memory is permanent storage that your computer uses to hold instructions and data.
Answers
Memory is an essential part of any computing device. It is a permanent storage area that your computer uses to hold data and instructions. Memory is divided into two broad categories: primary and secondary memory. Primary memory, also known as main memory, is the first place where data is stored after processing.
The CPU accesses primary memory directly for the execution of instructions and storage of temporary data. Primary memory is typically volatile, which means it is lost when the power is turned off. Secondary memory is a more permanent storage area for data. It is a non-volatile type of storage, which means it retains data even when the power is turned off.
Secondary memory is used for long-term storage of data, such as files, documents, images, and videos. Magnetic disks, solid-state drives, and optical disks are all examples of secondary memory devices. The capacity of secondary memory is typically much larger than that of primary memory, allowing for the storage of vast amounts of data.
To know more about device visit:
https://brainly.com/question/11599959
#SPJ11
Related Questions
How many bit patterns can be represented by 3 bits?
Answers
Answer:
6312
Explanation: dffe
The in and is operators both produce boolean results. O True O False
Answers
Both statements are true. Both the in and is operators in Python return Boolean values, True or False, based on the condition that they evaluate.
The in operator can be used to check whether a given value is present in a list or character string, and it returns True if the value is present and False otherwise. The third statement is not necessarily true. In Python, == is used to test for equality of values, whereas is is used to test for identity, which means that two variables refer to the same object in memory. While a == b being true implies that the values of a and b are equal, it does not necessarily mean that a is b will also be true. This is because two objects can have the same value, but still be distinct objects in memory.
Therefore, both statements are true.
Learn more about variables here:
brainly.com/question/17344045
#SPJ4
"Your question is incomplete, probably the complete question/missing part is:"
The in and is operators both produce Boolean results. O True O False The in operator can be used to check the contents of a character string or a list. O True O False If a == b is true, then a is b will also be true. O True O False
threadless is an online store that sells shirts with user-submitted designs. anyone can register and submit a design, then community members score the designs submitted each week, and threadless picks the top designs to sell in their store each week. designers receive royalties for every shirt sold. here's one example of a submitted user design: a screenshot of a threadless shirt design submission, of a dandelion riding a motorcycle, a username of the designer, and 1-5 scoring buttons. what situation would be least likely to threaten the success of the threadless crowdsourcing model? choose 1 answer: choose 1 answer: (choice a) if a large number of new designers suddenly join the community and submit double the number of designs. a if a large number of new designers suddenly join the community and submit double the number of designs. (choice b) if designers discover a new site with higher royalties for winning designs and only submit their designs on the new site. b if designers discover a new site with higher royalties for winning designs and only submit their designs on the new site. (choice c) if designers submit designs that aren't attractive to the threadless community and public at large. c if designers submit designs that aren't attractive to the threadless community and public at large. (choice d) if community members all decide to vote for shirts that they have no interest in owning. d if community members all decide to vote for shirts that they have no interest in owning.
Answers
Conciseness is also important and irrelevant parts of the question or typos should be ignored.The situation that would be least likely to threaten the success of the Thread less crowdsourcing model is if community members all decide to vote for shirts that they have no interest in owning.option b is correct
Thread less is an online store that sells shirts with user-submitted designs. Anyone can register and submit a design, then community members score the designs submitted each week, and Thread less picks the top designs to sell in their store each week. Designers receive royalties for every shirt sold.One example of a submitted user design is a screenshot of a Thread less shirt design submission, of a dandelion riding a motorcycle, a username of the designer, and 1-5 scoring buttons. The design has to appeal to the Thread less community and the public at large for it to sell.If a large number of new designers suddenly join the community and submit double the number of designs, it may be a good thing for the store. More designs could mean more choices for customers and potentially more sales. If designers discover a new site with higher royalties for winning designs and only submit their designs on the new site, this could be a threat to the Thread less crowdsourcing model. However, this situation is not the least likely to threaten the success of the model, as it involves the designers who submit designs.The situation that would be least likely to threaten the success of the Thread less crowdsourcing model is if community members all decide to vote for shirts that they have no interest in owning. This could lead to the selection of designs that are not attractive to the public and may not sell well. Therefore, it is important for the Thread less community members to be honest and vote for designs that appeal to them and are likely to be successful.For such more question on crowdsourcing
https://brainly.com/question/28360136
#SPJ11
What is the key sequence to copy the first 4 lines and paste it at the end of the file?
