True or false? When migration is done from the firewall of another vendor to a Palo Alto Networks firewall, a best practice is to always migrate the existing Security policy.
Answers
True. When migrating from the firewall of another vendor to a Palo Alto Networks firewall, it is a best practice to always migrate the existing Security policy to ensure a smooth transition and maintain the security posture of the network.
It is generally recommended to migrate the existing security policy when migrating from the firewall of another vendor to a Palo Alto Networks firewall. However, this recommendation is not a hard and fast rule and there may be instances where it is not the best approach. It is important to evaluate the existing security policy and assess whether it is suitable for the new environment and the capabilities of the Palo Alto Networks firewall. Additionally, it may be necessary to modify or update the security policy to align with the organization's security objectives and best practices. Ultimately, the decision to migrate the existing security policy should be based on a thorough analysis of the current and future security requirements, as well as the capabilities of the Palo Alto Networks firewall.Thus when migrating from the firewall of another vendor to a Palo Alto Networks firewall, it is a best practice to always migrate the existing Security policy to ensure a smooth transition and maintain the security posture of the network is a correct statement.Know more about the Palo Alto Networks
https://brainly.com/question/28447433
#SPJ11
Related Questions
You will be given a list of tuples where each tuple indicates a point i.e. (x, y) in a 2-dimensional coordinate system. you need to write a python program to find the minimum distance and the point that is closest to the origin i.e. (0,0)
Answers
The math. dist() method calculates the Euclidean distance between two points (p and q), where p and q are the point's coordinates.
It should be noted that the two points (p and q) must have the same dimensions.
A distance formula is a formula used to calculate the distance between two places. These points might be of any size. You might want to find the distance between two points on a line (1d), two points on a plane (2d), or two points in space (3d) (3d). The distances between two places in terms of their coordinates are given by an algebraic formula (see coordinate system). The distance formulas for points in rectangular coordinates in two- and three-dimensional Euclidean space are based on the Pythagorean theorem.
Learn more about system here-
https://brainly.com/question/14253652
#SPJ4
Most presentations use text: A. To draw attention to content
B. At a minimum
C. Without restraint
D. To maximize area and style
Answers
(True/False) Like function ‘fork’ in the process API, function ‘pthread_create’ creates a clone of the current thread.
Answers
False. Function 'pthread_create' does not create a clone of the current thread.
In the process API, the 'fork' function creates a new process by duplicating the existing process, including its memory and resources. However, in the pthreads library, the 'pthread_create' function is used to create a new thread within the same process, rather than creating a separate clone of the current thread.
When 'pthread_create' is called, a new thread is created and starts executing the specified thread function. This allows concurrent execution of multiple threads within the same process, sharing the same memory and resources. Each thread has its own stack and thread-specific data, but they all have access to the same global and heap memory.
Unlike 'fork', which creates a separate process, 'pthread_create' creates a new thread within the same process, allowing for parallel execution of tasks. This makes it useful for implementing multithreaded applications where multiple threads can work on different parts of a task simultaneously, improving performance and resource utilization.
learn more about 'pthread_create' here:
https://brainly.com/question/28901733
#SPJ11
100 Points!
Think of a problem in society that could use data to help solve it. Answer the following questions in at least 1 paragraph (5-7 sentences).
What is the problem?
What data would you need to collect in order to gather more information to help solve this problem?
How would you collect this data?
How would the use of a computer help to solve this problem ? (make sure you explain in depth here).
Answers
Answer:
Attached in img below, didn't lke my answer for some reason.

Make each word to its correct meaning baiting click-jacking cross-site scripting
Answers
Answer:
Explanation:
Sure! Here are the correct meanings for the given terms:
1. Baiting: Baiting refers to the act of enticing or luring someone into a trap or a specific action, often through deception or manipulation.
