A website developer is working on a new e-commerce website and has asked an information security expert for the most appropriate way to store credit card numbers to create an easy reordering process. Which of the following methods would BEST accomplish this goal?
A. Salting the magnetic strip information
B. Encrypting the credit card information in transit
C. Hashing the credit card numbers upon entry
D. Tokenizing the credit cards in the database
Answers
The BEST way to achieve this would be to tokenize the credit cards in the database methods.
Which of the following best distinguishes a data owner from a data custodian?While the data custodian is in charge of data backup, retention, and recovery, the data owners are largely responsible for setting the data's sensitivity or classification levels. These duties are given to the custodian by the data owner.
A risk register is used for which of the following?To identify potential setbacks in a project, a risk register is a record that is used in risk management. Prior to problems developing, this method seeks to collectively detect, assess, and resolve risks.
To know more about database visit :-
https://brainly.com/question/6447559
#SPJ4
Related Questions
As you know computer system stores all types of data as stream of binary digits (0 and 1). This also includes the numbers having fractional values, where placement of radix point is also incorporated along with the binary representation of the value. There are different approaches available in the literature to store the numbers having fractional part. One such method, called Floating-point notation is discussed in your week 03 lessons. The floating point representation need to incorporate three things:
• Sign
• Mantissa
• Exponent
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-
point notation.
B. Determine the smallest (lowest) negative value which can be
incorporated/represented using the 8-bit floating point notation.
C. Determine the largest (highest) positive value which can be
incorporated/represented using the 8- bit floating point notation.
Answers
Answer:
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-point notation.
First, let's convert -9/2 to a decimal number: -9/2 = -4.5
Now, let's encode -4.5 using the 8-bit floating-point notation. We'll use the following format for 8-bit floating-point representation:
1 bit for the sign (S), 3 bits for the exponent (E), and 4 bits for the mantissa (M): SEEE MMMM
Sign bit: Since the number is negative, the sign bit is 1: 1
Mantissa and exponent: Convert -4.5 into binary and normalize it:
-4.5 in binary is -100.1. Normalize it to get the mantissa and exponent: -1.001 * 2^2
Mantissa (M): 001 (ignoring the leading 1 and taking the next 4 bits)
Exponent (E): To store the exponent (2) in 3 bits with a bias of 3, add the bias to the exponent: 2 + 3 = 5. Now, convert 5 to binary: 101
Now, put the sign, exponent, and mantissa together: 1101 0010
So, the 8-bit floating-point representation of -9/2 (-4.5) is 1101 0010.
B. Determine the smallest (lowest) negative value which can be incorporated/represented using the 8-bit floating-point notation.
To get the smallest negative value, we'll set the sign bit to 1 (negative), use the smallest possible exponent (excluding subnormal numbers), and the smallest mantissa:
Sign bit: 1
Exponent: Smallest exponent is 001 (biased by 3, so the actual exponent is -2)
Mantissa: Smallest mantissa is 0000
The 8-bit representation is 1001 0000. Converting this to decimal:
-1 * 2^{-2} * 1.0000 which is -0.25.
The smallest (lowest) negative value that can be represented using the 8-bit floating-point notation is -0.25.
C. Determine the largest (highest) positive value which can be incorporated/represented using the 8-bit floating-point notation.
To get the largest positive value, we'll set the sign bit to 0 (positive), use the largest possible exponent (excluding infinity), and the largest mantissa:
Sign bit: 0
Exponent: Largest exponent is 110 (biased by 3, so the actual exponent is 3)
Mantissa: Largest mantissa is 1111
The 8-bit representation is 0110 1111. Converting this to decimal:
1 * 2^3 * 1.1111 which is approximately 1 * 8 * 1.9375 = 15.5.
The largest (highest) positive value that can be represented using the 8-bit floating-point notation is 15.5.
Explanation:
4. (15 points) Give an algorithm that takes as input a positive integer n and a number x, and computes xn (i.e., x raised to the power n) by performing O(lgn) multiplications. Your algorithm CANNOT use the exponentiation operation, and may use only the basic arithmetic operations (addition, subtraction, multiplication, division, modulo). Moreover, the total number of basic arithmetic operations used should be O(lgn).
