FILL THE BLANK. rising motion is associated with a surface _______ pressure system and with _______ aloft.
Answers
Rising motion is associated with a surface low-pressure system and with low pressure aloft.
In weather systems, rising motion refers to the vertical movement of air. It is commonly observed in areas where low-pressure systems exist, both at the surface and aloft.A surface low-pressure system is characterized by air converging and rising near the Earth's surface. As the air rises, it cools and condenses, leading to cloud formation and the potential for precipitation. Surface low-pressure systems are typically associated with unsettled weather conditions such as clouds, rain, and storms.Similarly, low pressure aloft refers to regions of lower atmospheric pressure at higher altitudes. In these areas, air tends to ascend due to the lower atmospheric density. This rising motion aloft can also contribute to cloud formation and the development of weather systems.Therefore, rising motion is associated with a surface low-pressure system and with low pressure aloft in meteorology.
To know more about system click the link below:
brainly.com/question/31185904
#SPJ11
Related Questions
Cual de las siguientes es una desventaja del uso de las computadoras?
A)Precision
B)Rapidez
C)Violacion ala privacidad
D)Confianilidad
Answers
Explanation:
Predict the output a b= 12 13 print(print(a+b))
Answers
Answer:
Invalid Syntax
We if correct the syntax then output is 25
Explanation:
In the given question a=12 ,b=13 if we used print(print(a+b)) this syntax then invalid syntax will occur if we correct the syntax then correct syntax program is given below
a =12
b=13
print(a+b)
it gives 25 as output because we used "+" operator between a and b variable this operator provide addition between the two variable .
Why is it important to perform routine computer maintenance? It can make more room for junk files and downloadable programs. It can help prevent hardware, software, and Internet access problems. It can stop computer problems from occurring more than once. It can help you remember how to perform steps to solve computer problems.
Answers
b :D
hope this helps
plz give me brainliest
only typed tht so i can have enough words lol
Answer:
B. It can help prevent hardware, software, and Internet access problems.
Explanation: trust dawg
For a new version of processor, suppose the capacitive load remains, how much more energy will the processor consume if we increase voltage by 20% and increase clock rate by 20%?
Answers
Answer:
The answer is below
Explanation:
The amount of power dissipated by a processor is given by the formula:
P = fCV²
Where f = clock rate, C = capacitance and V = Voltage
For the old version of processor with a clock rate of f, capacitance C and voltage of V, the power dissipated is:
P(old) = fCV²
For the new version of processor with a clock rate of 20% increase = (100% + 20%)f = 1.2f, capacitance is the same = C and voltage of 20% increase = 1.2V, the power dissipated is:
P(new) = 1.2f × C × (1.2V)² = 1.2f × C × 1.44V² =1.728fCV² = 1.728 × Power dissipated by old processor
Hence, the new processor is 1.728 times (72.8% more) the power of the old processor
the method used to transfer information to far off place instantly is called
Answers
Telecommunication
Explanation:
Which communication technology often takes the place of printed interoffice communication?.
