Privacy is considered keeping information about a network or system user from being disclosed to unauthorized people.A. TrueB. False
Answers
Answer:
A. True
Explanation:
Privacy: In computer science, The term "privacy" is described as an issue that generally concerns specific computer community in order to maintain some personal information associated with individual citizens of specific nations in computerized systems that is responsible for keeping the records. However, it is also a major concerns for different individuals to keep their data safe.
Answer:
True
Explanation:
Privacy is considered keeping information about a network or system user from being disclosed to unauthorized people. As per the Information privacy law, the relationship between the collection and dissemination of data, technology, the public expectation of privacy, legal and political issues surrounding them.It is also known as data privacy or data protection.
Related Questions
As a computer science student, how do you assess your vulnerability to information theft in comparison to a famous celebrity?
Answers
Answer:
Explanation:
As a computer science student, you should assess your vulnerability to information theft by analyzing the types of information you have and where you store it, as well as the security measures you have in place to protect that information. This includes things like passwords, two-factor authentication, and encryption.
A famous celebrity, on the other hand, may have a higher level of vulnerability to information theft due to their high-profile status and the fact that they may have more sensitive information such as financial information, personal contacts, and private photos and videos. They may also be targeted more frequently by hackers and scammers who are looking to exploit their fame and popularity.
It is important to note that everyone's vulnerability to information theft is different and it is important to take the necessary steps to protect your personal information, regardless of whether you are a computer science student or a famous celebrity. This includes keeping your software and operating system updated, being cautious when clicking on links or opening email attachments from unknown sources, and not sharing personal information online.
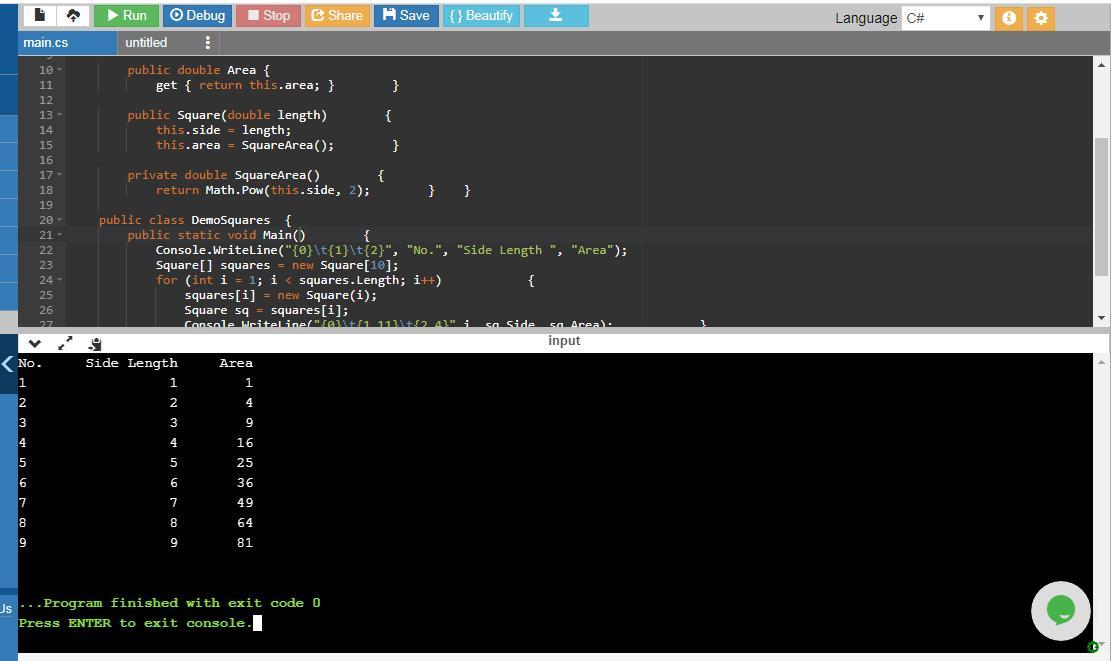
C# Create a program named DemoSquares that instantiates an array of 10 Square objects with sides that have values of 1 through 10 and that displays the values for each Square. The Square class contains fields for area and the length of a side, and a constructor that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method that computes the area field. Also include read-only properties to get a Square’s side and area.
