A hardware device that is used to store data and programs in a computer system is a(n)___
input device
output device
storage device
processing device
scanning device
Answers
Answer:
answer is storage device
Related Questions
the size of a font is measured in
Answers
Answer:
Point
Explanation:
point (pt)
A font is typically measured in a point (pt) size, which is the vertical measurement of the lettering. There are approximately 72 (72.272) points in one inch or 2.54 cm. In the picture to the right are examples of font sizes 6pt to 84 pt.
Write a statement that stores a number, 55.0, in the last column of the last row in the array.
Answers
To store the number 55.0 in the last column of the last row in the array, you can use the following statement:
array[array.length - 1][array[0].length - 1] = 55.0.
Here are the details of the steps involved:
1. Determine the index of the last row in the array by using the expression `array.length - 1`. This will give you the index of the last row in the array since array indices start from 0.
2. Determine the index of the last column in the array by using the expression `array[0].length - 1`. This expression accesses the first row in the array (array[0]) and calculates the length of that row (number of columns) and then subtracts 1 to get the index of the last column.
3. Use the above calculated indices to access the last column of the last row in the array, which is `array[array.length - 1][array[0].length - 1]`.
4. Assign the value 55.0 to this specific element in the array by using the assignment operator (`=`).
This statement will assign the value 55.0 to the last column of the last row in the array.
To know more about array visit:-
https://brainly.com/question/31044154
#SPJ11
For a normal startup Windows Boot Loader loads which of the following into memory?
A. All of these get loaded
B. System registry hive
C. Ntoskernel
D. OS kernel
Answers
During a normal startup, the Windows Boot Loader loads the system registry hive and the Ntoskernel into memory. The correct answer is option C.
The system registry hive contains configuration information about the computer hardware and software, while the Ntoskernel is the main component of the Windows operating system that manages system resources and provides services to other system components.
The OS kernel is also loaded into memory, but it is a component of the Ntoskernel. Therefore, option A, which states that all of these get loaded, is not incorrect, but options B and C are the specific components that are directly loaded by the Windows Boot-Loader.
Therefore option C is correct.
Learn more about Kernel:
https://brainly.com/question/30265745
#SPJ11
In our situation now a days in online class we are experiencing different problems such as internet
problems like internet connection low quality gadgets technical problems using laptops and computers set up as an ict student how can you solve these common learning problems based on the knowledge you gained in computer hardware servicing
Answers
Enumerate a couple of reasons why it would be impracticable for the external devices to be connected directly to the processor or the system bus
Answers
Answer:
(a) Difference in data transfer rates
(b) Difference in word lengths
(c) Different peripherals with different modes of operation
Explanation:
There are several reasons. Some of them have been listed in the explanation section. A brief explanation is as follows
(a) Difference in data transfer rates
Some peripherals have fast transfer rate while some have slow transfer rates compared to the processor they are being connected to. This difference in the rates implies that a high speed system bus will find it difficult to communicate with a (say) low speed peripheral.
(b) Difference in word lengths
Another consideration is the word lengths. Often times, peripherals and the bus they are being connected with will have a different word lengths.
(c) Different peripherals with different modes of operation
In computer architecture, a processor can not be used to interact with peripheral of different mode of operations. In other word, each peripheral have its own mode and will require different means of connection.
how do the conditional operators work when the operands are strings?
Answers
All operators function in binary, and the basic syntax is A operator B. The comparison is performed using the values of the operands when operands A and B are both integers. Instead, a comparison is drawn using the alphabet. Comparisons between strings are case-sensitive.
Conditional (ternary) operator:The conditional (ternary) operator is the only JavaScript operator that allows three operands: a condition, an expression to be evaluated if the condition is true, and an expression to be executed if any of the circumstances, all of which are indicated by a question mark (? ), is false. When an if...else statement would be appropriate, this operator is frequently used instead.
If both operands are numeric strings, or if one operand is a number and the other is a numeric string, the comparison is performed numerically. Same requirements apply to the switch statement. When the comparison is === or!==, the type is not converted because these comparisons compare both the type and the value.
Learn more about conditional operators, visit:
https://brainly.com/question/13260049
#SPJ4
Your employer has asked you to create a
presentation for a new product demonstration. You
are asked to include a slide that will show the
specs of your company's product stacked up
against specs of a competitor's product. Which
slide layout should you choose to
do this?