Answers
Answer:
Explanation:
13. Place where names, addresses and email information
is stored
Answers
Answer in ur email
Explanation:
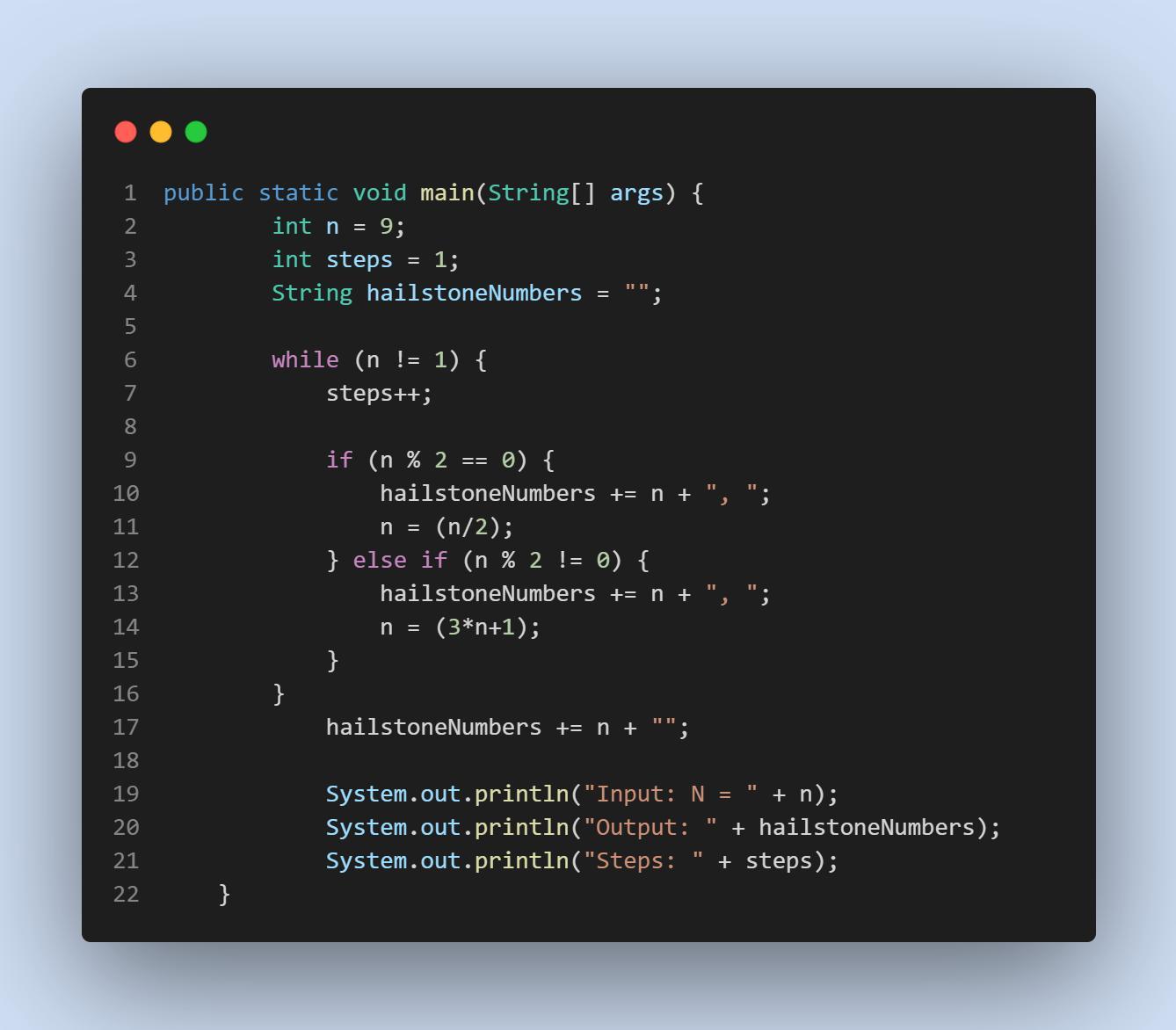
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
(a) Write down mathematical expressions for the values of European call and put options on a given security at expiry, explaining any terms that you use. Also, sketch the pay-off diagram in each case, assuming that there are transaction costs. () (b) Sketch the pay-off diagrams for each of the following portfolios, assuming that there are transaction costs: i. Short one share and long one call and three puts both with strike price K; () ii. Short one call with strike price 2K and short one call with strike price 4K, and long one call with strike price K; and (6 marks) iii. Short one call and short two puts both with strike price K and long one share. () (c) A portfolio consists of the following: long: 100 shares; 300 puts with strike price 115p;200 puts with strike price 100p; and short: 400 calls with strike price 110p;210 calls with strike price 195p. Assuming that the options all have the same expiry date, find the value of the portfolio at expiry if the share price is: i. 185p; ii. 195p; iii. 200p; or iv. 215p. ()
Answers
The question asks for mathematical expressions for European call and put options at expiry, and to sketch the pay-off diagrams considering transaction costs. Additionally, it requires the pay-off diagrams for specific portfolios with transaction costs and the valuation of a portfolio at different share prices.
