4. Write a MATLAB code implementing the Inverse Matrix Method. Check your answer with ""Left Division"". Attach after this sheet: (4 points) (both cases where Vs = 5and 7 V) a) m-file b) output NOTE: R1 = R2 = 10092 and R3 = R4 = 20092.
Answers
The Inverse Matrix Method is a technique used in solving systems of linear equations. The method involves finding the inverse of the coefficient matrix and multiplying it by the constant vector to obtain the solution vector.
Here is the MATLAB code implementing the Inverse Matrix Method:
% Define the resistance values
\(R_1 = 10092;\\R_2 = 10092;\\R_3 = 10092;\\R_4 = 10092;\)
% Define the voltage source values
\(Vs_1 = 5;\\Vs_2 = 7;\)
% Define the matrix and vector equations
\(A = [1/R_1+1/R_2, -1/R_2; -1/R_2, 1/R_2+1/R_3+1/R_4];\\V = [Vs_1;/R_1; Vs_2/R_3];\)
% Solve for the current values using the inverse matrix method
\(I = A^{-1} * V;\)
% Display the current values
\(disp(I)\)
% Check the current values using the left division
I_left = \([1/R_1 + 1/R_2, -1/R_2; -1/R_2, 1/R_2 + 1/R_3 + 1/R_4] [Vs_1/R_1; Vs_2/R_3];\)
% Display the left division results
disp(I_left);
The resistance and voltage source values are defined first in this code. We then use these numbers to define the matrix and vector equations. The A matrix represents the current equation coefficients, while the V vector represents the voltage values. We then solve for the current values using the inverse matrix approach \((A^{-1} * V)\).
Finally, we check the current values using left division ([A\b] in MATLAB), which should give us the same results.
Learn more from MATLAB:
https://brainly.com/question/15076658
#SPJ11
Related Questions
Synonyms. decorate. verb. to make something look more attractive by
Answers
We must evaluate the possibilities and lay the foundation before we can comprehend the reasoning behind the response.
First of all, we recognize that the definition states that this notion aids in making judgments. However, the synonyms make it clear that you can also give the objects under examination a value. Rating and rate are therefore synonyms since the meaning of the words suggests that a rate is given a value based on many attributes in order to give it a level of order as a result of its characteristics. Cosmetics are made from chemicals and are used to improve skin quality and physical attractiveness. Chemical items used to enhance appearance are called cosmetics. Cosmetics are a broad category that encompasses a wide range of products or chemicals. They are frequently categorized as products for beauty and health. Some natural ingredients are combined with artificial components that have been synthesized to create cosmetics. Deodorants, perfumes, lip gloss, and other cosmetics are some examples.
Learn more about Cosmetics here:
https://brainly.com/question/20699735
#SPJ4
which is true regarding how methods work? group of answer choices after a method returns, its local variables keep their values, which serve as their initial values the next time the method is called a method's local variables are discarded upon a method's return; each new call creates new local variables in memory a return address indicates the value returned by the method
Answers
The correct statement for working of method is-
A method's local variables are discarded upon a method's return; Each new call creates new local variables in memory.What is the working of the method?Work methods are indeed the physical actions used to complete a task.
An effective ergonomics program includes several components, one of which is evaluating as well as modifying work methods to avoid discomfort and injury. Ergonomics programs include work method analysis to make sure that safe practices are used for job tasks. Training and work practitioner controls then are implemented to make sure that appropriate methods for reducing employee exposure to intuitive risks are used.Thus, for the given question;
A local variable is a variable that can only be accessed within a specific section of a program.These variables are typically defined in that routine and are considered to be local to that subroutine.Thus, we can conclude that each new call to a method's local variables can result in the creation of new local variables throughout memory.
To know more about the local variables, here
https://brainly.com/question/28274892
#SPJ4
Select the correct answer from each drop-down menu A manipulator and the end effector work together to execute a robot's tasks A manipulator is a series of joined segments, whose function is to capable of The manipulator is thus

Answers
The end effector and the manipulator collaborate to carry out a robot's operations. A manipulator is made up of a number of connected segments that are used to position and direct the end effector.