Otitle slide
O section header
Opicture with caption
O comparison
Answers
A RESTful service, such as the open weather service use used in an activity in this class, sends and receives data in the form of JSON or JavaScript Object Notation. This data is in the form of:Group of answer choicesa sequencea stringa key/value paira list
Answers
Answer:
A key/value pair
Explanation:
JSON or JavaScript Object Notation uses key/value pairs to represent data.
Here's an example:
{
name: "Jordan Carter"
age: 25
}
Data can be then accessed using a key such as "name" to get the value "Jordan Carter."
Python is an example a blank while blank is an example of a software framework.
Answers
Answer:
programming language.
Middleware
Explanation:
write a program to output a big A like the one below

Answers
hope this helps, i'm a beginner so this might not be the most concise method

In computer security, the term "Dumpster diving" is used to describe a practice of sifting through trash for discarded documents containing sensitive data. Found documents containing names and surnames of the employees along with the information about positions held in the company and other data can be used to facilitate social engineering attacks. Having the documents shredded or incinerated before disposal makes dumpster diving less effective and mitigates the risk of social engineering attacks.A. TrueB. False
Answers
Answer:
TRUE
Hope this helps ;)
Computer Vision and Industrial Robots
Consider an industrial robot performing several tasks in an assembly line. Such machines perform a single task with great speed and efficiency. Conduct research on the Internet and list what you feel would be its main components if computer vision was implemented. Ask yourself what are the advantages of adding a computer vision system to this robot. Which robot do you expect better performance from, a robot with computer vision or robot without computer vision.
Answers
Answer:
View Computer Vision Unit Activity.docx from COMPUTER SCIENCE 101 at Edoptions High School. Consider an industrial robot performing several tasks in an assembly line.Machine Vision in industrial applications. Robots working in industrial applications need visual feedback. This is used to navigate, identify parts, collaborate with humans and fuse visua
Explanation:
Many industries are feeling the effects of skilled labor shortages. At the same time, companies are reluctant to invest heavily in training and developing unskilled employees, for fear of losing them afterward through defection to competitors. With no end in sight to the workforce shortfall, the appeal of robots as an efficient supplement, and even replacement, for human labor is continuing to grow.
The cost of robotics is generally falling, and alternative business models like robotics-as-a-service (RaaS) make industrial robots accessible even to companies that don’t have substantial capital budgets to exploit. The affordability of the units themselves, along with the fact that programming is becoming more straightforward and hence less costly, is also boosting the appeal of industrial robotics adoption.
Answer:if u still need help i can help you
Explanation:
what function does a driver perform on the computer
Answers
Answer:
A driver, or device driver, is a set of files that tells a piece of hardware how to function by communicating with a computer's operating system. All pieces of hardware require a driver, from your internal computer components, such as your graphics card, to your external peripherals, like a printer.
Explanation:
Operating systems as well as other computer applications can access hardware features with the help of drivers, which provide a software interface between hardware devices. This eliminates the need for users to be aware of the exact specifications of the hardware being utilised.
What is the purpose of a device driver?A device driver is a piece of specialized software that manages a specific computer-connected device; by providing a software interface to the hardware, it enables operating systems and other computer programs to access hardware functionalities.
How does a device driver work? Can you list all of its operations?The operating system and its running programs send requests for device access and actions to the corresponding hardware devices through device drivers. In addition, they transmit messages or status information from the hardware to the operating system, which in turn transmits it to the apps.
Get More about drivers Visit:
https://brainly.com/question/14308161
#SPJ4
1.
Which of the following is NOT caused by alcohol?
Answers
Answer:
What are the choices
Answer:
Explanation:reduced concentratjon
inhibited comprehension
decreased coordination
increased heart rate
Brainless is one the way if you help

Answers
Answer:
1. x - 6
2. p - ? = 7
i chose these equations because
a number - 6 = the weight of your backpack.
p - an unknown number without a substitute variable = slices of bread left.
How to connect two routers wirelessly to extend range.