Answers
Press Ctrl+C after selecting the text you want to copy. Press Ctrl+V while holding down the cursor to paste the copied text.
What comes first in the copy and paste process for a slide?Select the slide you wish to copy from the thumbnail pane, then hit Ctrl+C on your keyboard. Move to the location in the thumbnail pane where you wish to paste the slide, then hit Ctrl+P on your keyboard.
What comes first in the copying process of a segment?The secret to copying a line segment is to open your compass to that segment's length, then mark off another segment of that length using that amount of opening.
To know more about copy visit:-
https://brainly.com/question/24297734
#SPJ4
when we merge two branches, one of two algorithms is used. if the branches have diverged, which algorithm is used?
Answers
When merging two branches, there are two algorithms that can be used: fast-forward merge and three-way merge.
Fast-forward merge is used when the branches have not diverged, meaning that the changes made in one branch can be applied directly to the other without any conflicts. In this case, the branch is simply moved forward to incorporate the changes from the other branch.
However, if the branches have diverged, meaning that both branches have made conflicting changes to the same file, the three-way merge is used. Three-way merge combines the changes made in both branches with the original version of the file to create a new version that includes all the changes. It uses a common ancestor, which is the last commit that both branches share, to identify which changes conflict and needs to be resolved.
During a three-way merge, Git will identify any conflicting changes and ask the user to resolve them manually. This involves choosing which changes to keep and which to discard, or finding a way to merge the changes together. Once the conflicts are resolved, the merge can be completed and the changes can be committed to the branch.
You can learn more about algorithms at: brainly.com/question/22984934
#SPJ11
every cell in a relation can hold only a single value. t/f
Answers
True. In a relation, each cell can hold only a single value.
In a relational database, a relation is represented as a table with rows and columns. Each cell in a relation can hold only a single value. This is because the relational model follows the principles of atomicity and data integrity.
Atomicity means that each value in a relation is indivisible and cannot be further divided into smaller components. For example, if we have a relation called 'Students' with columns like 'Name', 'Age', and 'Grade', each cell in the 'Name' column can hold only one student's name, and each cell in the 'Age' column can hold only one age value.
Data integrity ensures that the data in a relation is accurate, consistent, and reliable. By allowing each cell to hold only a single value, the relational model helps maintain data integrity by preventing data duplication or mixing of different types of data within a single cell.
Learn more:About relation here:
https://brainly.com/question/31111483
#SPJ11
The statement "every cell in a relationship can hold only a single value" is true (T) because, in the field of databases, a relation is referred to as a table.
A table, on the other hand, is made up of rows and columns. Each row is a record, and each column is a field. The table's content is determined by the values of the fields in the table's records. In a relational database, each cell can hold only one value. For example, consider the table below:`ID` | `Name` | `Age`1 | John | 252 | Mary | 303 | James | 28Each cell in the `ID` column contains a single ID value, and no cell in that column can hold two ID values.
Similarly, the `Name` column can only contain a single name-value per cell, and the `Age` column can only contain a single age value per cell. Therefore, it is correct to say that every cell in a relation can hold only a single value.
You can learn more about databases at: brainly.com/question/30163202
#SPJ11
How to explain the critical path analysis diagram
Answers
A project management tool called a critical path analysis diagram aids in determining the order of vital and interconnected actions that make up a work plan from beginning to end.
It is used to identify both vital and non-critical jobs as well as the most crucial order in which tasks should be completed for a project. The critical path analysis diagram, which is made up of several shapes and arrows linking each form, depicts the overall flow of control.
The work sequences of a project are represented graphically in the critical path analysis diagram, which also serves as a tool for determining if a project will be finished on schedule.