Which area of the robotic manipulator is utilized for object positioning within the robot work volume?The robot manipulator is divided into two parts: Body-and-arm - for positioning things within the work volume of the robot. Wrist assembly for object orientation.
Where is the manipulator's end effector connected?An end effector is an accessory that fastens to a robot's wrist and enables it to interact with the task at hand.
To know kore about manipulator visit:-
https://brainly.com/question/30002364
#SPJ1
how many country on earth
Answers
Answer:
195 countries
I think Soo
Answer:
there are 195 countries on earth
A single computer on a network is called a____________.
Answers
Answer: A single computer on a network is called a node. pls brainliest
SXXSSSSSSSSSZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ
Answers
Answer:
okkkk
Explanation:
MARK ME BRAINLIEST PLZZZZZZZZZZZZZZZZZZZZZZZZzzzzzzzzzzzzzzzzzzzzWhat does it mean when someone endorses you on linkedin.
Answers
Answer:
LinkedIn endorsements are a way for the people in your network to confirm your aptitude and experience within your professional field. Every endorsement you get on the skills listed on your LinkedIn profile helps you to be more easily found and, just maybe, to land the job you've always wanted.
Explanation:
What is a closed source operating system?
Answers
Answer:
Answer- use code that is proprietary and kept secret to prevent its use by other entities
Explanation:
Explanation- Closed-source operating systems use code that is proprietary and kept secret to prevent its use by other entities. Traditionally, they are sold for a profit. Open-source operating systems use code that is freely-distributed and available to anyone to use, even for commercial purposes.
Answer:
closed-source operating systems use code that is proprietary and kept secret to prevent its use by other entities.
Explanation:
ttyyy!!
What is a benefit of being a member of a professional organization?
Answers
Answer: A benifit of being a member of a proffesional organzation is you can refresh your knowledge by acquiring new skills through workshops, seminars, and conferences.
Explanation:
Toda vez que a minha internet cai a conexão, meu ip fica mudando, daí as coisas que dependem do meu ip cadastrado não funciona, o que pode ser qual poderia ser a possível solução?
Answers
Answer:
Seu ISP muda sua infraestrutura de rede. Causando como os endereços IP são atribuídos para mudar. O ISP muda o centro ou roteador responsável pelo seu endereço. O ISP encontrou uma falha na rede, causando a reconstrução das tabelas de roteamento ou outros problemas relacionados à rede. Se você não tem a opção de configurar o DHCP, ou apenas precisa que seu PC mantenha seu IP por um período limitado de tempo, definir um endereço IP estático será o caminho a percorrer. Abra o Painel de Controle e clique em Rede e Internet> Centro de Rede e Compartilhamento> Alterar configurações do adaptador.
desculpe se isso é difícil de entender, português não é minha língua nativa
A school has an intranet for the staff and students to use. Some of the files stored on the intranet are confidential. Give two reasons why a school may have an intranet.
Answers
Answer:
explanation below
Explanation:
An intranet could be defined as a computer network that is used for sharing information, operational systems, collaboration tools and other computing tasks within a company or organization such as schools. It is usually structured to exclude excess by those outside of the organization.
Intranet provides a lot of benefits to organization where it is been used and they are as seen below :
1. Users can effectively update and view their documents with ease – scheduling meetings, managing of classroom curriculum and preparing of projects can be done with less stress.
2. It can be used to keep accurate staff records – employees can have their details rightly stored using the intranet and a photograph can also be used.
What do Cc and Bcc stand for?
O Clear Copy and Binary Clear Copy
O Counter Claim and Best Counter Claim
O Crystal Clear and Binary Crystal Clear
O Carbon Copy and Blind Carbon Copy
Answers
Thank You!
computer science, a structured programming approach using c, forouzan and gilberg, third edition pdf
Answers
A Structured Programming Approach Using C" by Forouzan and Gilberg. This book focuses on the structured programming approach using the C programming language.
It covers topics such as algorithms, control structures, functions, arrays, pointers, and file processing. The third edition is an updated version of the book, providing more examples and exercises for students to practice. It is commonly used as a textbook in computer science courses. In conclusion, "Computer Science: A Structured Programming Approach Using C" by Forouzan and Gilberg is a valuable resource for learning about structured programming in computer science using the C programming language.