Answers
Answer:
The algorithm is as follows:
Exponent(x, n):
if(n == 0):
return 1
pr = Exponent(x, int(n / 2))
if (n % 2 == 0):
Return pr* pr
else:
if(n > 0):
Return x * pr* pr
else:
Return (pr* pr) / x
Explanation:
In order to get a O(log n) time complexity, a recursive procedure is implemented by the algorithm
The algorithm begins here
Exponent(x, n):
If n is 0, the procedure returns 1
if(n == 0):
return 1
This recursively calculates the product of x, n/2 times
pr= Exponent(x, int(n / 2))
If n is even, the square of prod (above) is calculated
if (n % 2 == 0):
Return pr* pr
If otherwise (i.e. odd)
else:
If n is above 0, the square of prod multiplied by x is calculated
if(n > 0):
Return x * pr* pr
If otherwise, the square of prod divide by x is calculated
else:
Return (\(pr* pr\)) / x
The time complexity is: O(log|n|)
Please! Someone help me write a c++ program without using double and should outcome the expected output like in the image provided.


Answers
The C++ program without using double and should outcome what is in the image is given below:
The Program#include <iostream>
using namespace std;
int main() {
int hour, minute;
cin >> hour >> minute;
if (hour >= 12) {
if (hour > 12) hour -= 12;
cout << hour << ":" << minute << " PM" << endl;
} else {
if (hour == 0) hour = 12;
cout << hour << ":" << minute << " AM" << endl;
}
return 0;
}
Read more about programs here:
https://brainly.com/question/26497128
#SPJ1
What is a common goal of an organization when implementing an Agile mindset?
Answers
A common goal of an organization when implementing an Agile mindset is to give their staff the freedom to perform their best work.
What is an Agile mindset?One common goal of an organization when implementing an Agile mindset is to improve the speed and flexibility of its development process.
Agile is a project management approach that emphasizes iterative, incremental progress and the ability to adapt to change. By adopting an Agile mindset, an organization can more easily respond to changing customer needs and market conditions, and deliver value more quickly.
Other common goals of an organization when implementing an Agile mindset include:
Increasing collaboration and transparency: Agile emphasizes close collaboration between team members and stakeholders, and promotes open communication and transparency. By adopting an Agile mindset, an organization can foster a culture of collaboration and trust.Improving quality: Agile approaches often include frequent testing and feedback loops, which can help improve the quality of the end product.Therefore, the goal of an organization when implementing an Agile mindset is to become more agile and responsive, and to be better able to deliver value to customers in a rapidly changing world.
Learn more about Agile mindset from
https://brainly.com/question/29307421
#SPJ1
Explain how the entity relationship (ER) model helped produce a more structured
relational database design environment.
Answers
The way that the entity relationship (ER) model helped produce a more structured relational database design environment is that
A database's primary entities and their relationships can be determined with the aid of an entity relationship model, or ERM. The role of the ERM components is easier to comprehend because they are graphically portrayed.
It is simple to translate the ERM to the tables and attributes of the relational database model using the ER diagram. The full set of needed database structures is generated by this mapping procedure, follows a set of clearly defined processes which are:
uses clearly defined images and rules to represent reality.the theoretical basisbeneficial for communicationTranslate to any DBMS typeHow does the ER model aid in relational database design?A visual representation of relational databases is an entity relationship diagram (ERD). Relational databases are modeled and designed using ERDs.
The Entity Relationship Model (ERM), which enables designers to perceive entities and connections visually, contributed to the creation of a more structured relational database design environment.
Therefore, Instead of defining the structures in the text, it is easier to understand them graphically.
Learn more about entity relationship (ER) model from
https://brainly.com/question/14424264
#SPJ1
which of the following events happen first
web 2.0 had evolved
ARPANET was developed
The world wide web was created
Email was invented
Answers
Answer:
Hey! The answer your looking for is ARPANET:)
Explanation:
Answer:
ARPANET was developed
Explanation:
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
Answers
Answer: NAT
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP? One-to-many NAT allows multiple devices on a private network to share a single public IP address.
The following that allows for hundreds of computers all to have their outbound traffic translated to a single IP is the One-to-many NAT. Option C
How does One-to-many NAT works
One-to-many NAT allows hundreds of computers to have their outbound traffic translated to a single IP this is done by designating each computer to a unique port number, that is used to identify the specific device within the the network address transition NAT, where all private network gain access to public network .