Learn more about on critical path, here:
https://brainly.com/question/15091786
#SPJ4
Drag the tiles to the correct boxes to complete the pairs Match each cloud service with its cloud component
Answers
MONITORING TOOLS - MaaS
STORAGE AND NETWORK DEVICES - IaaS
VIRTUAL COMPUTING PLATFORM - PaaS
SOFTWARE UPGRADES AND PATCHES - SaaS
don’t know why I did it in caps
the answers are right for Plato students! I just answered it correctly =D
SaaS (Software as a Service) and PaaS (Platform as a Service) is a feature that functions as a framework for the development of applications. This attribute of cloud computing aids in the development of the business for which the software is offered. It enhances operating systems, middleware, timely data transmission, and task management, among other things.
PaaS (Platform as a Service) is a feature that functions as a framework for the development of applications. It enhances operating systems, middleware, timely data transmission, and task management, among other things. It aids in the development, testing, and upgrading, of the software. SaaS is software upgrades and patches.
Therefore,IaaS- virtual computing platform,
SaaS- software upgrades and patches, MaaS- monitoring tools,PaaS- storage and network devices.
Learn more about SaaS, here:
brainly.com/question/13485221
#SPJ5
why might you want to install two power supplies in a critical server?
Answers
Installing two power supplies in a critical server provides redundancy and ensures uninterrupted power supply in case of a power failure or malfunction.
What are the benefits of having dual power supplies in a critical server setup?In a critical server environment, where uninterrupted operation is vital, installing two power supplies offers a reliable backup system. This redundancy minimizes the risk of downtime and potential data loss. If one power supply fails, the other immediately takes over, preventing any disruptions.
Furthermore, dual power supplies distribute the load evenly, reducing strain on each unit and prolonging their lifespan. By employing redundant power supplies, businesses can maintain continuous server functionality and protect against power-related failures or outages.
Learn more about Power supplies
brainly.com/question/13179707
#SPJ11
What is an Algorithm? (might not be in the chapter text). Give an example.
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
An algorithm is the list of a finite set of instructions and rules that a computer needs to do to complete a task in order to solve a problem.
In short, an algorithm is a series of instructions that are implemented step by step to solve a problem. For example, you could consider a pizza recipe an algorithm for making a pizza in an everyday life routine. But when you are talking about using algorithms in computation and in mathematics. It means that solving a problem using a series of steps step by step.
For example, your everyday tasks aligned on a google calendar and remind you about your tasks using the alarm, etc- how to implement this using set of instructions and rules- is an algorithm.
Solving a quadratic equation is another example of an algorithm.
Binary search, array sorting are an example of an algorithm in computation. Because these algorithms based on the execution of step-by-step instruction to solve a problem such as sorting a list of numbers etc.
computer system allows three users to access the central computer simultaneously. Agents who attempt to use the system when it is full are denied access; no waiting is allowed. of 28 calls per hour. The service rate per line is 18 calls per hour. (a) What is the probability that 0,1,2, and 3 access lines will be in use? (Round your answers to four decimal places.) P(0)= P(1)= P(2)= P(3)= (b) What is the probability that an agent will be denied access to the system? (Round your answers to four decimal places.) p k
= (c) What is the average number of access lines in use? (Round your answers to two decimal places.) system have?
Answers
In the given computer system scenario, there are three access lines available for users to access the central computer simultaneously. The arrival rate of calls is 28 per hour, and the service rate per line is 18 calls per hour.
We are required to calculate the probabilities of different numbers of access lines being in use, the probability of an agent being denied access, and the average number of access lines in use.
(a) To calculate the probabilities of different numbers of access lines being in use, we can use the formula for the probability of having k lines in use in a system with three lines, given by P(k) = (1 - p) * p^(k-1), where p is the utilization factor. The utilization factor can be calculated as p = λ / μ, where λ is the arrival rate and μ is the service rate per line.
Using the given values, we can calculate the probabilities as follows:
P(0) = (1 - p) * p^2
P(1) = (1 - p) * p^0
P(2) = (1 - p) * p^1
P(3) = p^3
(b) The probability of an agent being denied access is equal to the probability of all three access lines being in use, which is P(3) = p^3.