Answers
Answer:
Here is the C# program.
using System; //namespace for organizing classes
public class Square //Square class
//private fields/variables side and area of Square class
{ private double side;
private double area;
//Side has read only property to get Square side
public double Side {
get { return this.side; }
}
//Area has read only property to get Square area
public double Area {
get { return this.area; } }
/*constructor Square(double length) that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method SquareArea() that computes the area field */
public Square(double length) {
this.side = length;
this.area = SquareArea(); }
//method to calcuate area of a square
private double SquareArea() {
//Pow method is used to compute square the side i.e. side^2
return Math.Pow(this.side, 2); } }
public class DemoSquares {
public static void Main() { //start of main() function body
//displays the side and area on output screen
Console.WriteLine("{0}\t{1}\t{2}", "No.", "Side Length ", "Area");
//instantiates an array to input values 1 through 10 into Side
Square[] squares = new Square[10]; //squares is the instance
for (int i = 1; i < squares.Length; i++) {
//traverses through the squares array until the i exceeds the length of the //array
squares[i] = new Square(i);
//parameter is passed in the constructor
//new object is created as arrray is populated with null members
Square sq = squares[i];
/*display the no, side of square in area after setting the alignment to display the output in aligned way and with tab spaces between no side and area */
Console.WriteLine("{0}\t{1,11}\t{2,4}", i, sq.Side, sq.Area); }
//ReadKey method is used to make the program wait for a key press from //the keyboard
Console.ReadKey(); } }
Explanation:
The program is well explained in the comments mentioned with each statement of the program. The program simply has Square class which contains area and length of side as fields and a constructor Square which has length of one side of Square as parameter and assigns its parameter to length of Square side. The a private method SquareArea() is called that computes the area field. get methods are used to include read-only properties to get a Square’s side and area. The program along with its output is attached in the screenshot.

What problem does Mitra identify in education? How can the internet and social media influence this problem?
Answers
Answer:
The problem that Mitra identifies in education is that kids don't go to school, don't know what a computer or the internet is. Teachers don't want to go to places where they're needed the most. The Internet and Social Media can influence problems because kids and young adults could be focusing on social media and relying on the internet more than actually focusing on there school work and working in general.
A binary floating point number is normalized when the binary point is to the immediate ____(RIGHT or LEFT)of the ___(Most or Least) significant bit of the actual significand.
What is A &= ~(2 << 6) doing?
What would be used by a compiler to achieve a faster integer division by a constant?
Answers
The expression "2 << 6" is equivalent to multiplying 2 by 2^6, which is 64. So, "2 << 6" results in 64. The bitwise NOT operator () flips all the bits of the expression that follows it, and the bitwise AND operator (&) performs a logical AND between the original value of A and the result of the NOT operation.
The compiler replaces a division operation with a multiplication and a bit shift operation, which are faster operations on most computer architectures. This technique can significantly speed up integer division by constants.
Learn more about binary: https://brainly.com/question/19802955
#SPJ4
Draw a logic circuit which represents the following logic expression:
X = NOT (A AND B) OR (A AND NOT B)
Answers
Answer:
Attached image
Explanation:
Step 1/4
1. First, we need to create a circuit for (A AND B). We can use an AND gate for this purpose, with inputs A and B.
Step 2/4
2. Next, we need to create a circuit for NOT (A AND B). We can use a NOT gate connected to the output of the AND gate from step 1.
Step 3/4
3. Now, we need to create a circuit for (A AND NOT B). We can use another AND gate with inputs A and the output of a NOT gate connected to input B.
Step 4/4
4. Finally, we need to create a circuit for the entire expression X = NOT (A AND B) OR (A AND NOT B). We can use an OR gate with inputs from the outputs of the NOT gate in step 2 and the AND gate in step 3. So, yes, it is possible to create a logic circuit that represents the given logic expression. The circuit would consist of 2 AND gates, 2 NOT gates, and 1 OR gate.

To achieve asymmetrical balance, what might an artist do?
A.
Use a reflection so that the top and bottom half of the image are mirrored.
B.
Use objects that have a different visual weight.
C.
Use objects that have the same visual weight.
D.
Use objects that are repeated across the image.
Answers
Answer:
Answer: B. Use objects that have a different visual weight.