a) The mathematical expressions for the values of European call and put options at expiry depend on various factors, including the underlying security price, strike price, time to expiry, risk-free rate, and volatility. The Black-Scholes model is commonly used to calculate option values. The pay-off diagram represents the profit or loss of an option at expiry as the underlying security price changes. The inclusion of transaction costs in the pay-off diagram considers the impact of buying or selling options.
b) i. The pay-off diagram for a short one share and long one call and three puts portfolio with the same strike price K would depend on the specific values of the options and the share price at expiry.
ii. The pay-off diagram for a portfolio with short one call with strike price 2K, short one call with strike price 4K, and long one call with strike price K would also depend on the specific values and share price at expiry.
iii. The pay-off diagram for a portfolio with short one call and short two puts with strike price K and long one share would be determined by the option values and share price at expiry.
c) To find the value of the given portfolio at expiry for different share prices, the specific values of the options and share price need to be considered. By calculating the pay-off for each option position and summing them based on the given quantities, the total portfolio value at expiry can be determined.
Learn more about transaction here: https://brainly.com/question/1016861
#SPJ11
combine the system calls (the second column) from the same pid (the first column) into a sequence or a string
Answers
By following the given steps, you can combine the system calls from the same pid into a sequence or string. This process provides an organized representation of the system calls based on the corresponding pid. Please note that the actual implementation might vary depending on the programming language or script you are using.
To combine the system calls from the same pid into a sequence or string, you can use a programming language or script. Here is an explanation of how you can achieve this in Python:
1. First, you need to read the input data containing the pid and system calls.
2. Create a dictionary where the pid will be the key and the system calls will be stored as values in a list.
3. Iterate through the input data and check if the pid already exists in the dictionary. If it does, append the system call to the existing list of system calls. If not, create a new key-value pair with the pid and the system call as the initial value.
4. After iterating through all the data, sort the system calls in each list according to their sequence or any desired order.
5. Finally, concatenate the sorted system calls for each pid into a string.
To know more about system calls visit:
brainly.com/question/13440584
#SPJ11
Find values of $a$, $b$, and $c$ so that the program: 1 a = # fill in 2 b = # fill in 3 c = # fill in 4 for i in range(a,b,c): 5 print(i, end=' ') outputs: 6 10 14 18 22 26 30 In the boxes below, put your value for $a$ in the first box, your value for $b$ in the middle box, and your value for $c$ in the bottom box.
Answers
Answer:
To find the values of $a$, $b$, and $c$ that satisfy the given program and output, we need to determine the pattern in the printed numbers and derive the corresponding values.
The program uses a for loop with a range that starts at $a$, ends at $b$ (exclusive), and increments by $c$. It then prints each value of $i$ in the range.
From the given output (6 10 14 18 22 26 30), we can observe that the numbers are increasing by 4 in each iteration.
Therefore, we can deduce the values of $a$, $b$, and $c$ as follows:
$a = 6$ (the first printed number)
$b = 31$ (the next number after the last printed number, which is 30, plus the increment of 4)
$c = 4$ (the constant difference between the numbers)
So, the values of $a$, $b$, and $c$ are:
$a = 6$
$b = 31$
$c = 4$
WILL GIVE BRAINLIEST!!!!
Casey overhears two people talking about an amazing new app. What phrase has been abbreviated when they talk about an “app”?
applied computer simulation
application software
appropriate usage format
applied technology
Answers
Answer:
Application Software
Answer:
application software
Explanation:
"Application software" is a common phrase nowadays that is being abbreviated as "app." Casey described the new app as "amazing," which means that the app could be a game, a browser, a photo editor or other programs that are deemed important and mostly exciting for the end users–people who are targeted by the software. In the situation above, they could be talking about a trendy app. New apps are being created by people over the course of years.