To know more about Structured Programming, visit:
https://brainly.com/question/33453996
#SPJ11
There are many different types of decision-making. Which of the following is NOT a type of decision-making? a. fiat rule b. single decision-maker c. majority rule d. consensus/collaboration
Answers
Answer:
These are all correct but if you want to get technical I would choose A, because fiat rule is used in the military without any consent from any political standpoint.
Explanation:
Answer:
the answer is A
Explanation:
In a ______, the bars that represent the categories of a variable are spaced so that one bar is not directly next to another; whereas in a ______, the bars actually touch one another.
Answers
Answer:
The correct answer would be "bar graph; histogram".
Explanation:
The bar graph has become a photographic arrangement of information which always practices that relate bars to consider various give information. Alternatively, this is indeed a diagrammatic comparative analysis of univariate data. This same histogram demonstrates the variation including its frequency of repeated measures, introduces numerical information.is makes it possible to evaluate performance by capturing current data in addition to analyzing historical data. often managers are faced with an overwhelming volume of data and analyzing it becomes very time consuming, a situation known as:_____.
Answers
An overwhelming volume of data and analyzing it becomes very time-consuming, a situation known as Analysis paralysis.
What is the process of data analysis?
The process of gathering, purifying, classifying, and processing raw data in order to derive pertinent and beneficial information for enterprises is known as data analytics.A thorough grasp of data can enhance customer satisfaction, customer retention, targeting, operational cost reduction, and problem-solving techniques. Finding insights into data, such as measurements, facts, and statistics requires the use of data analysis methodologies and procedures.Techniques for qualitative and quantitative data analysis are the two main approaches to data analysis. Data analysis tools are software and programs that gather and analyze data about a company, its clients, and its competitors in order to streamline operations and help decipher patterns so that decisions may be made using the data.The findings are shared, offering interpretations and aiding in decision-making.To learn more about data analysis refer to:
https://brainly.com/question/29384413
#SPJ4
What are the major constraints of a camp watchtower
Answers
A camp watchtower is a structure built to provide an elevated view of the surrounding area to enable the watchman to monitor the camp or its perimeter for any potential threats. However, there are some major constraints to consider when building a camp watchtower:
Limited visibility: A watchtower can only provide a limited view of the surrounding area, depending on its height and location. Obstacles such as trees or other structures can limit the view and reduce the effectiveness of the watchtower.Vulnerability to weather conditions: A watchtower can be vulnerable to harsh weather conditions such as high winds, heavy rain, or lightning strikes. This can compromise the integrity of the structure and make it unsafe for the watchman.Accessibility: The watchtower must be accessible to the watchman, which can be difficult in remote or rugged areas. If the watchtower is too difficult to access, it may not be used effectively.Maintenance: The watchtower requires regular maintenance to ensure its safety and effectiveness. This can be time-consuming and expensive, especially in remote locations.Cost: The construction of a watchtower can be expensive, and it may not always be a feasible option for small or low-budget camps.
To learn more about watchtower click the link below:
brainly.com/question/31055341
#SPJ4
compare the four ways of regulating the internet
Answers
Answer:
the four is all the same way that can harm people through the internet
Explanation:
hi what is full form of ugst
Answers
Answer:
UGST – Union Territory Goods & Services Tax.
Answer:
Explanation:
Hello friend
Here's your answer
The full form of UTGST is Union Territory Goods and Service Tax
Hope this helps
plz mark as brainiest!!!!!!
Write a informational paragraph that compares and contrast climate and weather include specific details for each
Answers
Answer:
The main difference between weather and climate refers to their temporal extension, that is, while weather refers to the climatic and meteorological conditions in the short term (rain forecasts, temperatures, atmospheric pressure, etc., which are going to happen in the next few days), the climate is a compilation of all these conditions and their averaging, to account for long-term weather conditions (thus, for example, if in December there is an average temperature of 0ºC, or the amount of snow that usually accumulates in that month, etc., that is, it is a much more macro look of what the climate is in a certain territory).
Which of the following is not a main method for sending information from one computer to
another?