Review 03 diagnostic and troubleshooting skills including data gathering methods and techniques.
Answers
The kinds and ways to improve your diagnostic and troubleshooting skills are:
Be Relax and never panic when you encounter it.Know everything about your computer. Look for solutions and clues and state them down. Find out the repeatability.What is diagnostic and troubleshooting?Diagnosing is known to be the act of finding out the root cause of any issue through an act of elimination but troubleshooting is known to be the act of fixing of the problem after diagnosis is said to have been carried out.
Therefore, The kinds and ways to improve your diagnostic and troubleshooting skills are:
Be Relax and never panic when you encounter it.Know everything about your computer. Look for solutions and clues and state them down. Find out the repeatability.Learn more about troubleshooting skills from
https://brainly.com/question/14983884
#SPJ1
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

Normally used for small digital displays
Answers
Answer:
LCD screens would be used for students using smaller devices in the classroom, like iPads or handheld touchscreens
What enables image processing, speech recognition & complex gameplay in ai
Answers
Deep learning, a subset of artificial intelligence, enables image processing, speech recognition, and complex gameplay through its ability to learn and extract meaningful patterns from large amounts of data.
Image processing, speech recognition, and complex gameplay in AI are enabled by various underlying technologies and techniques.
Image Processing: Convolutional Neural Networks (CNNs) are commonly used in AI for image processing tasks. These networks are trained on vast amounts of labeled images, allowing them to learn features and patterns present in images and perform tasks like object detection, image classification, and image generation.Speech Recognition: Recurrent Neural Networks (RNNs) and their variants, such as Long Short-Term Memory (LSTM) networks, are often employed for speech recognition. These networks can process sequential data, making them suitable for converting audio signals into text by modeling the temporal dependencies in speech.Complex Gameplay: Reinforcement Learning (RL) algorithms, combined with deep neural networks, enable AI agents to learn and improve their gameplay in complex environments. Through trial and error, RL agents receive rewards or penalties based on their actions, allowing them to optimize strategies and achieve high levels of performance in games.By leveraging these technologies, AI systems can achieve impressive capabilities in image processing, speech recognition, and gameplay, enabling a wide range of applications across various domains.
For more such question on artificial intelligence
https://brainly.com/question/30073417
#SPJ8
What type of customization have you or would you make to your operating system and. Why
Answers
Answer:
I have made a couple of customizations to my OS, which is Windows 10. The first being that I activated dark mode, this feature turns the entire OS into a dark-themed color, including apps and menus. This makes using the computer for extended hours much easier on the eyes. The other very important customization I added was a hover taskbar. This allows me to add many important shortcuts to the taskbar which all appear when I hover over the taskbar. It makes my desktop much cleaner and I have quick and easy access to my most important applications.
Explanation:
Customizing your operating system can improve productivity, security, and aesthetics by adjusting settings such as desktop appearance, keyboard shortcuts, and system performance.
What is an operating system?
An operating system is software that manages computer hardware and software resources and provides common services for computer programs.
What is an aesthetics?
In the context of operating systems, aesthetics refers to the visual design and appearance of the user interface, including elements such as icons, fonts, colors, and layout.
To know more about operating system, visit:
https://brainly.com/question/6689423
#SPJ1
Citi bike is an example of which arena of technology
Answers
Citi bike is an example of the arena of technology called Lyft.
What is Citi Bike?Citi Bike is a privately owned public bicycle-sharing system that operates in the Bronx, Brooklyn, Manhattan, and Queens boroughs of New York City, as well as Jersey City and Hoboken, New Jersey.
It was managed by Motivate (previously Alta Bicycle Share), with former Metropolitan Transportation Authority CEO Jay Walder as CEO, until September 30, 2018, when the firm was bought by Lyft. Lyft technology is used in the system's bikes and stations.
The system surpassed 50 million rides in October 2017 and will reach 100 million rides in July 2020.
Learn more about Lyft:
https://brainly.com/question/28547867
#SPJ1
what does the internet of things iot enable accenture
Answers
IoT platforms support applications' scalability and agility.
What is the Internet of things?The term "Internet of things" refers to actual physical things that have sensors, computing power, software, and other technologies and can link to other systems and devices via the Internet or other communications networks and exchange data with them.
IoT platforms support applications' scalability and agility.