Different between school and university Tutorials
Answers
Answer:
A tutorial is a teaching session given to one student or a small group of students. If you are stuck in a class, you could use a tutorial. Teachers lead classes, but tutors are educators who also help students, usually one-on-one.
For each example given below, identify and write the type of data out of four choices:
Nominal data, Ordinal data, Interval data, and Ratio data. Mark N, O, I, or R
Salary, Nationality, Grade (A,B,C,D), Temperature
Answers
The type of data for each example is:
Salary: Ratio data (R)
Nationality: Nominal data (N)
Grade (A, B, C, D): Ordinal data (O)
Temperature: Interval data (I)
Salary: Ratio data (R) - Salary is a type of quantitative data that can be measured on a continuous scale. It has a meaningful zero point, allowing for meaningful comparisons and calculations. For example, if one person earns $50,000 and another person earns $100,000, we can say that the second person earns twice as much as the first person.
Nationality: Nominal data (N) - Nationality is a categorical variable that cannot be ranked or quantified. It is a form of qualitative data that represents different categories or groups. For example, someone can be of American, British, or Indian nationality, but we cannot assign a numerical value or order to these categories.
Grade (A, B, C, D): Ordinal data (O) - Grades are categorical variables that have a specific order or ranking. Although the actual difference between grades may not be consistent, we can still rank them from highest to lowest. For example, A is higher than B, B is higher than C, and so on.
Temperature: Interval data (I) - Temperature is a quantitative variable that can be measured on a continuous scale. However, it lacks a meaningful zero point. The interval between temperatures is consistent, but zero degrees does not indicate the absence of temperature. For example, the difference between 20 and 30 degrees Celsius is the same as the difference between 30 and 40 degrees Celsius, but 0 degrees Celsius does not mean "no temperature."
To know more about categorical variable visit:
https://brainly.com/question/32790259
#SPJ11
Can someone give me an example of previous experiences you've had that involved a model. These can be school related or from your personal life. explanation should include the context of the model (what was the setting and real-world use) and what the basic components of the model are. What assumptions are built into the model and what are the limits of the model, or what can the model fail to explain?
Answers
One example of a previous experience involving a model is building a solar system model for a school project.
The context of the model was an educational setting, specifically a science class where students were required to create a physical representation of the solar system. The main purpose was to help visualize the relative positions and sizes of the celestial bodies within the solar system and gain a better understanding of their distances from one another.
The solar system model, while a helpful educational tool, was not able to account for various factors such as the ongoing movement and rotation of the planets, the effects of gravity, or the complexities of each planet's atmosphere and geological features. Additionally, the model did not represent the numerous dwarf planets, minor planets, and other celestial objects that make up our solar system.
To know more about project visit;-
https://brainly.com/question/7953972
#SPJ11
A user calls and complains that she cannot access important company files from her personal device. You confirm that Intune policies are properly set up and assigned to her. What could be the issue that is blocking her from accessing the files
Answers
Answer:
A user calls and complains that she cannot access important company files from her personal device. You confirm that Intune policies are properly set up and assigned to her. What could be the issue that is blocking her from accessing the files? The user's device is rooted or jailbroken.
4. When setting the aperture, f2 is: *
Very large and lets in a small amount of light
Very small and lets in a large amount of light
Very small and lets in a small amount of light
Very large and lets in lots of light
Answers
Answer:
Very small and let's in a small amount of light
Which problem does IPv6 (Internet Protocol version 6) help to solve? A. IPv5 is an outdated protocol version with insufficient security safeguards. B. There are less than 4.3 billion IPv4 addresses, which has already been exceeded with existing websites. C. Internet Protocol versions prior to version 6 haven't achieved widespread use. D. Companies waste hundreds of public IP addresses. With IPv6, they can use just one IP address
Answers
IPv6 (Internet Protocol version 6) helps to solve the problem described in option B, which states that there are fewer than 4.3 billion IPv4 addresses, which has already been exceeded with existing websites. IPv4, the previous version of the Internet Protocol, uses 32-bit addresses, limiting the total number of unique IP addresses that can be assigned.