2. Click-jacking: Click-jacking is a technique used by malicious actors to trick users into clicking on a seemingly innocent element or link on a webpage, which actually performs a hidden action or leads the user to unintended destinations. It is designed to deceive and hijack the user's clicks for nefarious purposes.
3. Cross-site scripting: Cross-site scripting (XSS) is a security vulnerability that occurs when an attacker injects malicious scripts into a trusted website or web application. When other users visit the affected site, the injected scripts can execute on their browsers, potentially allowing the attacker to steal sensitive information, perform unauthorized actions, or manipulate the website's content.
I hope this clarifies the meanings of the terms "baiting," "click-jacking," and "cross-site scripting" for you.
What happens when a switch receives a frame with a destination MAC address of FF FF FF FF FF FF?
Answers
When a switch receives a frame with a destination MAC address of FF FF FF FF FF FF, it broadcasts the frame out to all ports on the switch, except for the port that the frame was received on.
This is known as a broadcast frame. Broadcast frames are used by network devices to send information to all devices on a network. They are typically used by network protocols such as Address Resolution Protocol (ARP) and Dynamic Host Configuration Protocol (DHCP) to discover and communicate with other devices on the network.
Broadcast frames are also used by network switches to learn which devices are connected to which ports. When a switch receives a broadcast frame, it updates its MAC address table to associate the source MAC address of the frame with the port that it was received on.
To know more about destination visit:
brainly.com/question/30074835
#SPJ11
In Java:
Assume the availability of an existing class, ICalculator, that models an integer arithmetic calculator and contains:
a private instance variable currentValue that stores the current int value of the calculator
a getter method for the above instance variable
methods add, sub, mul, and div
Each method in ICalculator receives an int argument and applies its operation to currentValueand returns the new value of currentValue. So, if currentValue has the value 8 and sub(6) is invoked then currentValue ends up with the value 2, and 2 is returned.
Write a public subclass, ICalculator1, based on ICalculator. The class ICalculator1 has one additional method, sign, that receives no arguments, and doesn't modify currentValue. Instead, it simply returns 1, 0 or -1 depending on whether currentValue is positive, zero, or negative respectively.
Answers
Answer:
A subclass?
Explanation:
A public subclass for ICalculator1 has one additional method, sign, that receives no arguments, and doesn't modify current Value. Instead, it simply returns 1, 0 or -1 depending on whether current Value is positive, zero, or negative respectively.
What is public subclass?A member's access is declared to be public with the Java keyword public. All other classes can see members of the public class. This implies that a public field or method can be accessed by any other class. In addition, public fields can be changed by other public subclass or classes unless they are marked as final.
Further a subclass is defined as a class that is descended from another class (also a derived class, extended class, or child class). A superclass is the class from which a subclass is descended (also a base class or a parent class).
A public subclass for ICalculator1 has one additional method, sign, that receives no arguments, and doesn't modify current Value:
In Java,
public class ICalculator1 extends ICalculator {
public int sign() {
if (getCurrentValue() > 0)
return 1;
else if (getCurrentValue() == 0)
return 0;
else
return -1;
}
}
Therefore the availability of an existing class, I-Calculator, that models an integer arithmetic calculator, above public subclass has been made.
Learn more about public subclass:
https://brainly.com/question/15992142
#SPJ12
How should a team have quality built into its deliverables?
Answers
Answer:
According to the question, the answer is option "A) By having a separate quality assurance team for testing the quality of deliverables". The reason for this answer is because there are many things regarding quality assurance should be taken care of, in order to make the product deliverable to customers.6 May 2019
Supply Chain strategy often optimizes supply chain networks for "average" performance. Explain why this is or is not the right approach? Edit View Insert Format Tools Table 12pt Paragraph BIU AQV T²V : When locating facilities in a network, the transportation economies about the potential facility location should be considered. What does this mean with respect to where the facility is located and how the network is configured? Edit View Insert Format Tools Table 12pt Paragraph ✓ B I U AV 2V T²V ⠀
Answers
Supply Chain strategy is essential in every organization that involves the planning and management of all activities involved in sourcing, procurement, conversion, and logistics. In doing so, the goal is to optimize supply chain networks for average performance.