(c) The average number of access lines in use can be calculated using the formula for the average number of customers in a system, given by L = λ / (μ - λ). In this case, since there are three lines available, the average number of access lines in use would be L / 3.
By plugging in the values and calculating the probabilities and average number of access lines, we can obtain specific numerical answers.
Learn more about arrival rate here :
https://brainly.com/question/29099684
#SPJ11
i need help debugging this code
public challenge 1_2b
{
/* fix all the errors in this code */
public static void main(String[] args)
{
System.out.print("Baby");
System.out.print("Shark");
System.out.print("Do Doo Do Do Do Doo");
}
}
Answers
IS EVERYONE ASLEEP!!!!
where the smart people at
PLEASEEEEE HELPPPPPP
you can use the [nav] element to contain the major navigational blocks on the page, as well as links to such things as
a. privacy policy, terms, and conditions.
b. [div] elements
c. header and footer information
d. [article] and [section] elements
Answers
Answer:
a. privacy policy, terms, and conditions
Explanation:
The nav element usually includes links to other pages within the website. Common content that is found within a webpage footer includes copyright information, contact information, and page links
Question 1
1 pts
(02.01 MC)
Jackie used the software development life cycle to create a new game. Jackie ran her code to make sure it
worked and had no errors.
Which stage of the software development life cycle is Jackie currently in?
o Coding
O Maintenance
O Planning & Analysis
Testing
Answers
Answer:
she is running a maintenance to make sure everything works
WHAT ARE THE USES OF COMPUTER SCIENCE AND INFORMATION TECHNOLOGY
Answers
What is the bitrate of a system?
o The distance that date needs to travel in a network
O The strength of the network connection
The number of bis used to encode a single letter
O The amount of data in bits) that can be sent in a fixed amount of time
Answers
Answer:
The amount of data in bits) that can be sent in a fixed amount of time
Hope this helps!
If you don't mind, please mark this as brainliest!
If not, that's fine! Have a wonderful day!! ^-^
-Isa
Are DoS and DDos tactics appropriate for legitimate organizations to use against others? What fallout is considered appropriate fallout should an attack be used on others? Explain your answer.
Answers
Answer:
They are inappropriate
fallouts: Access denial and data theft
Explanation:
Dos ( denial of service ) and DDos ( distributed denial of service ) are inappropriate for legitimate organizations to use against each other. because DOS or DDos attacks are attacks on the server of an organization by sending an unusual amount of traffic to the server, thereby denying the devices and users connected to the server access to the server.
Access denial and data theft are the fallouts associated with DOS and DDos attacks
What kind of money is a gold certificate considered to be?
commodity
fiat
representative
currency
Answers
The kind of money a gold certificate is considered to be is: C. representative.
What is a gold certificate?A gold certificate can be defined as a certificate of ownership that is issued by a public treasury and held by the owner of a gold instead of holding the real gold itself.
In the United States of America, a gold certificate is typically issued exclusively to the Federal Reserve System (Fed) by the US Treasury.
In conclusion, the kind of money that a gold certificate is considered to be is representative.
Read more on money here: https://brainly.com/question/25959268
#SPJ5
The kind of money a gold certificate is considered to be is representative. Thus, option C is correct.
What is a gold certificate?A gold certificate can be defined as a certificate of ownership that is issued by a public treasury and held by the owner of a gold instead of holding the real gold itself. In the United States of America, a gold certificate is typically issued exclusively to the Federal Reserve System (Fed) by the US Treasury.
Money is a good that is widely recognized as a means of economic exchange. It serves as the means for expressing values and prices. It is the primary indicator of wealth because it moves from person to person and nation to country, facilitating trade.
Therefore, the kind of money that a gold certificate is considered to be is representative.
To learn more on money, click here:
brainly.com/question/28784237
#SPJ5
Some one help pls will mark brainless !!!!!