The NAT device serves as translator, keeping track of the original source IP and port number in the translation table, translates the source IP address and port number of each outgoing packet to the single public IP address, This allows for a possible multiple devices to share a single IP address for outbound connections.
Learn more about One-to-many NAT on brainly.com/question/30001728
#SPJ2
The complete question with the options
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
a. Rewriting
b. Port forwarding
c. One-to-many NAT
d. Preservation
Help pls
Which argument is not a default filter for data?
O Does Not Equal
O Above Average
O Less Than
O Top 50
Answers
Top 50 argument is not a default filter for data. Option D is correct.
What is the default filter?Default Workbooks Filters are set. These are also known as Dashboards. The default filters are always used when emailing dashboards. Select the filter options that want to use as the default choices before setting any default filters.
When all desired options are selected, you can click “Set As Default” to make the selected options the default filter view.
Setting default filters on the dashboard ensures that the same filters will be applied to everyone accessing the page for the first time. Top 50 argument is not a standard data filter.
Therefore, option D is correct.
Learn more about default filter, refer to:
https://brainly.com/question/28702414
#SPJ1
Which function is used to display a string value to the screen?
main[]
print()
run=
SHOW!
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
in most programming languages, the print() function is used to display a string value to the screen. Because, the print function prints all the string given in it as a parameter.
for example: to print hello world.
we use the function to print hello world as print("hello world").
However, it noted that other options are not correct because the main() function is an entry point of a program and it does not print string value to the screen. while run and show function do not print string value of screen also.
Answer:
in python print()
Which of these is not a way of avoiding email fraud and scam?

Answers
Answer:
The third one definitely (If you aren't sure where it goes click it) Ur in college right
Explanation:
I am having trouble figuring out how to write a code to complete this assignment in Python:
Implement the build_dictionary() function to build a word frequency dictionary from a list of words.
Ex: If the words list is:
["hey", "hi", "Mark", "hi", "mark"]
the dictionary returned from calling build_dictionary(words) is:
{'hey': 1, 'hi': 2, 'Mark': 1, 'mark': 1}
Ex: If the words list is:
["zyBooks", "now", "zyBooks", "later", "zyBooks", "forever"]
the dictionary returned from calling build_dictionary(words) is:
{'zyBooks': 3, 'now': 1, 'later': 1, 'forever': 1}
The main code builds the word list from an input string, calls build_dictionary() to build the dictionary, and displays the dictionary sorted by key value.
Ex: If the input is:
hey hi Mark hi mark
the output is:
Mark: 1
hey: 1
hi: 2
mark: 1
This is what I have been given:
# The words parameter is a list of strings.
def build_dictionary(words):
# The frequencies dictionary will be built with your code below.
# Each key is a word string and the corresponding value is an integer
# indicating that word's frequency.
'''your code goes here'''
# The following code asks for input, splits the input into a word list,
# calls build_dictionary(), and displays the contents sorted by key.
if __name__ == '__main__':
words = input().split()
your_dictionary = build_dictionary(words)
sorted_keys = sorted(your_dictionary.keys())
for key in sorted_keys:
print(key + ': ' + str(your_dictionary[key]))
Answers
Answer:
def build_dictionary(words):
dic = {}
for word in words:
dic [word] =words.count(word)
return(dic)
if __name__ == '__main__':
words = input().split()
your_dictionary = build_dictionary(words)
sorted_keys = sorted(your_dictionary.keys())
for key in sorted_keys:
print(key + ': ' + str(your_dictionary[key]))
Explanation:
use the count function cause the initial input is a list.
Following are the Python program code to count the list of word in the dictionary:
Python Program to count list of words:def build_dictionary(words):#defining the method build_dictionary that takes words as a parameter
f = {}#defining a variable dictionary as a f
for i in words:#defining a loop that checks dictionary value
if (i in f):#defining an if block that check dictionary value
f[i] += 1#addining 1 in the value of list
else:#defining else block
f[i] = 1#holding 1 in the list
return f#return list value
if __name__ == '__main__':
words = input().split()#defining a variable words that input value and splits its value
your_dictionary = build_dictionary(words)#defining a variable your_dictionary that adds value in build_dictionary
sorted_keys = sorted(your_dictionary.keys())#defining variable sorted_keys that sort value your_dictionary as key
for k in sorted_keys:#defining loop that counts number of value
print(k + ': ' + str(your_dictionary[k]))#defining print method that prints its value
Output:
Please find the attached file.