It is the right approach to optimize supply chain networks for "average" performance because it helps the company attain its objectives and improve its performance. It makes the planning and management of activities in sourcing, procurement, conversion, and logistics more efficient by making use of resources at an optimal level. Also, this approach allows the company to maintain the right balance between supply and demand by producing enough products to meet the customers' demands. By doing so, the company reduces costs, increases efficiency, and enhances customer satisfaction. However, sometimes, optimizing supply chain networks for "average" performance may not be the right approach. This is because customers' preferences are not average. Also, different customers have different needs. Thus, optimizing the supply chain for an average performance level may result in dissatisfied customers who may opt to seek services from the competitors. Thus, it is essential to ensure that the optimization strategy considers the customers' needs and preferences, and a balance is achieved. In conclusion, optimizing the supply chain for average performance is the right approach in most cases. However, this approach should consider the customers' needs and preferences to achieve a balance between supply and demand. Therefore, when locating facilities in a network, transportation economies about the potential facility location should be considered. This means that the facility should be located in an area that is easily accessible to transportation. Additionally, the network should be configured in such a way that the facility is linked to other facilities in the supply chain network to allow for efficient transportation.
To learn more about Supply Chain strategy, visit:
https://brainly.com/question/27670727
#SPJ11
give another term for searching data in database
Answers
Answer:
wmeme
Explanation:
kmemeemsjsjsjnssnnssnsnsnsns
which of the following is an exit controlled loop? a) while loop. b) for loop. c) do-while loop. d) none of the above.
Answers
The correct answer is c) do-while loop. A do-while loop is an exit controlled loop, which means the condition is checked after the loop body executes.
This is different from a while loop, which checks the condition before loop body executes. For loops are entry controlled loops, which means the condition is checked before the loop body executes. In a do-while loop, the loop body is executed at least once before the loop condition is checked. If the condition is true, the loop continues, but if the condition is false, the loop exits. Therefore, c) do-while loop is an exit controlled loop, the loop is controlled by the exit condition rather than the entry condition, making it an exit controlled loop. The while loop and the for loop are entry controlled loops, as they first check the loop condition before executing the loop body.
Learn more about do-while visit:
https://brainly.com/question/30885778
#SPJ11
Which of the following are peripherals?
Rasterize
Sneaker-net
Media access control
None of the above
Answers
Answer:
D
Explanation:
A peripheral or peripheral device is ancillary device used to put information into and get information out of the computer.
Answer: D
Explanation:
Select the correct answer.
Ben wants to keep similar items close to each other in the image he is working on. Which is the most effective technique for applying the gestalt
concept of proximity?
The BLANK technique is the most effective technique for applying the gestalt concept of proximity.
Answers
Gestalt Principles are principles/laws of human perception that describe how humans group similar elements, recognize patterns and simplify complex images when we perceive objects.
What are the Gestalt Principles?The tendency to view items as belonging to the same grouping when they are close to one another is known as the gestalt principle of
proximity
. It claims that regardless of how different the forms and sizes are from one another, if shapes are close to one another, you will perceive them as groups. One of Gestalt's principles, the concept of closeness focuses on how each stimulus would be seen in its most basic form. The
Law of Simplicity
or the Law of Pragnanz are other names for it. It is founded on the idea that the sum of a thing is worth more than the sum of its components.
To learn more about Gestalt Principles refers to;
https://brainly.com/question/4734596
#SPJ1
State one criteria that makes a piece of malware a virus.
Answers
Answer: Self replication
Explanation: Malware is a catch-all term for any type of malicious software, regardless of how it works, its intent, or how it's distributed. A virus is a specific type of malware that self-replicates by inserting its code into other programs.