Agility in IoT component harvesting, discovery, and reuse.
Scale horizontal elements so they scale vertically. IoT has emerged in recent years as one of the most significant 21st-century technologies.
Continuous communication between people, processes, and things is now possible thanks to the ability to connect commonplace items—such as household appliances, automobiles, thermostats, and baby monitors—to the internet via embedded devices.
Therefore, IoT platforms support applications' scalability and agility.
Know more about the Internet of things here:
https://brainly.com/question/19995128
#SPJ4
hich of the following are sql databases? (select all that apply.) 1 point mongodb mysql oracle couchdb mariadb postgresql
Answers
MariaDB, MySQL, PostgreSQL, and Oracle are the following SQL databases.
What are examples and databases?A database is a systematic collection of data. They make it possible to manipulate and store data digitally. Databases simplify data administration. Consider a dataset as an illustration. In quite an online telephone directory, a database is utilized to store information about persons, their phone numbers, and other forms of contact.
SQL: Is it a database?A SQL database, often known as a relational database, is made up of a number of highly organized tables where each row represents a certain type of data item and each column designates a particular field of data. Rdbms are developed using the structure of queries (SQL) to produce, store, update, store retrieve information.
To know more about Databases visit:
https://brainly.com/question/25198459
#SPJ1
The complete question is-
Which of the following are SQL databases? (Select all that apply.)
a. MongoDB
b. MariaDB
c. MySQL
d. PostgreSQL
e. CouchDB
f. Oracle
During early recording, microphones picked up sound waves and turned them into electrical signals that carved a _______ into the vinyl. (6 letters)
WILL PICK YOU AS BRAINLIEST!
hint- NOT journalism
HURRY please
Answers
Answer:
Groove
Explanation:
There is not much to explain
Write an application that accepts up to 20 Strings, or fewer if the user enters the terminating value ZZZ. Store each String in one of two lists—one list for short Strings that are 10 characters or fewer and another list for long Strings that are 11 characters or more. After data entry is complete, prompt the user to enter which type of String to display, and then output the correct list. For this exercise, you can assume that if the user does not request the list of short strings, the user wants the list of long strings. If a requested list has no Strings, output The list is empty. Prompt the user continuously until a sentinel value, ZZZ, is entered.
Answers
Answer:
count = 20
i = 0
short_strings = []
long_strings = []
while(i<count):
s = input("Enter a string: ")
if s == "ZZZ":
break
if len(s) <= 10:
short_strings.append(s)
elif len(s) >= 11:
long_strings.append(s)
i += 1
choice = input("Enter the type of list to display [short/long] ")
if choice == "short":
if len(short_strings) == 0:
print("The list is empty.")
else:
print(short_strings)
else:
if len(long_strings) == 0:
print("The list is empty.")
else:
print(long_strings)
Explanation:
*The code is in Python.
Initialize the count, i, short_strings, and long_strings
Create a while loop that iterates 20 times.
Inside the loop:
Ask the user to enter a string. If the string is "ZZZ", stop the loop. If the length of the string is smaller than or equal to 10, add it to the short_strings. If the length of the string is greater than or equal to 11, add it to the long_strings. Increment the value of i by 1.
When the loop is done:
Ask the user to enter the list type to display.
If the user enters "short", print the short list. Otherwise, print the long_strings. Also, if the length of the chosen string is equal to 0, print that the list is empty.
What was one of the main advantages of BPR at Chevron?
Answers
Answer:
Business process re-engineering improves performance of chevron at end-to-end process and saves company's fifty million dollars by reducing operation cost.
Write code in java that takes input from the user for the radius (double) of a circle, and create a circle with that radius. The program should then print a sentence with the circumference and area of the circle. You should use the appropriate Circle methods to obtain the circumference and area of the circle rather than calculating these values yourself.
