The specific sensors needed will depend on the robot's intended function and the type of sensory information it needs to process. Common sensors used in robots include cameras, microphones, touch sensors, and proximity sensors.
#SPJ1
Sam is a Windows system administrator responsible for setting up client workstations for different departments. After installing the operating system, Sam manually disables certain programs that aren't needed by that department. Recently, Sam learned a few workstations had been compromised. The security analyst suggests that the disabled applications may have been the target. Going forward, what should Sam change in his process
Answers
Answer:
not disable any programs after installing a new operating system
Explanation:
Sam should simply not disable any programs after installing a new operating system. If the system is working as intended then he should leave it be, as the saying says "Don't fix what isn't broken". When a new operating system is installed, the entire system is usually wiped, meaning that the only programs installed have been installed as defaults by the operating system. Usually, this is for a reason and acts as security measures for the user, the system, and all of the data. Most of these programs interact with each other and work off of each other's data. Removing them from the system can prevent other very important functions of the operating system from performing their duties, which in term can compromise the entire security of the system. Therefore, the best thing to do would be to not remove these default programs.
What can you do on Forms?
Create a Survey
Create a Quiz
Make a permission slip
All of the above
Answers
Answer:
I believe the answer is "all of the above"
Explanation:
why is computer called an information processing device ?
Answers
Since, the computer accepts raw data as input and converts into information by means of data processing, it is called information processing machine (IPM).
Computer is called information processing machine because it gives you meaningful information after processing raw data......
List three ideas for checking in with your progress and recognizing completion on your actions.
Answers
One idea for checking in with your progress and recognizing completion on your action is to set specific milestones or targets along the way and regularly evaluate your progress towards them.
How can you effectively track your progress and acknowledge completion of your action?To effectively track your progress and acknowledge completion of your action, it is important to establish clear milestones or targets that can serve as checkpoints. Break down your overall goal into smaller, measurable objectives that can be achieved incrementally.
Regularly assess your progress by comparing your actual achievements against these milestones. This will provide you with a tangible way to track your advancement and ensure that you stay on track. Once you reach a milestone or successfully complete a specific objective, take the time to acknowledge and celebrate your achievement.
Read more about action check
brainly.com/question/30698367
#SPJ1
9.6 Code practice Edhesive

Answers
Answer:
N = [1,1,1,1,1],
[2,2,2,2,2],
[3,3,3,3,3],
[4,4,4,4,4]
def printIt(ar):
for row in range(len(ar)):
for col in range(len(ar[0])):
print(ar[row][col], end=" ")
print("")
N=[]
for r in range(4):
N.append([])
for r in range(len(N)):
value=1
for c in range(5):
N[r].append(value)
value=value + 1
printIt(N)
print("")
newValue=1
for r in range (len(N)):
for c in range(len(N[0])):
N[r][c] = newValue
newValue = newValue + 1
printIt(N)
Explanation:
I got 100%.
In this exercise we have to use the knowledge of computational language in python to write the code.
We have the code in the attached image.
The code in python can be found as:
def printIt(ar):
for row in range(len(ar)):
for col in range(len(ar[0])):
print(ar[row][col], end=" ")
print("")
N = [1,1,1,1,1], [2,2,2,2,2], [3,3,3,3,3], [4,4,4,4,4]
for r in range(4):
N.append([])
for r in range(len(N)):
value=1
for c in range(5):
N[r].append(value)
value=value + 1
printIt(N)
print("")
newValue=1
for r in range (len(N)):
for c in range(len(N[0])):
N[r][c] = newValue
newValue = newValue + 1
printIt(N)
See more about python at brainly.com/question/26104476

What is the output?
>>> password = "sdf345"
>>> password.isalpha()
>>>
Answers
Answer:
The answer is false
Explanation:
The string isalpha() returns True if all the characters are letters and the string has at least one character.
Answer:
False
Explanation:

An algorithm is a guiding rule used to solve problems or make decisions. Please select the best answer from the choices provided T F
Answers
True. An algorithm can be defined as a step-by-step procedure or a set of rules designed to solve a specific problem or perform a particular task.
It serves as a guiding rule for problem-solving or decision-making processes. Algorithms are used in various fields, including computer science, mathematics, and even everyday life.
In computer science, algorithms are fundamental to programming and software development. They provide a systematic approach to solving complex problems by breaking them down into smaller, manageable steps.
Algorithms can range from simple and straightforward to highly complex, depending on the nature of the problem they aim to solve.
The importance of algorithms lies in their ability to provide a structured and efficient solution to a given problem. They help in achieving consistency, accuracy, and reproducibility in decision-making processes. Additionally, algorithms enable automation and optimization, allowing for faster and more reliable problem-solving.
It is essential to acknowledge and respect the originality and intellectual property of others when using algorithms developed by someone else. Proper citation and avoiding plagiarism are crucial to ensure the integrity of one's work and uphold ethical standards.
For more such questions on algorithm,click on
https://brainly.com/question/29927475
#SPJ8
When using ________ access, access to the data starts at the beginning of the file and proceeds through all the records to the end of the file.
Answers
When using sequential access, access to the data starts at the beginning of the file and proceeds through all the records to the end of the file.
Do any of you guys know what the main problem in E.T is?
Answers
Answer:
At its glowing red heart, E.T. is a film about friendship. Elliott and E.T. are a tightknit pair from wildly different backgrounds, and their bond is grounded in love, loyalty, compassion, teamwork, and even a mysterious cosmic connection.