1. Which of the following CAN NOT be considered as information? (1) The average height of students in a class.
(2) The total sales of a company for the month of May.
(3) The body temperature of a patient.
(4) The number of copies of a book sold at the end of the day. (5) Literacy rate of a country.
Answers
Answer:
Explain three most significant features of computer
what protocol is responsible for assigning internet protocol (ip) addresses to hosts on many networks?
Answers
The DHCP protocol is commonly used to assign IP addresses (Dynamic Host Configuration Protocol). An internet service provider can use DHCP to give a specific device a public IP address.
What is meant by DHCP protocol?The Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically assigns an Internet Protocol (IP) host with its IP address and other necessary configuration data, such as the subnet mask and default gateway. The Dynamic Host Configuration Protocol (DHCP) is a network protocol used to set up network devices for IP network communication. A DHCP client utilizes the DHCP protocol to obtain configuration data from a DHCP server, such as an IP address, a default route, and one or more DNS server addresses.Your PC's ability to communicate with other Computers is governed by TCP/IP. We advise using automatic Dynamic Host Configuration Protocol to make managing TCP/IP settings easier (DHCP).To learn more about DHCP protocol, refer to:
https://brainly.com/question/14234787
C++ please help
The program first reads integer orderCount from input, representing the number of pairs of inputs to be read. Each pair has a string and an integer. One Order object is created for each pair and added to vector orderList. Call each Order object's Print().
Ex: If the input is:
5 bread 17 gyro 4 coconut 3 fennel 5 truffle 12
then the output is:
Order: bread, Quantity: 17 Order: gyro, Quantity: 4 Order: coconut, Quantity: 3 Order: fennel, Quantity: 5 Order: truffle, Quantity: 12
Note: The vector has at least one element.
code below:
#include
#include
using namespace std;
class Order {
public:
void SetFoodAndQuantity(string newFood, int newQuantity);
void Print() const;
private:
string food;
int quantity;
};
void Order::SetFoodAndQuantity(string newFood, int newQuantity) {
food = newFood;
quantity = newQuantity;
}
void Order::Print() const {
cout << "Order: " << food << ", Quantity: " << quantity << endl;
}
int main() {
int orderCount;
unsigned int i;
vector orderList;
Order currOrder;
string currFood;
int currQuantity;
cin >> orderCount;
for (i = 0; i < orderCount; ++i) {
cin >> currFood;
cin >> currQuantity;
currOrder.SetFoodAndQuantity(currFood, currQuantity);
orderList.push_back(currOrder);
}
/* Your code goes here */
return 0;
}
Answers
Here is the modified code that meets the requirements mentioned in the problem:
#include <iostream>
#include <vector>
using namespace std;
class Order {
public:
void SetFoodAndQuantity(string newFood, int newQuantity);
void Print() const;
private:
string food;
int quantity;
};
void Order::SetFoodAndQuantity(string newFood, int newQuantity) {
food = newFood;
quantity = newQuantity;
}
void Order::Print() const {
cout << "Order: " << food << ", Quantity: " << quantity << endl;
}
int main() {
int orderCount;
unsigned int i;
vector<Order> orderList; // vector of Order objects
Order currOrder;
string currFood;
int currQuantity;
cin >> orderCount;
for (i = 0; i < orderCount; ++i) {
cin >> currFood;
cin >> currQuantity;
currOrder.SetFoodAndQuantity(currFood, currQuantity);
orderList.push_back(currOrder);
}
// Loop through the orderList vector and print each order
for (i = 0; i < orderList.size(); ++i) {
orderList[i].Print();
}
return 0;
}
The code reads an integer representing the number of pairs of inputs to be read.
For each pair, an Order object is created with the string and integer values, and then added to a vector. Finally, the Print() function is called for each object in the vector.