Program Explanation:
Defining the method "build_dictionary" that takes one parameter "words" in the method. Inside this method, a dictionary variable named "f" is declared in which a for loop is declared. Inside this, a conditional block is declared that counts words' value.In the next step, a constructor is declared, in which words variable is declared that input value and splits its value.In the next step, "your_dictionary" is declared that that adds value to build_dictionary, and use stored method is used that sort its value and store its value in "sorted_keys".After that, a for loop is declared that counts the "sorted_keys" dictionary value and prints its counted list value.
Find out more information about the dictionary here:
brainly.com/question/1199071

Three years later, you're still consulting for CNT Books. The network has more than 15 subnets and 10 routers in several buildings and locations. You have been keeping up with the network by configuring the routers statically. However users have had problems with downtime in the past year because of network links going off line, as there's only one route to reach every subnet. The owner wants fault tolerance built into the network to include back up links in case a primary link goes offline. You're concerned that the current router configuration method will still cause some downtime, even if the backup links operate correctly. Why might there be downtime if a primary link goes offline but the backup link is ok? What can you do to reduce the possibility of downtime?
Answers
There may be downtime if a primary link goes offline but the backup link is ok because the router configuration is static, meaning the router will not automatically detect the new backup link and switch to it.
What is the configuration ?Configuration is the way in which components of a system or a network are connected and arranged. It is the specific arrangement of hardware, software, networks and other components that make up a system or a network. It is also the process of setting up or organizing the components of a system so that they can properly interact with one another and perform as expected. Configuration can refer to anything from the configuration of a single computer to the configuration of a large-scale computer network. Configuration also includes the setup of applications, services and databases that are used in the system or network.
To learn more about configuration
https://brainly.com/question/9978288
#SPJ1
How did early computing device such as Charles Babbage's analytical engine and Ada Lovelace's contributions set the foundation for modern computing
Answers
Early computing devices, such as Charles Babbage's Analytical Engine and Ada Lovelace's contributions, played a crucial role in setting the foundation for modern computing. Here's how their work contributed to computing development:
1. Charles Babbage's Analytical Engine: Babbage designed the Analytical Engine, a mechanical general-purpose computer concept, in the 19th century. Although the Analytical Engine was never fully built, its design and principles laid the groundwork for modern computers. Key features of the analytical engine include:
a. Stored Program: Babbage's Analytical Engine introduced the concept of storing instructions and data in memory, allowing complex calculations and tasks.
b. Control Flow: The Analytical Engine could make decisions and perform conditional operations based on previous computations, resembling the modern concept of control flow in programming.
c. Loops: Babbage's design incorporated looping mechanisms, enabling repetitive instruction execution, similar to modern programming languages.
2. Ada Lovelace's Contributions: Ada Lovelace, an English mathematician, collaborated with Charles Babbage and made significant contributions to computing. Her work on Babbage's Analytical Engine included writing the first algorithm intended for machine implementation. Lovelace realized the potential of the analytical engine beyond numerical calculations and recognized its capability for processing symbols and creating complex algorithms. Her insights laid the foundation for computer programming and algorithms.
Lovelace's ideas about the analytical engine extended beyond what was initially envisioned. He stressed the importance of machines handling more than just numbers. Her contributions demonstrated computers' potential to perform tasks beyond basic calculations and numerical processing.
Collectively, Babbage's analytical engine and Lovelace's contributions provided early conceptual frameworks for modern computing. Their ideas influenced subsequent pioneers in the field, and the concepts they introduced paved the way for the development of the digital computers we use today.
how many ways are there to permute the letters in each of the following words? (a) number (b) discrete (c) subsets
Answers
The permutations for each word are:
(a) number - 8! = 40,320(b) discrete - 8! = 40,320(c) subsets - 6! = 720Understanding Permutations: A Guide to Counting Possible CombinationsPermutations are a powerful tool for calculating the number of possible arrangements of a given set of items. Whether it is a set of letters, numbers, or other objects, understanding how to calculate the number of possible permutations can help to solve a variety of problems. This essay will provide a guide to understanding and calculating permutations, focusing on the three examples given above.