Sample run:
Enter the radius of the circle:
> 3
A circle with a radius 3.0 has a circumference of 18.84955592153876 and an area of 28.274333882308138
Answers
Answer:
Explanation:
import java.util.Scanner;
public class Circumference {
public static void main(String[] args){
Scanner input = new Scanner(System.in);
System.out.print(“Enter the radius of the circle: ");
double userInput = input.nextDouble();
//create a new instance of the Circumference Class
Circumference c = new Circumference();
System.out.println(“A circle with a radius of “ + userInput + “ has a circumference of ” + c.getCircumference(userInput) + "and an area of " + c.getArea(userInput);
}
public double getCircumference(double radius){
return 2.0 * Math.PI * radius; //formula for calculating circumference
}
public double getArea(double radius){
return radius * radius * Math.PI; //formula for finding area
}
}
/* Formatting may be a lil weird in the main method(), if your getting errors just comment the print statement and re-type it yourself :)*/
A database on a mobile device containing bands, sub-bands and service provider ids allowing the device to establish connection with the right cell phone tower is called:.
Answers
Answer:
The database on a mobile device containing bands, sub-bands, and service provider IDs that allow the device to establish a connection with the right cell phone tower is called a "Preferred Roaming List" (PRL).
Explanation:
The PRL is a database maintained by the mobile network operator (MNO) and stored on the mobile device. It contains information about the bands and sub-bands supported by the MNO's network and the service provider IDs of roaming partners. When a mobile device is searching for a signal, it consults the PRL to determine which network frequencies and towers are available and compatible with the device.
The PRL is periodically updated by the MNO to reflect changes in network coverage and roaming agreements. Updates to the PRL can be pushed to the device over-the-air (OTA) or manually installed through a software update or by calling the carrier's customer service.
You are working as a marketing analyst for an ice cream company, and you are presented with data from a survey on people's favorite ice cream flavors. In the survey, people were asked to select their favorite flavor from a list of 25 options, and over 800 people responded. Your manager has asked you to produce a quick chart to illustrate and compare the popularity of all the flavors.
which type of chart would be best suited to the task?
- Scatter plot
- Pie Chart
- Bar Chart
- Line chart
Answers
In this case, a bar chart would be the most suitable type of chart to illustrate and compare the popularity of all the ice cream flavors.
A bar chart is effective in displaying categorical data and comparing the values of different categories. Each flavor can be represented by a separate bar, and the height or length of the bar corresponds to the popularity or frequency of that particular flavor. This allows for easy visual comparison between the flavors and provides a clear indication of which flavors are more popular based on the relative heights of the bars.
Given that there are 25 different ice cream flavors, a bar chart would provide a clear and concise representation of the popularity of each flavor. The horizontal axis can be labeled with the flavor names, while the vertical axis represents the frequency or number of respondents who selected each flavor as their favorite. This visual representation allows for quick insights into the most popular flavors, any potential trends, and a clear understanding of the distribution of preferences among the survey participants.
On the other hand, a scatter plot would not be suitable for this scenario as it is typically used to show the relationship between two continuous variables. Pie charts are more appropriate for illustrating the composition of a whole, such as the distribution of flavors within a single respondent's choices. Line charts are better for displaying trends over time or continuous data.
Therefore, a bar chart would be the most effective and appropriate choice to illustrate and compare the popularity of all the ice cream flavors in the given survey.
for more questions on Bar Chart
https://brainly.com/question/30243333
#SPJ8
C++
Set hasDigit to true if the 3-character passCode contains a digit.