Answers
You can easily extend your wifi network with additional networking hardware like wifi repeaterw and wireless acces points
The lifetime of a new 6S hard-drive follows a Uniform
distribution over the range of [1.5, 3.0 years]. A 6S hard-drive
has been used for 2 years and is still working. What is the
probability that it i
Answers
The given hard-drive has been used for 2 years and is still working. We are to find the probability that it is still working after 2 years. Let A denote the event that the hard-drive lasts beyond 2 years. Then we can write the probability of A as follows:P(A) = P(the lifetime of the hard-drive exceeds 2 years).By definition of Uniform distribution, the probability density function of the lifetime of the hard-drive is given by:
f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.where a = 1.5 years and b = 3.0 years are the minimum and maximum possible lifetimes of the hard-drive, respectively. Since the probability density function is uniform, the probability of the hard-lifetime of a new 6S hard-drive follows a Uniform distribution over the range of [1.5, 3.0 years]. We are to find the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years.Let X denote the lifetime of the hard-drive in years.
Then X follows the Uniform distribution with a = 1.5 and b = 3.0. Thus, the probability density function of X is given by:f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.Substituting the given values, we get:f(x) = 1/(3.0 - 1.5) = 1/1.5 if 1.5 ≤ x ≤ 3.0; 0 the integral is taken over the interval [2, 3] (since we want to find the probability that the hard-drive lasts beyond 2 years). Hence,P(A) = ∫f(x) dx = ∫1/1.5 dx = x/1.5 between the limits x = 2 and x = 3= [3/1.5] - [2/1.5] = 2/3Thus, the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years is 2/3.
To know more about Uniform distribution visit:
brainly.com/question/13941002
#SPJ11
what does redundancy mean in the context of internet routing?
Answers
To ensure that data can continue to flow even in the event of a breakdown, networks must be redundant. In other words, more redundancy equals more reliability.
What is redundancy?In order to ensure that data can continue to flow even in the case of a breakdown, networks must be redundant.
In other words, more redundancy equals more reliability.
Additionally, it supports distributed site management.
The idea is that if one device malfunctions, another may take over immediately.
The process of maintaining data in two or more locations within a database or data storage system is known as data redundancy.
Data redundancy ensures that a company can continue to operate or provide services even if something were to happen to its data, such as corruption or loss.
Therefore, networks must be redundant in order to guarantee that data may still flow even in the event of a failure. In other words, more redundancy equals more reliability.
Know more about redundancy here:
https://brainly.com/question/17880618
#SPJ4
Which of the following is not a data cleansing activity? Multiple Choice Identifies redundant records Identifies inaccurate or incomplete data Identifies missing records or attributes Identifies sales trends
Answers
Identifying sales trends is not a data cleansing activity. Data cleansing activities primarily involve rectifying data issues, while identifying sales trends falls under the realm of data analysis for business insights.
Data cleansing refers to the process of identifying and correcting or removing errors, inconsistencies, and inaccuracies in a dataset. It aims to improve data quality and ensure reliable and accurate information for analysis and decision-making. The provided options consist of activities that are typically part of data cleansing, except for identifying sales trends.
Identifying redundant records involves identifying and eliminating duplicate entries in a dataset, ensuring that each record is unique. Identifying inaccurate or incomplete data entails identifying and correcting data that is incorrect or lacks necessary information. Identifying missing records or attributes involves identifying gaps in the dataset where certain records or essential attributes are absent. These activities contribute to enhancing the quality and completeness of the data.
On the other hand, identifying sales trends falls under the domain of data analysis rather than data cleansing. Sales trends analysis involves examining historical sales data to identify patterns, fluctuations, and insights related to sales performance over time. While it is valuable for business intelligence and decision-making, it focuses on interpreting and understanding data rather than cleansing or improving its quality.
Learn more about data here:
https://brainly.com/question/13441094
#SPJ11
help me asap ill give brainliest

Answers
Answer:
Give me brainliest thanks
2
ng and Upgrading Computers: Mastery Test
Select the correct answer.
Which of the following can computer maintenance software determine?
O A.
O B.
O C.
O D.
whether your hard drive is about to fail
whether your monitor or screen is drawing too much power
the humidity inside your desktop computer
the amount of dust inside your laptop
Reset
Next
Answers
whether your hard drive is about to fail can computer maintenance software determine.
What is computer maintenance software ?