Learn more about codes;
https://brainly.com/question/28848004
#SPJ1
2. Enter the Grade Points for each grade Earned
3. Enter the Credits Earned for each course. **Hint: The F grade will still receive a 1.0 for Credits Earned.
4. Calculate the Grade Points Earned by multiplying the Grade Points times the Credits Earned for each course.
5. Total the Grade Points and Credits Earned column.
6. Divide the total number of grade points by credits earned to calculate the GPA.
Help please
Answers
To calculate GPA, enter grade points and credits earned for each course, calculate grade points for each course, add total grade points and credits earned, then divide total grade points by total credits earned.
To calculate your GPA using the provided steps, follow this process: 1. For each course, enter the grade points earned according to the respective grade (e.g., A=4.0, B=3.0, C=2.0, D=1.0, F=0.0). 2. Enter the credits earned for each course. If a course has an F grade, still record 1.0 credit earned. 3. Calculate the grade points earned for each course by multiplying the grade points by the credits earned. 4. Add up the total grade points and credits earned from all courses. 5. Divide the total grade points by the total credits earned to calculate your GPA.
Using this method will help you determine your GPA based on the grades and credits earned for each course.
Learn more about GPA here;
https://brainly.com/question/15170636
#SPJ11
you are the it administrator for a small corporate network. the employee in office 1 shares her computer with other users. she needs your help to secure the contents of the d:\finances folder so that unauthorized users cannot view the documents in the folder. in this lab, your task is to complete the following: encrypt the d:\finances folder and all of its contents. add emily as an authorized user for the d:\finances\2018report.xlsx file
Answers
To secure the contents of the D:\Finances folder and restrict unauthorized access, you can encrypt the folder and its contents. This will ensure that only authorized users can view the documents.
Follow these steps to encrypt the folder:
Right-click on the D:\Finances folder and select "Properties."
In the Properties window, go to the General tab and click on the "Advanced" button.
In the Advanced Attributes window, check the box that says "Encrypt contents to secure data" and click "OK."
You will be prompted to confirm if you want to encrypt the folder and its contents. Choose "Apply changes to this folder, subfolders, and files" and click "OK."
By encrypting the folder, the documents within it will be protected with encryption, and unauthorized users will not be able to view them without the necessary decryption key.
To add Emily as an authorized user for the D:\Finances\2018report.xlsx file, follow these steps:
Right-click on the 2018report.xlsx file and select "Properties."
In the Properties window, go to the Security tab and click on the "Edit" button.
Click on the "Add" button to add a new user.
Type "Emily" in the text box and click "Check Names" to verify the username.
Once the username is verified, click "OK" to add Emily as an authorized user.
In the Permissions window, select the appropriate permissions for Emily, such as "Read" or "Full control."
Click "OK" to save the changes.
In conclusion, encrypting the D:\Finances folder and adding Emily as an authorized user for the 2018report.xlsx file will help secure the contents and ensure that only authorized users can access them.
To learn more about encryption visit:
brainly.com/question/33596430
#SPJ11
Some one help pls will mark brainless !!!!!