IPv6 introduces a 128-bit address space, allowing for a significantly larger number of unique addresses. With IPv6, there are approximately 3.4 × 10^38 possible addresses, which effectively eliminates the address exhaustion problem faced by IPv4.
By providing a vast address space, IPv6 enables the continued growth of the Internet and the increasing number of connected devices. It allows for the allocation of unique addresses to new devices and services without the need for complex network address translation (NAT) techniques.
Therefore, option B accurately represents the problem that IPv6 helps to solve, addressing the limitations of IPv4 addressing and enabling the scalability and expansion of the Internet.
To know more about network address translation,
https://brainly.com/question/13105976
#SPJ11
This Lab sheet is worth 10 points for complete queries. Only fully completed and documented solutions will receive maximum points. The queries are due per the timeline in Moodle. The queries in this homework assignment will use the Northwind database. Create an SQL query to solve the problem. Don't forget to include all of the following. 1. The database used "USE" 2. Comment with the assignment name, query number, your name and date. 3. The SQL code, in a readable, programmatic format. 4. Add a brief comment for each of the main segments, what the operation will accomplish 5. The output of the messages tab, to include the full "Completion time" or "Total Execution Time" line. 6. First 5 lines of the "Results" output. Points will be deducted if missing, more than 5 , or using the TOP command. 7. Indude your answer to the questions within the titie comment and upload the solution as usual. Follow the instructions in the Lab Lecture, complete the following queries. Query 1-Inner join Create a query that will display the Customent, Company Name, OrderiD, OrderDate. From the Customers and Orders tables. Once the query is created, answer the following question. Question - What will the results set represent? Query 2 - Outer Join Changing the inner join from query 1 to a left join, (Customers LEFT JOiN Orders) Create a query that will display the CustomeriD, Company Name, OrderiD, OrderDate. Once the query is created, answer the following question. Question - Looking thru the results set, you can see some "NUUL" entries. What does the "NUL" entries represent?
Answers
Database used: `USE Northwind` Lab Name: Lab 3
Query 1: Inner join, showing the Customers and Orders tables and displaying the Customer Name, Company Name, OrderID, and Order Date.
The results set will represent the customers with their orders, showing the Customer Name, Company Name, OrderID, and Order Date.
Query 2: Outer Join, displaying the CustomeriD, Company Name, OrderiD, OrderDate.
The "NUL" entries represent the customers that do not have any orders. Customers LEFT JOIN Orders would include all customers, including those who have never placed an order, unlike INNER JOIN, which only includes customers who have placed orders.
SQL code:```--Query 1
USE Northwind-- Ginny - Lab 3, Query 1
SELECT c.CustomerName, c.CompanyName, o.OrderID, o.OrderDate
FROM Customers c
INNER JOIN Orders o ON c.CustomerID = o.CustomerID```--
Query 2USE Northwind-- Ginny - Lab 3, Query 2
SELECT c.CustomerID, c.CompanyName, o.OrderID, o.OrderDate
FROM Customers cLEFT JOIN Orders o ON c.CustomerID = o.CustomerID```
The operation of the INNER JOIN will retrieve the records with matching values in both tables, while the operation of the LEFT JOIN retrieves all the records from the left table and matching records from the right table (Customers LEFT JOIN Orders).
Messages Output: Completion time: 0.034 seconds
Results Output: The first 5 lines of the results are:
CustomerName CompanyName OrderID OrderDate
Alfreds Futterkiste Alfreds Futterkiste 10643 1997-08-25
Ana Trujillo Emparedados y helados Ana Trujillo Emparedados y helados 10692 1997-10-03
Antonio Moreno Taquería Antonio Moreno Taquería 10308 1996-09-18
Antonio Moreno Taquería Antonio Moreno Taquería 10625 1997-08-08
Around the Horn Around the Horn 10365 1996-11-27
To know more about Database visit:
https://brainly.com/question/30163202
#SPJ11
i will mark brainalist!