Software that centralises maintenance data and streamlines maintenance operations is known as a computerised maintenance management system, or CMMS. It aids in maximising the use and accessibility of tangible assets like machines, transportation, communications, plant infrastructures, and other assets. CMMS systems, also known as computerised maintenance management information systems (CMMIS), are used in the manufacturing, energy, transportation, building, and other sectors where physical infrastructure is essential.
A CMMS's database is its fundamental component. The information regarding the assets that a maintenance organisation is responsible for maintaining, as well as the tools, supplies, and other resources needed to do so, are organised using a data model.
Read more about computer maintenance software:
https://brainly.com/question/28561690
#SPJ1
Assume my_string references a string. Write a statement that uses a slicing expression and displays the first three characters in the string.
Write in python
8
Answers
mystring = 'waterfall' print(mystring[0:3]) uses a slicing expression to show the string's first three characters.
Which approach would you employ to ascertain whether a substring is contained within a string?The. includes() method is the most effective approach to determine whether a substring is present. It is offered by the String class and is extremely effective. The method takes a CharSequence as an input and returns true if the sequence is valid.
In Python, how do you slice a letter?The same method is used by Python to cut a string off at the end. To specify the first character to include, use the starting index; do not use the end index. String[start position:] is the syntax for performing this operation. Negative indexing can also be used for slicing.
To know more about Python visit:-
https://brainly.com/question/30427047
#SPJ1
Answer:
Here's a Python statement that uses slicing to display the first three characters of the string referenced by my_string:
my_string = "example string"
first_three_chars = my_string[:3]
print(first_three_chars)
In this example, we first create a string my_string that contains the value "example string".
The slicing expression [:3] selects a slice of the string that starts from the beginning (denoted by : without a first index) and goes up to the 3rd character (denoted by 3).
The resulting slice is assigned to a variable first_three_chars, and then printed to the console using the print() function. This should output the first 3 characters of the string, which in this case is "exa".
A computer game allows a player to repeat a level until they run out of lives. Which two of the following loops would work correctly?

Answers
Answer:
c.
Explanation:
because this is the right syntax for the following loops
Describe how you use the ruler icon to indent text in two different ways.
Answers
Drag the arrow at the top of the ruler to add or change the first line indent. Only the first line of the paragraph where cursor is located will be indented as a result. Choose the triangle and move it to create a hanging indent.
How do you make a ruler indent?Choose the text in which to insert a first line indent. On the ruler, drag the triangular marker on the top left of the ruler to the place you want the indentation to start, for example to the 1" mark.
How many types of indent are there on ruler?Ruler format the left, right, top and bottom margins of page. Paragraph indentation: Indentation describes the starting point of a paragraph. Ruler format the First line indentation.
To know more about cursor visit:-
https://brainly.com/question/30355731
#SPJ1
what makes a role more or less likely to be replaced by a robot or an automated process
Answers
Answer:
So let's look at the seven occupations that won't be mechanized.
educators and teachers. Teaching and education are the first occupations or career paths that appear on our list. ... project managers, social workers, lawyers, programmers, systems analysts, healthcare professionals, carers, designers, and artists.
Explanation:
hope this helps
which methods can you use to migrate user settings from windows 8.1 to windows 10? (choose all that apply.)
Answers
Note that the methods can you use to migrate user settings from Windows 8.1 to Windows 10 are:
Use the User State Migration Toolkit. (option A)Perform an upgrade over the top of the old operating system. (Option E). This is called Windows Migration.What is Windows Migration?Migration programs are available to migrate settings from one Windows PC to another. These tools only transfer program settings and not the applications themselves. See the Application Compatibility Toolkit for additional information on application compatibility (ACT).
Migration Toolkit is a robust command-line utility that provides granular control over the migration process. The Migration Toolkit assists in the migration of database objects and data from an Oracle database to an EDB Postgres Advanced Server or PostgreSQL database.
Note that the Windows Update is a cloud-based service that keeps Microsoft Windows and other Microsoft applications, such as Windows Defender, up to date. Patches and updates often offer feature additions as well as security fixes to safeguard Windows against viruses.
Learn more about Windows MIgration:
https://brainly.com/question/29353983
#SPJ1
Full Question:
Which methods can you use to migrate user settings from a previous operating system to Windows 10? (Choose all that apply.)