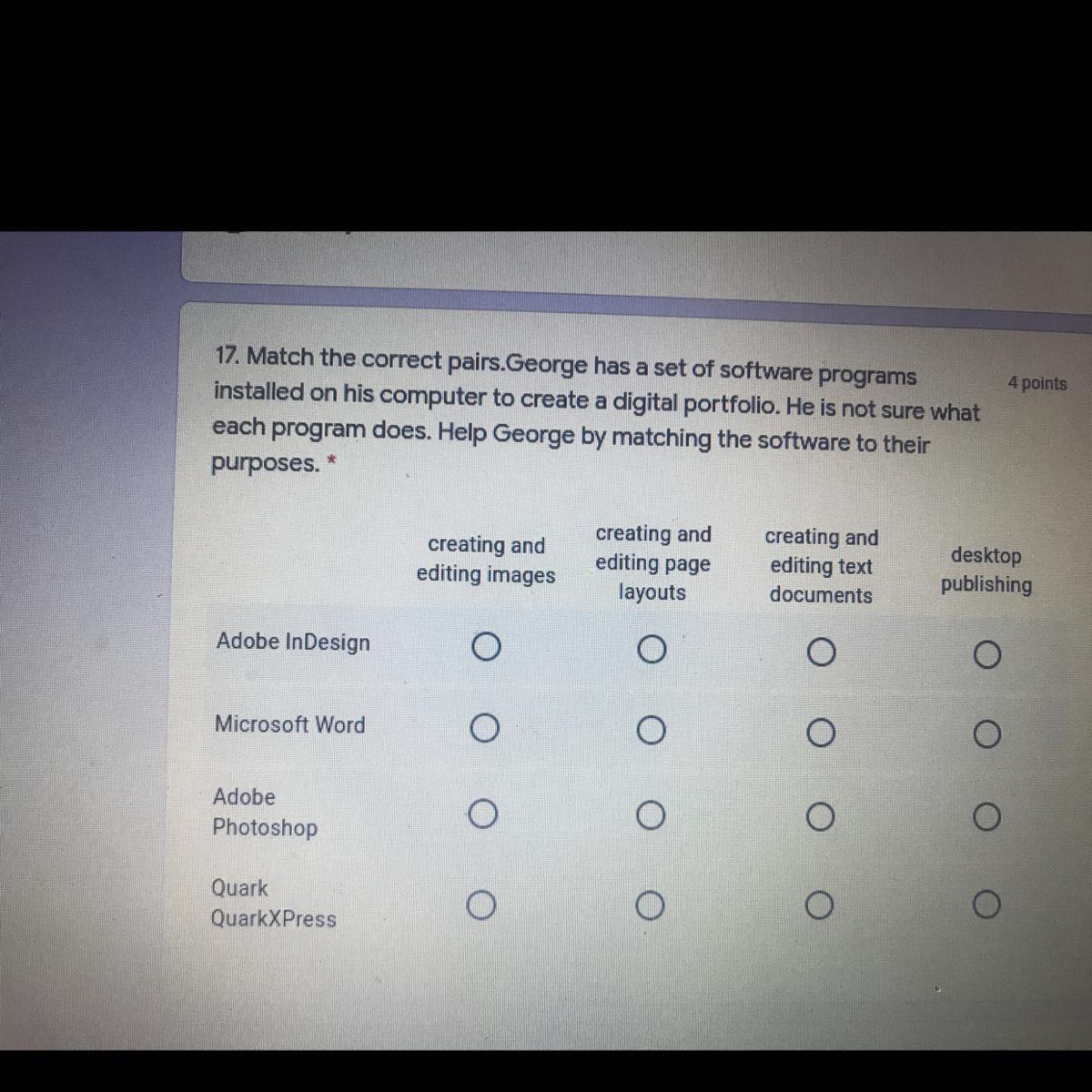
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
When it comes to new technology, where do you fall on the diffusion of innovation curve? Where are your parents? Do you think it's mostly young people who are early adopters of technologies? The kick-off session talked about great technologies failing because society wasn't ready for it. Do you have an example of this where it was a great technology/innovation but it still failed?
Answers
Innovators, Early adopters, Early majority, Late majority, Laggards are the categories of the diffusion of innovation curve an individual can fall into, When it comes to new technology
Innovators are individuals who adopt new technologies as soon as they are available. Early adopters are individuals who are willing to take a risk on a new technology that shows promise but is not yet proven. Early majority is the group of people that adopt new technologies only when it is necessary for them to do so. Late majority are individuals who are skeptical of new technologies until they have been widely adopted. Laggards are individuals who are resistant to new technologies and will only adopt them when they are absolutely necessary.
When it comes to my parents, they fall into the category of late majority. They are willing to adopt new technologies when they are necessary but are skeptical of them until they are widely adopted.
I do not think that it is only young people who are early adopters of technologies. People of all ages can be early adopters of technologies. However, younger people are more likely to be early adopters because they have grown up with technology and are more comfortable using it.