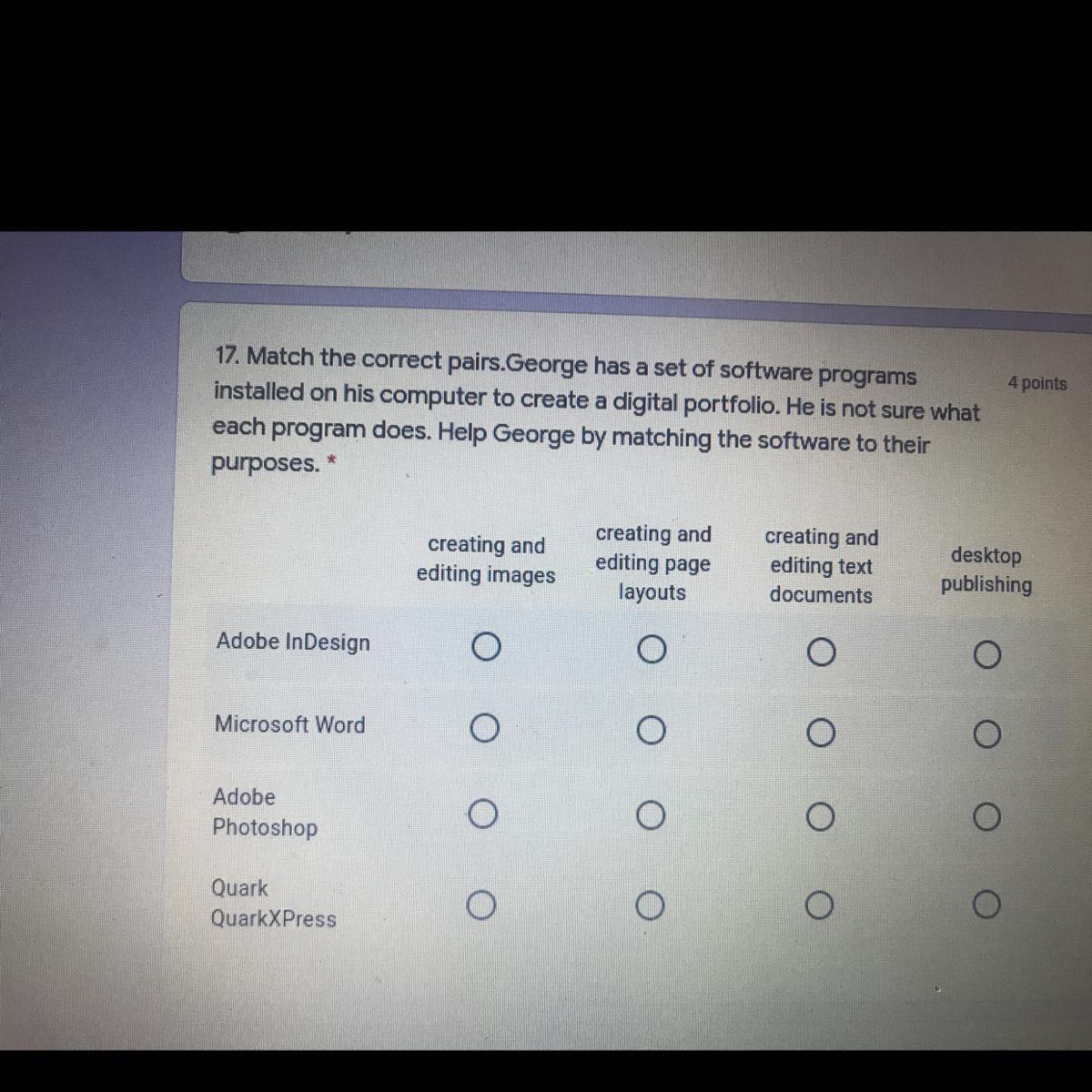
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
explain Machine Learning Quiz On Kernel Method?
Answers
Machine Learning Quiz on Kernel Method refers to a set of questions that are designed to test your understanding of the kernel method in the context of machine learning. The kernel method is a mathematical technique used in machine learning algorithms to transform data into a higher dimensional space, allowing for more accurate classification and prediction.
In a machine learning quiz on the kernel method, you may be asked questions about the different types of kernels (e.g. linear, polynomial, Gaussian), how to choose the appropriate kernel for a given dataset, and how to apply the kernel method in a machine learning algorithm.