Use the User State Migration Toolkit.
Use Remote Desktop to copy to files.
Use Windows Easy Transfer.
Copy the user profile from the old computer to the new computer.
Perform an upgrade over the top of the old operating system.
Write a white paper or PowerPoint presentation demonstrating that you understand the essential elements of a patch
management program. Evaluate at least three patch management software solutions, recommend one, and describe why
you are making this recommendation
Use the list provided in the lesson as your template and search the Internet for information on patch management
concepts and vendor solutions to help create your plan.
Answers
Answer:
When is this due?
Explanation:
I will write it
Use the drop-down menus to complete statements about safe and blocked senders lists.
*Safe *Blocked *repeatedly

Answers
Answer:
it already has an answer and it's right so i don't see the point to needing to answer this
Write two example of an operating ystem please give fast answer
Answers
Answer:
microsoft windows
Linux
Ios
Android
Explanation:
Please mark me as brainlist.
please help
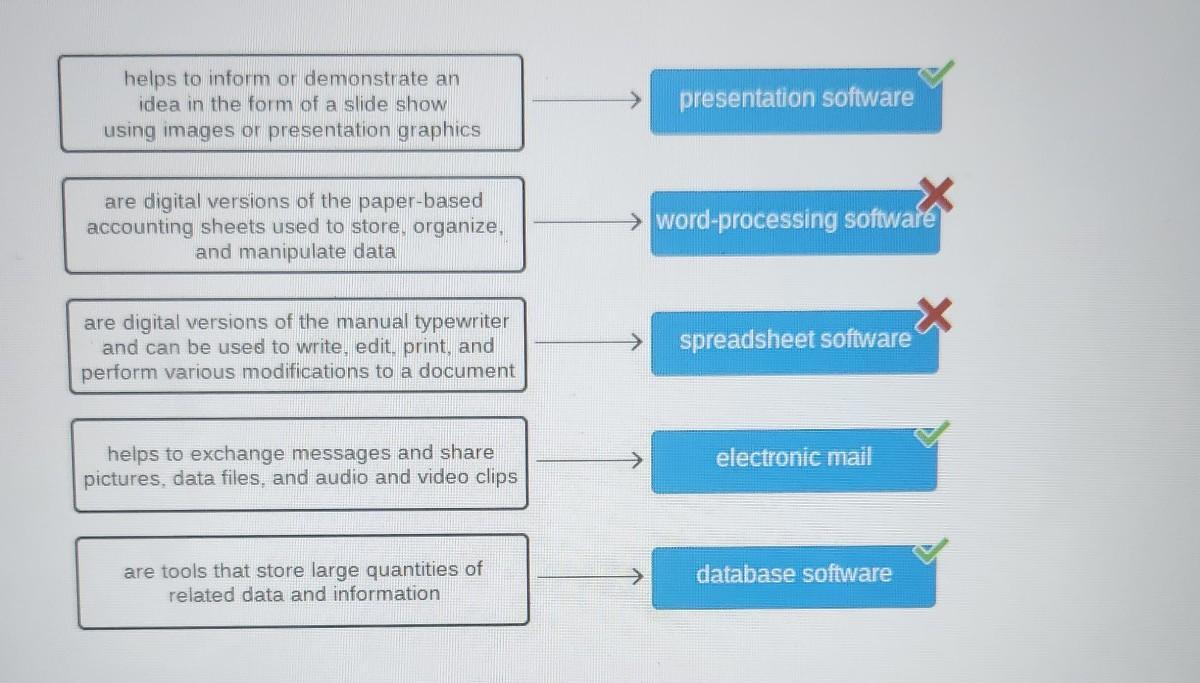
match the features with the software
Word Processor, Spreadsheet, Database
- addiction of images, drawings, tables and graphics to text
- centralized data management
- data security
- digital version accounting sheets
- supports multiple users for adding data simultaneously
- visual representation of data
- digital version of a typewriter
Answers
Answer:
word processor- addition of images, drawing tables, and graphics to texts and digital version of a typewriter. spreadsheet- digital version of accounting sheets and visual representation of data. database- centralized data management, data security, and supports multiple users for adding data simultaneously
Just switch the two I got wrong and you'll get the correct answers. :)