Answers
Answer:
I would say
1) Weather Station
2) (word missing)
3) Robot perihen devices
4) Bit
5) Primary Key
6) Algorithim
7) Flow Chart
8) Table Wizard
9) Design View
10) SIMS
Answer:
i think it would be 1) Weather Station
2) (word missing)
3) Robot perihen devices
4) Bit
5) Primary Key
6) Algorithim
7) Flow Chart
8) Table Wizard
9) Design View
10) SIMS
Explanation:
URGENT HTML5 can support videos and audio playback, but not 2D and 3D graphics.
A. True
B. False
Answers
Answer:
False I think.
Explanation:
After selecting the entire document what is the quickest way to find out how many paragraphs.
Answers
assume you want to create a class friend and you want to specify that a friend is a human (you want to specify that there is an inheritance relationship between class friend and class human) which keyword should you use in the class declaration to specify that there is an inheritance relationship between the two classes?
Answers
There are various inheritance patterns, including hierarchical inheritance, multiple inheritance, multilevel inheritance, and single inheritance.
What is inheritance?Genetic information is transmitted from parent to kid through inheritance. Members of the same family typically share traits in common because of this.
Examine 5 Different Types of Inheritance Using Examples in C++
Individual Inheritance.Several inheritances.inheritance on multiple levels.inheritance in a hierarchy.Inheritance hybrid.As it relates to genetics, the term "inherited" describes a feature or variation that is encoded in DNA and passed from parent to child during reproduction. The laws of Mendelian genetics govern inheritance.
The final keyword in a class' declaration can be used to prevent subclassing of that class. Similarly, by designating a method as a final method, you can stop subclasses from overriding it.
To learn more about inheritance refer to:
https://brainly.com/question/15078897
#SPJ4
what is the main disadvantage of a poll? a. power b. can not set priorities c. no way to mask it d. no hardware support e. too complicated g
Answers
A poll's primary drawback is its power. This method's main drawback is how slowly it works.
What is poll ?
The drawback of polling is that if there are too many devices to check, it may take longer to service an I/O device than it does to poll all of the devices. By asking a series of questions and extending generalisations into ratios or confidence intervals, opinion polls are often created to represent the opinions of a population. Pollster is a term used to describe someone who conducts polls. Maximum effectiveness and bandwidth use are the results. Polling is the process through which one programme continuously checks other programmes or devices.
To learn more about Pollster from given link
brainly.com/question/2729655
#SPJ4
If you try to add a string to an integer, which error will result?
A.
LogicError
B.
NameError
C.
FunctionError
D.
TypeError
Answers
The error that will result from trying to add a string to an integer is option D. Type Error.
This is because a string and an integer are two different data types, and you cannot perform arithmetic operations between them without first converting one of them to the same data type as the other.
A Type Error occurs when there is a mismatch between the data types of the variables being used in an operation or function call. In this case, the operation of adding a string and an integer is not defined, and Python does not know how to perform it. As a result, Python raises a Type Error to indicate that the operation is invalid.
To avoid Type Errors, it is important to ensure that the data types of the variables being used in an operation are compatible. If you need to add a string and an integer, you can convert the integer to a string using the str() function, and then concatenate the two strings using the + operator.
Alternatively, if you need to perform arithmetic operations on the integer, you can convert the string to an integer using the int() function before operation. Therefore the correct option D
Know more about Error here:
https://brainly.com/question/17101515
#SPJ11
Text,Audio and graphic is entered into the computer using
a)A cpu
b)Output
C)Input
ICT Question asap pls help
Answers
Answer:
I think it's input, not sure tho
When downloading a large file from the iniernet Alexis interrupted the download by closing ber computer, Later that evening she resumed tbe download and noticed that the file was bowniosding at a constant rate of change. 3 minutes since resaming the download 7440 total MegaBytes (MB) of the file had been downloaded and 6 mintues siace resuming the download 13920 total MesaBytes (MB) of the file had been donstoaded A. From 3 to 6 minutes after she resumed downlooding, how many minutcs elapod? misules b. From 3 to 6 minutes after she resumed downloading, how many total MB of the file were dowaloaded? MB c. What is the consuant rate at which the file downloads? MegaByes per minule d. If the file continues downloadisg for an additional 1.5 minner (after tbe 6 mimutes afts she feramed downloading). 4. How many aditipeal MB of the flie were downloaded? MIB 14. What is the new total number of MB of the file Bhat have been downloaded? MEI
Answers
a) From 3 to 6 minutes after resuming the download, 3 minutes elapsed.