To begin, permutations involve rearranging a set of items in different combinations, or orders. This rearrangement is done without replacement, meaning that each item can only be used once in each permutation. For example, when permuting the letters in the word "number," each letter can only be used once, and it cannot be repeated. To calculate the number of permutations, the formula n! (where n is the number of items in the set) is used. Applying this formula to the three examples given produces the results shown above.
Learn more about Permutations :
https://brainly.com/question/1216161
#SPJ4
Use the class below to determine IF there is an error or if some part of the code is missing.
public class acceptInput {
public static void main (String[ ] args) {
Scanner scan = new Scanner (System.in);
System.out.println("How old are you? ");
int age = scan.nextInt();
System.out.println("Wow you are " + age + " years old. ");
}
}
- Scanner object has been declared incorrectly
- .nextInteger() should be used to accept an integer from the user.
- Age variable is not correctly printed in the sentence
- import java.util.Scanner; is missing
- Program runs as expected
Answers
Based on the given class below:
public class acceptInput {
public static void main (String[ ] args) {
Scanner scan = new Scanner (System.in);
System.out.println("How old are you? ");
int age = scan.nextInt();
System.out.println("Wow you are " + age + " years old. ");
}
}
The error that can be seen here is that the Scanner object has not been created
What is Debugging?This refers to the term that is used to describe finding errors in a given program or system that prevents a code from properly executing and involves certain steps and processes.
Hence, it can be seen that the error in the code above is that there is the use of the Scanner object, but it is yet to be created which would return errors when the program is being run.
Read more about debugging here:
https://brainly.com/question/15079851
#SPJ1
Help me with this plzz
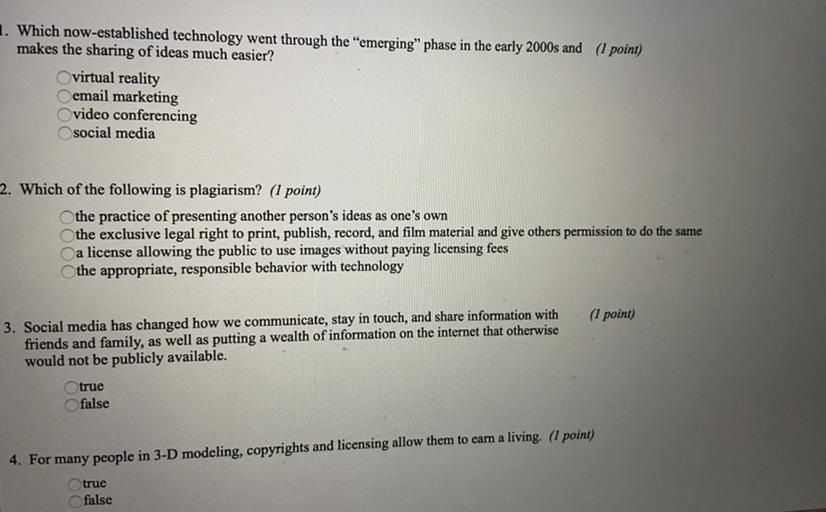
Answers
Answer:
the 1st one I believe
Explanation:
because plagiarism means to copy someone else work without permission. Example- if you are writing an essay and copy something off the internet and call it your own that's plagiarism
Answer:
Yeap you are right. The correct ans is the 1st one.
Plagiarism is the representation of another author's language, thoughts, ideas, or expressions as one's own original work.
state the base of correct addition of 27 + 6 =34
Answers
Answer:
9
Explanation:
lets do calculations with ONLY the rightmost digits, ie., 7 + 6 = 4, so we're ignoring the carry.
Then, following must be true as well:
7+5 = 3
7+4 = 2
7+3 = 1
7+2 = 0 <= this reveals our base 9
7+1 = 8
7+0 = 7
Which of the following is an example of critical reading?
Select all that apply:
Accepting textual claims at face value Considering an argument from a different point of view
Reviewing an argument to identify potential biases
Skimming a text to locate spelling errors or typos
Looking for ideas or concepts that confirm your beliefs
Answers
Answer:
Which of the following is an example of critical reading? Select all that apply:
a.Accepting textual claims at face valueb.Considering an argument from a different point of viewc. Reviewing an argument to identify potential biasesd. Skimming a text to locate spelling errors or typose. Looking for ideas or concepts that confirm your beliefs
Select the correct answer from each drop-down menu.