The kick-off session talked about great technologies failing because society wasn't ready for it. One example of this is the Betamax video format. Betamax was a superior video format to VHS, but it failed because the public was not ready for it. VHS was easier to use and more widely available, which made it more popular than Betamax.
Individuals' placement on the diffusion of innovation curve varies, and it is not limited to young people as early adopters. Furthermore, the failure of great technologies like Betamax showcases how societal readiness and market factors can influence the success or failure of an innovation.
Learn more about diffusion of innovation curve:
https://brainly.com/question/31940248
#SPJ11
For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


The development of computer languages is classified into two categories .
true or false
Answers
Answer:
False
Explanation:
Mark me as a brainliest
Can a WiFi router see if your device is active if the cell radio is disconnected but the WiFi is on? (Which can be done using an APK or ADB command.)
Answers
Answer:
I don't think so... it shouldnt be able to... considering the cell radio is off
Vivian and other members of her group are attending an event where they have to give short, uninterrupted speeches, one after the other. The moderator has a passive role during the course of the discussion, he or she has to simply introduce the presenters and manage the time frame of the event. At the end of the discussion, the moderator engages with the presenters and audience to ask questions and point to areas of agreement or disagreement.
Vivian is part of a _____.
Answers
Answer:
Panel discussion at a symposium
Explanation:
A symposium is a discussion held in public and arranged so that groups of experts in a particular field of study can come together and present information, papers, discoveries, and new researches and also to provide recommendations as to what is and not to be done
A moderator for the symposium and the panel members usually seat in front of an audience to whom a prepared brief report is presented by the panel group members after which the key point may be summarized by the moderator and the audience can take part in asking questions which are answered by the panel members
Therefore;
Vivian is part of a panel discussion at a symposium
Which of the following is normally included in the criteria of a design?
Answers
The one that is normally included in the criteria of a design is budget. The correct option is 3.
What is budget?A budget is an estimate of revenue and expenses for a given period of time that is usually compiled and re-evaluated on a regular basis.
Budgets can be created for an individual, a group of people, a company, a government, or almost anything else that makes and spends money.
Criteria are requirements that the design must meet in order to be successful. Constraints are design limitations.
These may include the materials available, the cost of the materials, the amount of time available to develop the solution, and so on.
Thus, the correct option is 3.
For more details regarding budget, visit:
https://brainly.com/question/15683430
#SPJ1
1. Materials
2. Time
3. Budget
4. Efficiency
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
refers to the increasing accessibility of technology, allowing more people to access information, create content, and develop applications.refers to the increasing accessibility of technology, allowing more people to access information, create content, and develop applications.
Answers
Answer:
Democratization of technology
Explanation:
Democratization of technology refers to the increasing accessibility of technology. More people have better access to the tools needed to view content and create technology solutions of their own.
Answer:
democratization of technology: the increasing accessibility of technology, allowing more people to access and create content and applications
Explanation:
- Edge 2022
what do you mean by networking devive?
Answers
Answer:
Networking Device are Those Device which are required for communicating and interacting between device and a computer network.
Explanation:
Question 4 of 25
in which situation would modular design be least beneficial for a game
program?
a. the program is extremely simple.
b. the programmer wants each task to be unique.
c. the program has many different parts.
d. the programmer is concerned about errors.
Answers
A situation which modular design would be least beneficial for a game program is: A. the program is extremely simple.
What is modular design?Modular design can be defined as a software development technique that involves the separation of the overall functionality of a software into independent and interchangeable software sections or modules.
Also, modular design can be used to break a large code in a software into smaller blocks holding specific functions.
In this context, we can infer that modular design would be least beneficial for a game program when the software program is extremely simple.
Read more on modular design here: https://brainly.com/question/14192464
#SPJ1
Answer:
A. the program is extremely simple.
Explanation: