Layer 4 of the OSI model is also known as:
1) Transport layer
2) Network layer
3) Data link layer
4) Session Layer
Answers
Layer 4 of the OSI model is also known as the Transport layer. The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer has specific responsibilities and interacts with the adjacent layers to ensure seamless communication and data transfer.
The Transport layer, the fourth layer, plays a crucial role in ensuring end-to-end communication between devices. It is responsible for the efficient and reliable transmission of data between the sender and the receiver. Key functions of the Transport layer include establishing, maintaining, and terminating connections, as well as managing data flow control, error detection, and correction.
This layer operates above the Network layer (Layer 3) which is responsible for routing and forwarding data packets, and below the Session layer (Layer 5) which manages sessions and maintains connections between applications. The Data Link layer (Layer 2) helps in the reliable transfer of data across the physical layer, but it is not directly related to Layer 4.
In summary, Layer 4 of the OSI model is known as the Transport layer, and it plays a vital role in providing end-to-end communication, ensuring data integrity, and managing connections between devices.
Learn more about Transport layer. here:
https://brainly.com/question/4727073
#SPJ11
Related Questions
Why you should observe proper conduct in your communication in the different social networking sites? (3-5 sentences)
Answers
Answer: reputation
Explanation:
One must take care in posting to social media sites because, especially with followers, someone can take screenshots of an unsavory post. Then, the photo is stored locally on their phone (and even worse, can be automatically uploaded to the cloud, making chances of completely eradicating something embarrassing even slimmer). If this is shared around, it may hurt one's career or reputation. Thus, it would be better safe than sorry to pay attention to what you post.
for the host address 10.28.94.135 /27 the last usable host address in the sbunet would be
Answers
For the host address 10.28.94.135/27, the last usable host address in the subnet would be 10.28.94.158. The subnet mask /27 means that the first 27 bits of the 32-bit IP address are the network address, and the remaining 5 bits are used for host addressing.
To find the last usable host address in the subnet for the host address 10.28.94.135/27, follow these steps:
Identify the subnet mask: A /27 subnet mask has 27 bits for the network and 5 bits for the host, so the subnet mask is 255.255.255.224.Calculate the subnet address: Perform a bitwise AND operation between the host address (10.28.94.135) and the subnet mask (255.255.255.224). This gives you the subnet address of 10.28.94.128.
Find the broadcast address: With a /27 subnet mask, there are 2⁽³²⁻²⁷⁾ = 32 IP addresses in each subnet, including the network and broadcast addresses. Add 31 to the subnet address (10.28.94.128) to get the broadcast address, which is 10.28.94.159.
Determine the last usable host address: The last usable host address in the subnet is one less than the broadcast address. Therefore, the last usable host address is 10.28.94.158. So, for the host address 10.28.94.135/27, the last usable host address in the subnet would be 10.28.94.158.
To learn more about subnet : https://brainly.com/question/29527004
#SPJ11
Lynn would like to compare the tuition cost of three different colleges. Which type of chart would best display this data? Analogous Bar Diagram Scatter
Answers
Answer:
Bar chart
Explanation:
A bar chart or bar graph is used to present the data according to the categories in the form of rectangular bars. The data of each constituent is presented either vertically or horizontally. There are two axes on the bar chart. One of them represents one category while the other represents the value to be measured. The comparison among the data given can be easily found and analyzed using a bar chart.
The tuition cost of the three different colleges can be easily compared when the data can be presented in the bar chart.
Answer:
bar graph
Explanation:
A combination of the three main services in cloud computing
Answers
Answer:
: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS).
Explanation:
Cloud computing can be broken up into three main services: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS). These three services make up what Rackspace calls the Cloud Computing Stack, with SaaS on top, PaaS in the middle, and IaaS on the bottom.
what type of structure should be used to gain a last-in first-out access to data? group of answer choices a vector an array a stack a linked list a queue
Answers
The data structure that should be used to achieve a last-in, first-out (LIFO) access to data is a stack. This is one of the most common abstract data types (ADTs), and it can be implemented using a linked list or an array.
Linked list: This is a data structure that represents a sequence of nodes that are connected by links. Each node contains data and a reference to the next node in the sequence. A linked list is a dynamic data structure because it can be modified by adding or deleting nodes.Stack: A stack is an abstract data type that allows access to its elements in a LIFO order. It has two main operations: push, which adds an element to the top of the stack, and pop, which removes and returns the top element of the stack.Array: An array is a collection of elements that are stored in contiguous memory locations. It is a static data structure because its size is determined when it is created. A stack can also be implemented using an array.
To gain a last-in first-out (LIFO) access to data, the appropriate structure to use is a stack.
A stack is a data structure that follows the LIFO principle, where the last item inserted is the first one to be removed. It operates on the "push" and "pop" operations. When an item is pushed onto the stack, it is added to the top, and when an item is popped, the topmost item is removed.
Out of the provided answer choices, the stack is the structure specifically designed for LIFO access. The other options such as a vector, array, linked list, or queue do not inherently follow the LIFO principle. However, it's worth noting that a linked list can be used to implement a stack, as well as an array, depending on the implementation details. But in terms of the structure itself, a stack is the appropriate choice for LIFO access.
Learn more about Array:https://brainly.com/question/28061186
#SPJ11
What stage of the development process is often called the pre-alpha phase and is the "meat" of the design process where features of the game are built?
Answers
Answer:
Stage 3 : production
Explanation:
The stage 3 of the game design process is called the Production stage. It is also called as the pre-alpha stage or phase. It is considered as the "meat" of the design process where several feature of the game like the mechanics, environment, characters and all the other relevant contents are built and created by the producers, programmers, game designers and the artist who work together to produce a great gaming effect.
Which term describes the process of training a machine to do simple, repetitive
tasks, and adapt or correct its performance based on changing conditions at
speed and scale?
Intelligent Automation
O Robotic Process Automation
O Machine Learning
O Personal Automation
O I don't know this yet.
Answers
Robotic Process Automation (RPA) is the term that describes the process of training a machine to do simple, repetitive tasks and adapt its performance based on changing conditions at speed and scale.
Robotic Process Automation (RPA) refers to the use of software robots or "bots" to automate repetitive tasks within business processes. RPA involves training these bots to perform simple, rule-based tasks that were previously carried out by humans.
These bots can interact with various software applications, mimic human actions, and adapt their performance based on changing conditions. RPA allows organizations to automate routine and mundane tasks, increase efficiency, reduce errors, and achieve scalability.
While RPA focuses on process automation, it does not necessarily involve advanced cognitive capabilities like machine learning. RPA is widely used in various industries and sectors to streamline operations and optimize resource utilization.
Learn more about RPA here: brainly.com/question/28914209
#SPJ11
What are the three main default roles in Splunk Enterprise? (Select all that apply.) A) King B) User C) Manager D) Admin E) Power.
Answers
User, Admin, and Power are the three primary default roles in Splunk Enterprise.
A power user in Splunk is what?A Splunk Core Certified Power User is capable of creating knowledge objects, using field aliases and calculated fields, creating tags and event types, using macros, creating workflow actions and data models, and normalizing data with the Common Information Model in either. They also have a basic understanding of SPL searching and reporting commands.
What Splunk permissions are set to by default?There is only one default user (admin) in Splunk Enterprise, but you can add more. (User authentication is not supported by Splunk Free.) You have the following options for each new user you add to your Splunk Enterprise system: a password and username.
To know more about Splunk Enterprise visit:-
https://brainly.com/question/10756872
#SPJ4
A token code is valid :________.
a. for as long as it appears on the device
b. for up to one hour
c. only for the user who possesses the device
d. if it is longer than eight characters
Answers
A token code is valid for up to one hour. A token code is a unique code that is issued to a user for authentication purposes. It is a one-time password that is used to verify the identity of the user during the login process.
Token codes are typically valid for a limited period of time, after which they expire and can no longer be used.
The validity period of a token code depends on the system that generates it. In most cases, token codes are valid for up to one hour. This means that the user must log in within one hour of receiving the token code or it will expire.
Token codes are an important security measure that helps to protect user accounts from unauthorized access. They are commonly used in two-factor authentication systems, where users are required to provide both a password and a token code to access their accounts.
A token code is valid for up to one hour. It is a one-time password that is used to verify the identity of the user during the login process. Token codes are an important security measure that helps to protect user accounts from unauthorized access.
To know more about one-time password :
brainly.com/question/31835158
#SPJ11
what is the largest memory that can have a starting address of 0x9eb8000
Answers
The largest memory that can have a starting address of 0x9eb8000 depends on the addressing scheme and architecture of the system.
The starting address 0x9eb8000 is represented in hexadecimal format. To determine the largest memory that can have this starting address, we need to consider the addressable range supported by the system's architecture.
In general, the size of addressable memory depends on the number of address bits used by the system. Each address bit doubles the addressable memory capacity. For example, a system with 32 address bits can address up to \(2^3^2\) (or 4,294,967,296) memory locations.
To determine the largest memory, we would need to know the number of address bits used by the system corresponding to the given starting address. Without that information, we cannot provide a specific answer.
Learn more about Starting address
brainly.com/question/31365478
#SPJ11
Which are characteristics of interpreters? Select
all that apply.
translate high-level programming language
into binary computer machine language
offer a program run-time that is faster than
when a compiler is used for the translation
make it possible to change the source
program while the program is running
offer a program run-time that is slower than
when a compiler is used for the translation
Answers
Answer:
translation is used for interpretation
val = 50
def example():
val = 15
print (val)
print (val)
example()
print (val)
Answers
Answer:50
15
i dont know the 3rd number but hope it helped
Explanation:
Based on the given scenario above, the output will be 50, 15, 50. Check more about output below.
What are computer outputs?An output is known to be a kind of data that a computer is said to bring out after processing.
Based on the above, conclusively, looking at the programming code, we can say that the output will be 50, 15, 50.
Learn more about programming from
https://brainly.com/question/23275071
#SPJ2
Using first-class continuations, we can implement a lightweight unit of cooperative-multitasking known as a fiber. We will do this by implementing the following functions: spawn: Creates a new fiber. Similar to the Unix fork system call, when spawn is called it will return twice with different values. In our implementation, it will return first with the value #t (true) and then again with the value #f (false). yield: Performs a context switch to the next fiber, if there is one. I.e., returns back into the context of another fiber and resumes executing it. terminate: Terminates the calling fiber. For these functions to work, you will need to maintain a global queue of fibers (using a list), which is updated as necessary.
Answers
First-class continuations can implement lightweight multitasking known as a fiber. Functions such as spawn, yield, and terminate are used to create and manage fibers.
First-class continuations are a powerful feature in programming languages that can be used to implement cooperative multitasking. A fiber is a lightweight unit of multitasking that can be created using functions such as spawn, yield, and terminate. When the spawn is called, it creates a new fiber and returns twice with different values. Yield performs a context switch to the next fiber in the global queue of fibers, while terminate terminates the calling fiber. To manage the global queue of fibers, a list can be used to update it as necessary.
Using fibers can greatly improve the performance and efficiency of programs by allowing multiple tasks to run concurrently without the overhead of heavy threads or processes. However, care must be taken to properly manage the queue and prevent deadlocks or race conditions.
To know more about the programming languages visit:
https://brainly.com/question/16936315
#SPJ11
A three phase generator has each of its windings out-of-phase with each other by ? .
Answers
A three phase generator has each of its windings out-of-phase with each other by 120 degrees.
What is Three phase generator?An AC three-phase generator is known to be called the three AC single-phase generators.
They are said to be generators that tends to run sequentially with a kind of offset of 120° that often exist between them been taken two at a time.
Therefore, based on the above, one can say that the three phase generator has each of its windings out-of-phase with each other by 120 degrees.
Learn more about three phase generator from
https://brainly.com/question/15052099
#SPJ1
Write an expression that will cause the following code to print "equal" if the value of sensorreading is "close enough" to targetvalue. Otherwise, print "not equal". Hint: use epsilon value 0. 1.
Ex: if targetvalue is 0. 3333 and sensorreading is (1. 0/3. 0),
output is:.
Answers
Answer:
0.000_33333333......
Which feature of a file system is responsible for keeping track of changes in the system?
Answers
Answer:
Journaling
Explanation:
Journaling is a file system feature that is responsible for keeping track of changes in the system.
The binary number represented by the voltage graph below is
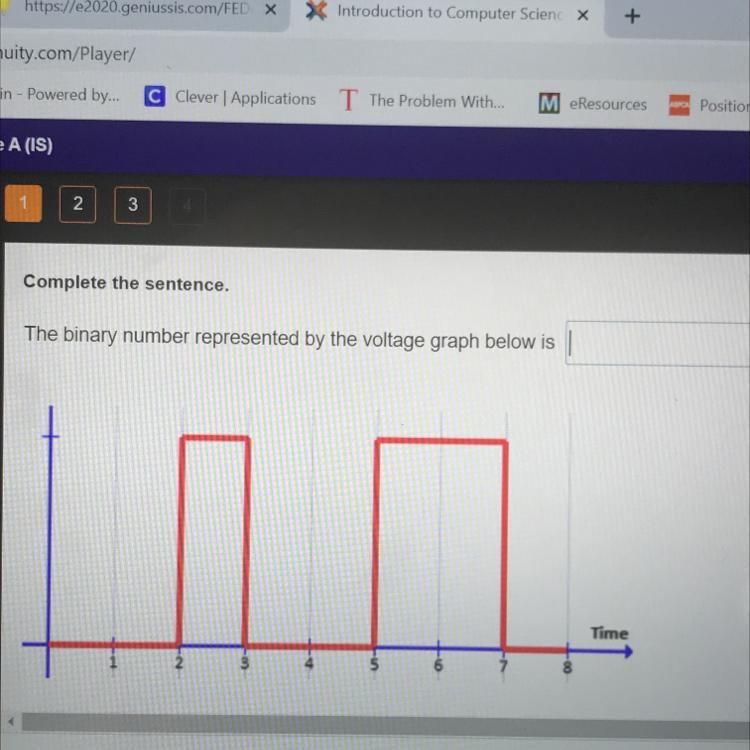
Answers
Answer:
4
Explanation:
Answer: 11010100
here ya go :)
Explain how to find the minimum key stored in a B-tree and how to find the prede- cessor of a given key stored in a B-tree.
Answers
To find the minimum key stored in a B-tree, we start from the root node and traverse down the leftmost child until we reach a leaf node. The key in the leftmost leaf node is the minimum key. To find the predecessor of a given key in a B-tree, we traverse the tree to locate the node containing the key. If the key has a left subtree, we move to the rightmost node of that subtree to find the predecessor key. Otherwise, we backtrack up the tree until we find a node with a right child. The key in the parent node of the right child is the predecessor.
To find the minimum key in a B-tree, we begin at the root node and follow the left child pointers until we reach a leaf node. At each node, we select the leftmost child until we reach a leaf. The key in the leftmost leaf node is the minimum key stored in the B-tree. This approach ensures that we always descend to the leftmost side of the tree, where the minimum key resides.
To find the predecessor of a given key in a B-tree, we start by traversing the tree to locate the node containing the key. If the key has a left subtree, we move to the rightmost node of that subtree to find the predecessor key. The rightmost node of a subtree is the node that can be reached by following right child pointers until no further right child exists. This node contains the predecessor key.
If the key doesn't have a left subtree, we backtrack up the tree until we find a node with a right child. The key in the parent node of the right child is the predecessor key. By moving up the tree, we ensure that we find the closest key that is smaller than the given key.
In summary, finding the minimum key in a B-tree involves traversing down the leftmost side of the tree until a leaf node is reached. To find the predecessor of a given key, we traverse the tree to locate the key, move to the rightmost node of its left subtree if it exists, or backtrack up the tree until we find a node with a right child.
learn more about B-tree here:
https://brainly.com/question/32667862
#SPJ11
You are in a group of five people whose small airplane crashed and
now you are stranded on a deserted tropical island for 24 hours. The
safety island is 3 miles away and can not be reached by walking.
Limited supplies from the plane have washed ashore(a flashlight, 2
bottles of water, a sheet, the tail of the plane, a bottle of perfume,
a ball of string, and a knife). Flora(plants/vegetation) and
fauna(animals) exist on the island.
1. You must use all of the supplies
2. Think of the "what if" issues: ex. How will your group
protect themselves from the animals? How can you reach
the safety island? How will your group eat? The sea
contains salt water, etc.
Answers
First and foremost, it's important to prioritize survival and safety in this situation.
What are the necessary steps?Here are some steps that the group could take using the available supplies:
Using the knife and ball of string, construct a shelter that can protect the group from the elements and provide a place to sleep. The sheet can be used as a roof or to create walls, and the tail of the plane can be used for support.
With the flashlight and knife, explore the island to find a fresh water source. If one is not found, the group can ration the two bottles of water until they can be rescued.
Use the knife and ball of string to create weapons and tools for protection and gathering food. The perfume can be used as a deterrent for some animals.
If there is no source of fresh water on the island, the group can use the ball of string and sheet to create a solar still to purify salt water from the sea.
Finally, the group can work together to come up with a plan to safely make their way to the safety island. This may involve using the tail of the plane as a makeshift raft, or building a larger boat using materials found on the island.
To protect themselves from animals, the group can create weapons and tools using the knife and ball of string.
Learn more about word problem on;
https://brainly.com/question/21405634
#SPJ1
Andreas wants to insert an element into an email that will graphically display the values in a table. Which option should he choose?
table
hyperlink
SmartArt
chart
Answers
Answer:
D. chart
Explanation:
Correct on edg
Answer:
d
Explanation:
took the test
A. Convert the following 1-byte (8-bits) binary numbers: • (1001 01102 to decimal using the following types: a) Unsigned binary number b) Signed 2's complement binary number c) BCD number
Answers
The conversions showcase the different interpretations and representations of the same binary number in decimal form, depending on the type of conversion being applied.
A. Convert the following 1-byte (8-bits) binary number: (1001 0110)₂ to decimal using the following types:
a) Unsigned binary number:
To convert an unsigned binary number to decimal, we calculate the sum of the decimal values of each bit position that is set to 1.
(1001 0110)₂ = (1 × 2^7) + (0 × 2^6) + (0 × 2^5) + (1 × 2^4) + (0 × 2^3) + (1 × 2^2) + (1 × 2^1) + (0 × 2^0) = 150
Therefore, the decimal representation of (1001 0110)₂ as an unsigned binary number is 150.
b) Signed 2's complement binary number:
To convert a signed 2's complement binary number to decimal, we consider the most significant bit (MSB) as the sign bit. If the sign bit is 0, the number is positive, and if the sign bit is 1, the number is negative. For negative numbers, we first invert all the bits and then add 1 to the result.
(1001 0110)₂ is a negative number since the MSB is 1.
First, invert all the bits: (0110 1001)₂
Then, add 1 to the result: (0110 1001)₂ + 1 = (0110 1010)₂
Now, convert the resulting binary number to decimal:
(0110 1010)₂ = (0 × 2^7) + (1 × 2^6) + (1 × 2^5) + (0 × 2^4) + (1 × 2^3) + (0 × 2^2) + (1 × 2^1) + (0 × 2^0) = -86
Therefore, the decimal representation of (1001 0110)₂ as a signed 2's complement binary number is -86.
c) BCD number (Binary-Coded Decimal):
BCD is a binary representation of decimal digits, where each decimal digit is encoded using 4 bits.
(1001 0110)₂ can be split into two BCD digits: (1001)₂ and (0110)₂.
For the first BCD digit, (1001)₂:
(1001)₂ = (9)₁₀
For the second BCD digit, (0110)₂:
(0110)₂ = (6)₁₀
Therefore, the BCD representation of (1001 0110)₂ is 96 in decimal.
The conversion of the 8-bit binary number (1001 0110)₂ to decimal using different types yields the following results:
a) Unsigned binary number: 150
b) Signed 2's complement binary number: -86
c) BCD number: 96
Learn more about 2's complement visit:
https://brainly.com/question/30885327
#SPJ11
How do you find the string of an array?
Answers
To find the string of an array, you can simply access a specific index of the array that contains the desired string.
An array is a data structure that stores a collection of elements of the same type, such as integers, characters, or strings. Each element in the array is identified by an index, which represents its position within the array.
To access the string stored at a specific index of the array, you can use the index to retrieve the element at that position. For example, if you have an array called "myArray" and you want to retrieve the string stored at index 2, you can do so using the following code:
myArray[2]
This will return the string stored at index 2 of the array. You can then use this string for whatever purpose you need in your program.
For more questions like Array click the link below:
https://brainly.com/question/31503078
#SPJ11
Urgent Please Help ASAP!! 50 Points!! Assignment due in 15 minutes!!
Reflect on the questions below.
1.) Why do some people resist help from others?
2.) Is it useful to work separately at some point in time during pair programming?
3.) How is pair programming beneficial?
4.) In pair programming, how can we better work together?
Answers
Questions:
1.) Why do some people resist help from others?
2.) Is it useful to work separately at some point in time during pair programming?
3.) How is pair programming beneficial
4.) In pair programming, how can we better work together?
Answers:
1.) Some people are prideful in their work, or they're just embarrassed to ask for assistance.
2.) It can be done, but pair programming is further effective with others.
3.) Pair programming is beneficial because you can get the job done faster.
4.) In pair programming, you can better work with your partner by working on different sections, and then checking each other's tail when the job is almost finished.
These answers are a combination of my knowledge and opinion(s). If you need any more help, do not hesitate to let me know. Glad I could help! :)
a skilled hacker who sometimes acts illegally and sometimes acts with good intent is a
Answers
A skilled hacker who sometimes acts illegally and sometimes acts with good intent is a "gray hat hacker."
A gray hat hacker refers to an individual who possesses advanced computer skills and expertise, engaging in hacking activities that may involve both legal and illegal actions. Unlike black hat hackers who primarily engage in malicious activities and white hat hackers who focus on ethical hacking, gray hat hackers operate in a morally ambiguous area. They may exploit security vulnerabilities to access systems or networks without proper authorization, but they often do so with good intentions, aiming to expose weaknesses and assist in improving security measures.
Gray hat hackers walk a fine line between the two opposing sides of hacking. While their actions may involve unauthorized penetration of systems or data breaches, they typically do not have malicious intent or seek personal gain. Instead, they may utilize their skills to identify vulnerabilities and notify the affected parties, offering assistance in securing the systems. In some cases, gray hat hackers may even publicly disclose the vulnerabilities to pressure organizations into addressing the issues promptly.
This gray area in hacking ethics often sparks debate and controversy. While some view gray hat hackers as valuable contributors to cybersecurity, others argue that their actions remain illegal and should be subject to legal consequences. The motivations of gray hat hackers can vary, with some driven by a desire to expose flaws and prompt improvements, while others may seek recognition or self-gratification.
Learn more about skilled hacker:
brainly.com/question/32899193
#SPJ11
Type the program's output.
#include
using namespace std;
int main()
{
int numCats;
numCats = 6;
if (numCats > 8) {
cout << "a" << endl;
}
else {
cout << "f" << endl;
}
cout << "k" << endl;
return 0;
}
Answers
The program's output is "f" followed by "k" on a new line.
The program starts by declaring an integer variable named numCats and assigning it a value of 6. Then, it checks if numCats is greater than 8 using an if statement. Since numCats is not greater than 8, the code inside the if block is not executed. Instead, the code inside the else block is executed which prints "f" to the console followed by an endline character.
After the if-else statement, the program prints "k" to the console followed by an endline character. Finally, the main function returns 0, indicating successful program execution.
Therefore, the program outputs "f" and "k".
Know more about program outputs here:
https://brainly.com/question/19088371
#SPJ11
It is common in DHCP configurations to exclude IP addresses from the scope of addresses you make available. What type of device might you exclude from a DHCP configuration
Answers
Storage server, is the type of device might you exclude from a DHCP configuration. Thus, option (d) is correct.
This serves to prohibit the DHCP server from allocating IP addresses to certain devices. Depending on the particular requirements of the network, a device may be omitted from a DHCP setup.
Storage server, is the type of device, generally speaking, devices that need a static IP address or devices that shouldn't be available to other networked devices may be left out of a DHCP configuration.
Therefore, option (d) is correct.
Learn more about on DHCP configurations, here:
https://brainly.com/question/8458316
#SPJ4
Your question is incomplete, but most probably the full question was.
It is common in DHCP configurations to exclude IP addresses from the scope of addresses you make available. What type of device might you exclude from a DHCP configuration?
A) BYOD employee smartphoneB) Thin client in the marketing departmentC) Sales department laptopD) Storage serverQuestion #1
Describe the issues regarding controlled airspace and minimum safe altitudes that affects an airborne pilot's decision-making.
Question #2
Describe how basic weather conditions such as wind, temperature, and precipitation will
affect a drone’s flight.
Question #3
Explain the role of the “Pilot-in-Command” and the “Remote-Pilot-in-Command.”
Question #4
Explain how a quadcopter maintains balanced flight while hovering.
Question #4
Explain how a quadcopter differs from an airplane to accomplish the maneuvers of pitch, roll, and yaw.
Answers
Answer:
1) Separation
2) Weather impacts on the ability to fly a drone
3) The Pilot-in-Command is in charge of a manned aircraft
The Remote-Pilot-in-Command is in charge of an unmanned aircraft
4) With the aid of a flight controller
5) A quadcopter is controlled by adjusting the rotor speeds
An airplane is controlled by adjusting the ailerons, elevator and rudder
Explanation:
1) Separation
Issues regarding controlled airspace and minimum safe altitudes that affects an airborne pilot's decision-making is called separation related issues
The concept of separation pertains to ensuring that an aircraft stays outside the minimum distance from other aircraft, obstacles or controlled airspace
Vertical Separation
The allowable vertical separation distance between two aircraft from the ground surface up to 29000 feet is 300 meters
The allowable vertical separation distance between two aircraft above 29000 feet is 600 meters
Horizontal separation
Horizontal separation are required for two aircraft that are closer to each other than the allowable minimum vertical separation. Horizontal separation includes, procedural separation, longitudinal separation, radar separation and reduced separation
2)
Wind
When the wind speed is high, it limits the drone's ability to maintain its position drifting the aircraft to undesired direction of flight
Temperature
High temperatures causes the the drone's motor to work harder generating more lift force which lead to shorter flight times
Cold temperatures reduces the battery efficiency and can also lower the battery voltage below the critical voltage.
Precipitation
A drone's is not waterproof and flying a drone i the rain can damage the equipment
Flying a drone in the rain increases the difficulty in its operation especially in drones that makes use of cameras for their flight stability
Rainy conditions reduces the strength and control of remote controllers
There is reduced visibility of flight during rainfall
3) In an aircraft, the Pilot-in-Command (PIC) is the pilot primarily responsible for the safety and operation of the aircraft during flight
The Remote-Pilot-in-Command has the primary responsibility and authority for the operation of a remotely operated (small) aircraft system
4) A quadcopter maintains balanced flight by the information sent to control the direction of the propeller and the orientation as well as the speed of the rotor controlled by flight controller through the electronic speed control circuit (ESC) to control the thrust, revolutions per minute (RPM) and the direction of the quadcopter
5) Pitch in a quadcopter is achieved by tilting to move forward
In an airoplane the pitch is controlled by the elevators
Roll in a quadcopter is achieved by increasing the rotation of the rotors on the one side and decreasing the rotor speed on the other side
Roll in an airplane is achieved by adjusting ailerons
Yaw in a quadcopter is the spin achieved by reducing the speed of the front rotor on the side opposite to the direction of the intended spin motion
Yaw in an airplane is achieved by adjusting the ruder and ailerons to turn the plane
how to delete text messages on iphone for both sides
Answers
Answer:
simple answer dont send it
Explanation:
Graphic designers consider _____ easier to use because it allows them to set the initial color based on hue and then fine-tune the saturation and lightness values.
Answers
Answer:
HSL is what is used
Explanation:
hue saturation lightness or hsl is what the answer is
hope this helped
scav
Choose which statement is wrong by applying your knowledge from the reading. a. A security manager works on tasks identified by the CISO and resolves issues identified by technicians. b. The relationship between security and convenience is inversely proportional: as security is increased, convenience is decreased. c. Since 2015, the number of unfilled cybersecurity positions has increased by 10 percent.
Answers
There are reasons why a statement can be wrong. The option that is a wrong statement is Since 2015, the number of unfilled cybersecurity positions has increased by 10 percent.
How are many cybersecurity jobs unfilled?The U.S. is known to have a high total employed cybersecurity workforce and some that are unfilled positions as reported by Cyber Seek.
Studies has shown that since 2015, the number of unfilled cybersecurity positions has gone up by 50 percent. Such that the total expected rate has been approximated to be at 1.8 million open cybersecurity positions by 2022.
Learn more about cybersecurity from
https://brainly.com/question/14286078