#include
#include
#include
using namespace std;
int main() {
bool hasDigit;
string passCode;
hasDigit = false;
cin >> passCode;
/* Your solution goes here */
if (hasDigit) {
cout << "Has a digit." << endl;
}
else {
cout << "Has no digit." << endl;
}
return 0;
Answers
Answer:
Add this code the the /* Your solution goes here */ part of program:
for (int i=0; i<3; i++) { //iterates through the 3-character passCode
if (isdigit(passCode[i])) //uses isdigit() method to check if character is a digit
hasDigit = true; } //sets the value of hasDigit to true when the above if condition evaluates to true
Explanation:
Here is the complete program:
#include <iostream> //to use input output functions
using namespace std; // to identify objects like cin cout
int main() { // start of main function
bool hasDigit; // declares a bool type variable
string passCode; //declares a string type variable to store 3-character passcode
hasDigit = false; // sets the value of hasDigit as false initially
cin >> passCode; // reads the pass code from user
for (int i=0; i<3; i++) { //iterate through the 3 character pass code
if (isdigit(passCode[i])) // checks if any character of the 3-character passcode contains a digit
hasDigit = true; } //sets the value of hasDigit to true if the passcode contains a digit
if (hasDigit) { // if pass code has a digit
cout << "Has a digit." << endl;} //displays this message when passcode has a digit
else { //if pass code does not have a digit
cout << "Has no digit." << endl;} //displays this message when passcode does not have a digit
return 0;}
I will explain the program with an example. Lets say the user enters ab1 as passcode. Then the for loop works as follows:
At first iteration:
i = 0
i<3 is true because i=0
if (isdigit(passCode[i]) this if statement has a method isdigit which is passed the i-th character of passCode to check if that character is a digit. This condition evaluates to false because passCode[0] points to the first character of pass code i.e. a which is not a digit. So the value of i is incremented to 1
At second iteration:
i = 1
i<3 is true because i=1
if (isdigit(passCode[i]) this if statement has a method isdigit which is passed the i-th character of passCode to check if that character is a digit. This condition evaluates to false because passCode[1] points to the second character of pass code i.e. b which is not a digit. So the value of i is incremented to 1
At third iteration:
i = 2
i<3 is true because i=2
if (isdigit(passCode[i]) this if statement has a method isdigit which is passed the i-th character of passCode to check if that character is a digit. This condition evaluates to true because passCode[3] points to the third character of pass code i.e. 1 which is a digit. So the hasDigit = true; statement executes which set hasDigit to true.
Next, the loop breaks at i=3 because value of i is incremented to 1 and the condition i<3 becomes false.
Now the statement if (hasDigit) executes which checks if hasDigit holds. So the value of hasDigit is true hence the output of the program is:
Has a digit.

Scrabble is a word game in which words are constructed from letter tiles, each letter tile containing a point value. The value of a word is the sum of each tile's points added to any points provided by the word's placement on the game board. Write a program using the given dictionary of letters and point values that takes a word as input and outputs the base total value of the word (before being put onto a board). Ex: If the input is: PYTHON the output is: 14
Answers
Complete question:
Scrabble is a word game in which words are constructed from letter tiles, each letter tile containing a point value. The value of a word is the sum of each tile's points added to any points provided by the word's placement on the game board. Write a program using the given dictionary of letters and point values that takes a word as input and outputs the base total value of the word (before being put onto a board). Ex: If the input is: PYTHON
the output is: 14
part of the code:
tile_dict = { 'A': 1, 'B': 3, 'C': 3, 'D': 2, 'E': 1, 'F': 4, 'G': 2, 'H': 4, 'I': 1, 'J': 8, 'K': 5, 'L': 1, 'M': 3, 'N': 1, 'O': 1, 'P': 3, 'Q': 10, 'R': 1, 'S': 1, 'T': 1, 'U': 1, 'V': 4, 'W': 4, 'X': 8, 'Y': 4, 'Z': 10 }
Answer:
Complete the program as thus:
word = input("Word: ").upper()
points = 0
for i in range(len(word)):
for key, value in tile_dict.items():
if key == word[i]:
points+=value
break
print("Points: "+str(points))
Explanation:
This gets input from the user in capital letters
word = input("Word: ").upper()
This initializes the number of points to 0
points = 0
This iterates through the letters of the input word
for i in range(len(word)):
For every letter, this iterates through the dictionary
for key, value in tile_dict.items():
This locates each letters
if key == word[i]:
This adds the point
points+=value
The inner loop is exited
break
This prints the total points
print("Points: "+str(points))
Answer:
Here is the exact code, especially if you want it as Zybooks requires
Explanation:
word = input("").upper()
points = 0
for i in range(len(word)):
for key, value in tile_dict.items():
if key == word[i]:
points+=value
break
print(""+str(points))
What Is OpenShift Deployment?
Answers
Deploying applications on OpenShift, a Red Hat-designed container application platform, is an involved process that compiles the lifecycle management of the application, its horizontal and vertical scaling abilities, updates rolling out, and ensuring the application’s health and reliability.
How to explain the informationUnlocking these toolsets can be made easier with OpenShift's powerful selection of programmes and features which automate deployment while also monitoring and logging.
It also provides essential Continuous Integration and Deployment (CI/CD) pipelines to streamline the development process.
Learn more about deployment on
https://brainly.com/question/30259268
#SPJ1
Rectangular box formed when each column meet
Answers
Answer:
If this is a true or false I guess my answer is true?