Tanya wants to include an instructional video with all its controls on her office website. The dimensions of the video are as follows:
width="260"
height="200"
What code should Tanya use to insert the video?
To insert the video, Tanya should add the following code:
✓="video/mp4">

Answers
The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
How to explain the informationTanya can use the following code to insert the video with all its controls on her office website:
<video width="260" height="200" controls>
<source src="video.mp4" type="video/mp4">
<source src="video.ogg" type="video/ogg">
Your browser does not support the video tag.
</video>
The width and height attributes specify the dimensions of the video player. The controls attribute specifies that the video player should display all its controls. The source elements specify the location of the video files.
The first source element specifies the location of the MP4 file, and the second source element specifies the location of the Ogg file. The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Programming CRe-type the code and fix any errors. The code should convert non-positive numbers to 1.
if (userNum > 0)
printf("Positive.\n");
else
printf("Non-positive, converting to 1.\n");
user Num = 1;
printf("Final: %d\n", userNum);
1 #include Hem
int main(void) {
int userNum;
scanf("%d", &userNum);
return 0;
Answers
Answer:
Given
The above lines of code
Required
Rearrange.
The code is re-arrange d as follows;.
#include<iostream>
int main()
{
int userNum;
scanf("%d", &userNum);
if (userNum > 0)
{
printf("Positive.\n");
}
else
{
printf("Non-positive, converting to 1.\n");
userNum = 1;
printf("Final: %d\n", userNum);
}
return 0;
}
When rearranging lines of codes. one has to be mindful of the programming language, the syntax of the language and control structures in the code;
One should take note of the variable declarations and usage
See attachment for .cpp file
Write a three paragraph essay on the best rotary-wing aircraft. You can pick the aircraft based on your opinion, but you must explain why you picked it.
Answers
Answer:
Humans' initial desire for flight stems from the imitation of flying creatures in nature. The excellent flight performance of flying animals will inevitably become a source of inspiration for researchers. Bio-inspired flight systems have become one of the most exciting disruptive aviation technologies. This review is focused on the recent progresses in bio-inspired flight systems and bionic aerodynamics. First, the development path of Biomimetic Air Vehicles (BAVs) for bio-inspired flight systems and the latest mimetic progress are summarized. The advances of the flight principles of several natural creatures are then introduced, from the perspective of bionic aerodynamics. Finally, several new challenges of bionic aerodynamics are proposed for the autonomy and intelligent development trend of the bio-inspired smart aircraft. This review will provide an important insight in designing new biomimetic air vehicles.
Explanation:
there you go
what does I/O mean in computing
Answers
Explanation:
I/O (input/output)" describes any operation, program, or device that transfers data to or from a computer
The following do-while loop is suppose to ask for the price for a gallon of gas. The price must a positive number. The price can be an integer value or a double value. for example the price can be 3 or 3.0 or 3.5.
To create a robust program, we must do the data validation and as long as the user is entering a negative value or a String, the program must keep asking the user to enter a valid input.
in this program you need to use some of the scanner methods listed here, make sure to use the proper ones: hasNextInt(), hasNextDouble(), hasNextLine(), hasNext(), nextInt(), nextDouble(), nextLine()
Must flush the buffer at the proper locations in the code
Answers
Answer:
import java.util.Scanner;
public class qs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
double price;
do {
System.out.print("Enter the price for a gallon of gas: ");
while (!input.hasNextDouble()) {
System.out.println("That's not a number!");
input.next(); // this is important!
}
price = input.nextDouble();
} while (price < 0);
System.out.println("The price is " + price);
}
}
Need help asap
give the correct answer!!

Answers
Answer:
C
Explanation:
Coding provides the robot directions, or instructions of what to do.
what is the difference between hydra and hadoop?
Answers
Hadoop is batch oriented whereas Hydra supports both real-time as well as batch orientation.
The Hadoop library is a framework that allows the distribution of the processing of large data maps across clusters of computers using simple as well as complex programming models. batch-oriented analytics tool to an ecosystem full of multiple sellers in its own orientation, applications, tools, devices, and services has coincided with the rise of the big data market.
What is Hydra?