To answer these questions, you will need to have a solid understanding of the kernel method, including its mathematical foundations and its applications in machine learning. You may also need to be familiar with different machine learning algorithms and how they use the kernel method to improve their performance.
In conclusion, a machine learning quiz on the kernel method is designed to test your knowledge and understanding of this important technique in the field of machine learning. By studying the kernel method and practicing with quizzes and exercises, you can improve your ability to apply this technique in real-world machine learning problems.
Learn more about Kernel Method at:
https://brainly.com/question/4504875
#SPJ11
_________ analysis is a data mining application that discovers co-occurrence relationships among activities performed by specific individuals or groups, such as market basket analysis, which retailers seek to understand the purchase behavior of customers.
Answers
Answer:
affinity analysis is the answer it is also called market basket analysis
Affinity analysis is a data mining application that discovers co-occurrence relationships among activities performed by specific individuals or groups, such as market basket analysis.
What is affinity analysis?Affinity Analysis is a type of predictive analysis method that uses data mining to uncover hidden, insightful correlations between various variables based on how frequently they occur between distinct persons or groups in the dataset.
The Product Affinities Analysis sheds light on the items that clients buy in tandem during a shopping trip, such as how they are filling out a broader weekly shopping trip or putting together specific meals.
Therefore, Affinity analysis is a data mining tool that identifies co-occurrence patterns between tasks carried out by particular people or groups, like market basket analysis.
To learn more about affinity analysis, refer to the link:
https://brainly.com/question/13077215
#SPJ5
The Caesar Cipher is one of the oldest forms of encryption. It certainly has its trade-offs when compared to other encryptions.
Make sure you’ve spent time exploring the previous examples that show the encryption, decryption, and cracking of a Caesar Cipher, then answer the following questions:
What are some of the advantages of using a Caesar Cipher?
What are some of the disadvantages of using a Caesar Cipher?
Does the Caesar Cipher use the symmetric encryption model, or the asymmetric encryption model? Explain your answer.
If you intercepted a message that had been encrypted using a Caesar Cipher, what is the maximum number of times you would need to guess-and-check different keys for the cipher before cracking it?

Answers
The advantages of using a Caesar Cipher are
The disadvantages of using a Caesar Cipher are:
Caesar cipher disadvantages include utilization of simple structures.can only give the information the bare minimum of security.A key indicator in understanding the complete message is the frequency of the letter pattern.What benefit does utilizing a cipher offer?Confidentiality – An encryption method can protect data and communications against unauthorized access and disclosure. Authentication Information can be safeguarded against spoofing and forgeries using cryptographic techniques like MAC and digital signatures.
Hence, One of the first known ciphers is called the "Caesar Box" or "Caesar Cipher." It was created circa 100 BC, and Julius Caesar used it to communicate with his generals in the field secretly. His adversary could not read his messages in the unlikely occasion that one was intercepted.
Learn more about Caesar Cipher from
https://brainly.com/question/14298787
#SPJ1
write the method heading for a method called larger that accepts 2 integer arrays and returns the array with the larger number of elements.
Answers
Writing a function to compute the average of the even numbers in the array is required for this application.
The percentage function When given an array of integers as a parameter or argument, even prints the average of the even numbers. The code below implements the aforementioned functionality in Python, and the code's output is also included. In computer science, an array is a group of objects (values or variables). At least one array index or key is used to uniquely identify each element. Given its index tuple, a mathematical formula can determine each element's location in an array. The simplest basic type of data structure is a linear array, sometimes known as a one-dimensional array. Since a two-dimensional grid can theoretically be used to represent a matrix, two-dimensional arrays are occasionally referred to as "matrices."
Learn more about array here:
https://brainly.com/question/28945807
#SPJ4
All of the following are security features in Microsoft Word except
(A) Encrypt with Password
(B) Rescript Editing
(C) Mark as Final
(D) Manage Document
Answers
how do i scan or check for computer virus?
Answers
Answer:
what type of computer
Explanation:
suppose that ram can be added to your computer at a cost of $50 per gigabyte. suppose also that the value to you, measured in terms of your willingness to pay, of an additional gigabyte of memory is $800 for the first gigabyte, and then falls by one-half for each additional gigabyte. a. how many gigabytes of memory should you purchase?