b) From 3 to 6 minutes after resuming the download, 6,480 MB of the file were downloaded.
c) The constant rate at which the file downloads is 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, an additional 3,240 MB of the file will be downloaded.
e) The new total number of MB of the file that have been downloaded will be 17,160 MB.
a) From the given information, we can determine the time elapsed by subtracting the starting time (3 minutes) from the ending time (6 minutes), resulting in 3 minutes.
b) To calculate the total MB downloaded, we subtract the initial downloaded amount (7,440 MB) from the final downloaded amount (13,920 MB). Therefore, 13,920 MB - 7,440 MB = 6,480 MB were downloaded from 3 to 6 minutes after resuming the download.
c) The constant rate at which the file downloads can be found by dividing the total MB downloaded (6,480 MB) by the elapsed time (3 minutes). Therefore, 6,480 MB / 3 minutes = 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, we can calculate the additional MB downloaded by multiplying the constant rate of download (2,160 MB per minute) by the additional time (1.5 minutes). Hence, 2,160 MB per minute * 1.5 minutes = 3,240 MB.
e) The new total number of MB of the file that have been downloaded can be found by adding the initial downloaded amount (7,440 MB), the MB downloaded from 3 to 6 minutes (6,480 MB), and the additional MB downloaded (3,240 MB). Thus, 7,440 MB + 6,480 MB + 3,240 MB = 17,160 MB.
In summary, Alexis resumed the download and observed a constant rate of download. By analyzing the given information, we determined the time elapsed, the total MB downloaded, the rate of download, the additional MB downloaded, and the new total number of MB downloaded. These calculations provide a clear understanding of the file download progress.
Learn more about constant rate
brainly.com/question/32636092
#SPJ11
which of the following types of constraints is used to enforce referential integrity?
Answers
The type of constraint used to enforce referential integrity is the Foreign Key constraint. The purpose of foreign key constraints is to ensure that the values in the foreign key column(s) match the values in the referenced primary key column(s).
A foreign key is a column or a set of columns in a database table that refers to the primary key of another table. It establishes a relationship between two tables, where the values in the foreign key column(s) must match the values in the referenced primary key column(s).
By defining a foreign key constraint, you ensure that the values in the foreign key column(s) of a table are valid and exist in the referenced primary key column(s) of another table.
This constraint helps maintain data integrity and prevents inconsistencies or orphaned records in relational databases. So foreign key is used to enforce the referential integrity.
To learn more about referential integrity: https://brainly.com/question/17128955
#SPJ11
Whenever you create the instance of subclass, an instance of parent class is created implicitly which is referred by super reference variable.
Answers
Whenever you create an instance of a subclass, an instance of the parent class is implicitly created as well. This instance is referred to by the super reference variable, allowing the subclass to access and utilize the properties and methods of the parent class.
Yes, when you create an instance of a subclass in Java, an instance of the parent class is created implicitly as well. This parent class instance is referred to by the "super" reference variable within the subclass. This allows the subclass to inherit all of the methods and properties of the parent class, while also having its own unique functionality. It is important to note that the parent class constructor is called automatically when creating the subclass instance, and any arguments passed to the subclass constructor are forwarded to the parent class constructor using the "super" keyword.
Learn more about subclass here:-
https://brainly.com/question/13790787
#SPJ11
which one of the following is not hardware
Answers
Answer:
There r no options
Explanation:
I think the application r not the hardware.