It’s a distributing multi - task-processing management system that supports batch operations as well as streaming in one go. It uses the help of a tree-based data structure and log algorithms to store data as well as process them across clusters with thousands of individual nodes and vertexes.
Hydra features a Linux-based file system In addition to a job/client management component that automatically allocates new jobs to the cluster and re-schedules the jobs.Know more about Big Data: https://brainly.com/question/28333051
ed 4. As a network administrator of Wheeling Communications, you must ensure that the switches used in the organization are secured and there is trusted access to the entire network. To maintain this security standard, you have decided to disable all the unused physical and virtual ports on your Huawei switches. Which one of the following commands will you use to bring your plan to action? a. shutdown b. switchport port-security c. port-security d. disable
Answers
To disable unused physical and virtual ports on Huawei switches, the command you would use is " shutdown"
How doe this work?The "shutdown" command is used to administratively disable a specific port on a switch.
By issuing this command on the unused ports, you effectively disable those ports, preventing any network traffic from passing through them.
This helps enhance security by closing off access to unused ports, reducing the potential attack surface and unauthorized access to the network.
Therefore, the correct command in this scenario would be "shutdown."
Learn more about virtual ports:
https://brainly.com/question/29848607
#SPJ1
if you want to learn how to perform an action, which feature of the excel window should you use
Answers
To learn how to perform an action on Excel Window, the feature you should use is the "Tell Me What To Do" Feature. It can be found on the top right corner above all the ribbons after "Help". This can be activated using the keyboard shortcut keys "Alt + Q".
What is Excel Window?Excel is a popular spreadsheet system that manages data into columns and rows that can be manipulated using formulas that allow the software to perform mathematical functions on the data.
It is software created by Microsoft that uses spreadsheets to organize numbers and data with formulas and functions. Excel analytics is ubiquitous around the world and is used by companies of all sizes for financial analysis
Learn more about Excel:
https://brainly.com/question/25879801
#SPJ1
Please don't answer if you don't know Type the correct answer in the box
. Spell all words correctly. How does SQA differ from SQC? SQA involves activities to evaluate software processes, and SQC involves activities that ensure quality software.
Answers
Software Quality Assurance (SQA) and Software Quality Control (SQC) are two distinct aspects of quality management in software development, each with its own focus and activities.
How different are they?SQA encompasses efforts directed toward assessing and enhancing the procedures of software development at every stage. The main emphasis is on guaranteeing that appropriate techniques, norms, and protocols are adhered to in order to create software of superior quality. SQA encompasses various tasks, including scrutinizing requirements, conducting process audits, and administering quality control procedures.
Conversely, SQC pertains to actions that prioritize assuring the quality of the actual software product. This involves employing methods such as testing, inspections, and reviews in order to detect flaws and guarantee that the software satisfies the stated demands and standards. The goal of SQC is to identify and rectify any shortcomings or irregularities within the software product.
To put it succinctly, SQA focuses on assessing and enhancing the manner in which software is developed, while SQC is primarily focused on verifying the excellence of the resulting software product. SQC and SQA both play a vital role in attaining an optimum level of software quality.
Read more about software here:
https://brainly.com/question/28224061
#SPJ1
Which of these is NOT a mathematical operator used in Python?
A. !
B. /
C. %
D. *
Answers
Explain these five exffects of moisture on smart and modern materials. The materials: 2. Photochromic pigment 1.Thermochromic pigment 3. Shape memory polymer 4. Shape memory Alloy 5.Hydrogels
Answers
Smart materials are referred to as "reactive materials." Exposure to stimuli like as electric and magnetic fields, stress, moisture, and temperature can alter their characteristics.
Explain these five effects of moisture on smart and modern materials?Photochromic pigment—When exposed to light, photochromic pigments change color. Thermochromic pigment-When the temperature of thermochromic pigments shifts, the color changes. Shape memory polymer- Shape-memory Polymers are clever synthetic polymers that may return to their original shape after being deformed.Shape memory Alloy - Shape-memory alloys are metals that, even when distorted below a certain temperature, retain their shape.Hydrogels- A hydrogel is a three-dimensional system of hydrophilic polymers that can swell and absorb a lot of water.Thus, Smart materials are referred to as "reactive materials
For more information about Smart materials, click here:
https://brainly.com/question/2987553
#SPJ1