Explanation:
How to use the RANK Function in Microsoft Excel
Answers
Answer:
=RANK (number, ref, [order])
See Explanation
Explanation:
Literally, the rank function is used to rank values (i.e. cells) in a particular order (either ascending or descending).
Take the following instances:
A column used for total sales can use rank function to rank its cells from top sales to least.
A cell used for time can also use the rank function to rank its cells from the fastest time to slowest.
The syntax of the rank function is:
=RANK (number, ref, [order])
Which means:
\(number \to\) The rank number
\(ref \to\) The range of cells to rank
\(order \to\) The order of ranking i.e. ascending or descending. This is optional.
How do all array indexes begin?
O A. With the number 0
OB. With the smallest item in the array
O C. With the largest item in the array
O D. With the number 1
Answers
All array indexes begin with the largest item in the array. The correct option is C.
What is an array?A grouping of comparable types of data is called an array. For instance, we can create an array of the string type that can hold 100 names if we need to record the names of 100 different persons.
Since modern programming languages' array indices typically begin at 0, computer programmers may use zeroth in places where others may use first, and so on. As a result, the array's index starts at 0, since I initially denote the array's first element.
Therefore, the correct option is C. With the largest item in the array.
To learn more about array, refer to the link:
https://brainly.com/question/19570024
#SPJ1
: A bisection search algorithm always returns the correct answer when searching for an element in a sorted list. True False
Answers
A bisection search algorithm always returns the correct answer when searching for an element in a sorted list is FALSE.
What is algorithm ?
An algorithm is a set of instructions or steps that are followed in order to solve a problem or complete a task. Algorithms are typically used when a precise set of steps is needed to solve a problem. They help reduce the time, effort, and resources needed to solve a problem. Algorithms can be written in any language, including natural language, and are used in a wide variety of fields, including mathematics, computer science, engineering, and economics.
To know more about algorithm
https://brainly.com/question/22984934
#SPJ4
What characteristics are common among operating systems? List types of operating systems, and examples of each. How does the device affect the functionality of an operating system?
Answers
The operating system (OS) controls all of the computer's software and hardware. It manages files, memory, and processes, handles input and output, and controls peripheral devices like disk drives and printers.
What are the characteristics of OS?The fundamental software applications running on that hardware enable unauthorized users to interact with the equipment because instructions can be sent and results can be obtained.Developers provide technology that may be compatible, mismatched, or completely incompatible with several other OS categories across multiple versions of the same similar OS.The operating systems are frequently 32-Bit and 64-Bit in two different versions.Types of Operating System:Distributed OS .
Batch processing OS.
Time sharing OS.
To learn more about operating system refer to :
https://brainly.com/question/22811693
#SPJ1
in java please
In this exercise, you will need to create a static method called findString in the MatchingString class that should iterate over String[] arr looking for the exact match of the String that is passed as a parameter.
Return the index of the array where the String is found; if it does not exist in the array, return -1.
For example, if the word “Karel” is passed in, your method would return 1.
Answers
Answer:
Explanation:
The following code is written in Java. It is a static method that takes in a String parameter and loops through the String array called arr comparing each element in the array with the word parameter that was passed. If it finds a match the method returns the index of that word, otherwise it will return -1
public static int findString(String word){
int index = -1;
for (int x = 0; x < arr.length; x++) {
if (word == arr[x]) {
index = x;
break;
}
}
return index;
}
Which function deletes the first occurence of 3 in a list named listB ?
listB.clear(3)
listB(3)
listB delete(3)
listB.remove(3)
Answers
Answer:
\(listB.remove(3)\)
Explanation:
Given
Options A to D
Required
Which deletes the first occurrence of 3
The options show that the question is to be answered using the knowledge of Python.
So, we analyze each of the options using Python syntax
(a) listB.clear(3)
In python, clear() is used to delete all elements of a list, and it does not take any argument i.e. nothing will be written in the bracket.
Hence, (a) is incorrect
(b) listB(3)
The above instruction has no meaning in Python
(c) listB delete(3)
The above instruction as written is an invalid syntax because of the space between listB and delete.
Also, it is an invalid syntax because lists in Python do not have the delete attribute
\((d)\ listB.remove(3)\)
This removes the first occurrence of 3
Answer: listB delete(3)
Explanation: got it right on edgen