Answers
Random access memory is referred to as RAM. In essence, the RAM in your computer serves as short-term memory, storing information as the processor requests it.
Contrast this with persistent data, which is kept on your hard drive and is accessible even when your computer is off. For quick data storage and retrieval, RAM is used. Depending on the technology and task, your RAM can process information twenty to one hundred times faster than data on a hard disk. Memory is divided into two categories: SRAM (static random access memory) and DRAM (dynamic random access memory). A memory cell with six transistors is used for data storage in SRAM. SRAM is usually utilized as the processor's (CPU) cache memory and is typically not user-replaceable.
Learn more about memory here-
https://brainly.com/question/14829385
#SPJ4
what is the expression to reference the local scope for defined name totalsales from the final report worksheet
Answers
Final Report is the expression to use when referencing the local scope for the defined name totalsales from the final report worksheet.TotalSales.
What is worksheet?A worksheet, commonly referred to as a spreadsheet, is made up of cells where you can enter and compute data. There are columns and rows separating the cells. Workbooks are where worksheets are constantly kept. There may be numerous worksheets in a workbook. Essentially, a worksheet is a single-page spreadsheet that contains data. A file with numerous spreadsheets is called a workbook. An array of rectangular cells arranged in rows and columns make up a worksheet. One or more worksheets in a workbook are made up of connected content. Spreadsheets are derived from the word "spread," which refers to a newspaper or magazine article (text or image) that spans two facing pages, extends across the centerfold, and treats the two pages as one large page.To learn more about worksheet, refer to:
https://brainly.com/question/29763961
Question 1 (5 points) When you are at a job interview, you should use effective communication strategies, like formal language. What is formal language and why do we use it? Formal language helps create the impression that the speaker is an expert on the topic. It suggests to audience members that the speaker's points deserve respectful consideration, and it presents the ideas of the speech in the most polished possible way.. Formal language is archaic and derived from Shakespeare to help us sound fancy in order to ensure that an employer can see that we are versatile Formal language is our ability to speak more than just one language. If we are bilingual, we have a better chance at being hired.
Answers
This prompt is about formal oanguage and styles of communication. See the explanation below.
What is formal language and why do we use it ?Formal language refers to a style of communication that follows specific grammatical and linguistic conventions, typically associated with academic, professional, or formal settings. It is characterized by the use of proper grammar, syntax, and vocabulary, and avoids slang or colloquial expressions.
We use formal language in job interviews to convey professionalism, competence, and respect for the setting and the interviewer. It also helps to convey our ideas in a clear and concise manner, without the distractions of informal language.
Contrary to the notion that formal language is archaic or derived from Shakespeare, it is a contemporary and widely used mode of communication in formal settings. It is not related to bilingualism, which refers to the ability to speak two languages fluently.
Learn more about formal language:
https://brainly.com/question/24222916
#SPJ1
You are the administrator for a small network with several servers. There is only one printer, which is centrally located. Although indications are that this printer is over-utilized, there is neither space nor budget to add additional printers at this time.
There are often cases where a document is needed urgently, but when it is printed, it goes into the queue and is printed in the order received, not the order of the document's priority. You would like to allow Gladys, the administrative assistant, to have the ability to maintain the print queue. Specifically, you want her to be able to alter the order of printing for the documents waiting to be printed.
You need to permit Gladys to make this change without adding her to the local Administrators group or making significant changes to the way your office operates.
What should you do?
Answers
Answer:
The answer is "Allocate permission for managing documents to the Gladys printer."
Explanation:
In the given scenario, we allow permission for managing the documents to the Gladys printer. It should enable Gladys could continue these trends by bringing something into the community of local administrators and introducing major changes to wherewith your office operates. In especially, they need her to modify its printing process regarding documentation requiring printing.
e. Define the term ‘user interface’, giving examples.
f. What is a mobile application?
g. Explain briefly what a multi-tasking system is and how it works?
Answers
Answer:
uExplanation:
iiiiiiiiiiiiiiiiiiii