Electricity
Light
Molecules
Radio
Answers
Molecules are not the main method for sending information from one computer to another. Thus, option C is correct.
There are the multiple method of sending information that using the radio waves most commonly used now a days. A Wireless method of sending information using radio waves.
A wireless router has receives the signal as well as decodes it. The router sends the information to the Internet using a physical, wired Ethernet connection. and sending information through radio waves involve two devices .One is receiver device and other is sending device.
Therefore, Molecules are not the main method for sending information from one computer to another. Thus, option C is correct.
Learn more about radio on:
https://brainly.com/question/29787337
#SPJ1
¿ Porque la madera presenta mayor resistencia a ser cortada en sentido travesal que en sentido longitudinal
Answers
La madera es más fuerte en la dirección paralela al grano. Debido a esto, las propiedades de resistencia y rigidez de los paneles estructurales de madera son mayores en la dirección paralela al eje de resistencia que perpendicular a él
Which term is most closely associated with cellular manufacturing?A. part familiesB. assembly lineC. roboticsD. CADE. CAM
Answers
The term most closely associated with cellular manufacturing is A. part families.
Cellular manufacturing is a production method that organizes machines and equipment into cells to produce a specific set of similar products. Part families refer to a group of parts that have similar design and production characteristics. By grouping parts into families, cellular manufacturing aims to streamline production and improve efficiency. Cellular manufacturing is a production method that organizes machines and equipment into cells to produce a specific set of similar products. Part families, which refer to a group of parts with similar design and production characteristics, are closely associated with cellular manufacturing. By grouping parts into families, cellular manufacturing aims to streamline production and improve efficiency. This grouping allows for the utilization of common tools, processes, and setups, reducing the setup time and facilitating faster production. By organizing machines into cells and using part families, cellular manufacturing provides a flexible and efficient approach to production.
Part families are the term most closely associated with cellular manufacturing.
To know more about Streamline, Visit :
https://brainly.com/question/29708350
#SPJ11
When creating envelopes, how will you adjust the layout?
A.
clicking the Insert menu
B.
clicking the Edit button
C.
clicking the Format tab
D.
clicking the Setup button
E.
clicking the Print button
Answers
Answer:
D
Explanation:
Select all the correct answers.
Which TWO of the following are recommended practices to protect users' privacy while using email services?
Avoid forwarding a personal emails to others.
Avoid forwarding jokes and trivia using email.
Avoid using webmail if you have an email client on your computer.
Avoid opening emails from unrecognized senders.
Avoid using webmail in the workplace:
Answers
Answer: Avoid forwarding a personal email to others and most likely Avoid forwarding jokes and trivia using email.
The recommended practices to protect users' privacy while using email services are options A and C: avoid forwarding a personal emails to others and avoid using webmail if you have an email client on your computer.
What do you mean by term E-mail?
An E-mail is refers to as the communication source. It is a specialized computer network that stores, processes, and send the material from one person to another within seconds..
E-mail is considered as the computer equivalent but it has many advantages like timeliness and flexibility.
Moreover, the content of email include text, files, images or other kind of attachments send by the specified person to the one or more than one groups.
In order to protect the personal data of the user, it is recommend that people should note share their personal information with other and specially the young generation do not use webmail if the another party already utilize your computer.
Nowadays more frauds are happen due to the fact that people are more indulge in these communications for their better advancements. So, we have to take every step very carefully.
Therefore, correct options are A and C.
Learn more about E-mail, refer to the link:
https://brainly.com/question/13313275
#SPJ2
3.5 code practice
grade = str(input("What year of high school are you in?: "))
if ("grade ==Freshman"):
print("You are in grade: 9")
elif ("grade == Sophomore"):
print("You are in grade: 10")
elif ("grade == Junior"):
print("You are in grade: 11")
elif ("grade == Senior"):
print("You are in grade: 12")
else:
print("Not in High School")
It keeps printing your are in grade 9. Why?
Answers
The fixed code is shown below. input() function already returns string that's why you don't have to convert string again. Also the syntax in if-else scope is wrong.
grade = input("What year of high school are you in?: ")
if(grade.lower()=="freshman"):
print("You are in Grade 9.")
elif(grade.lower()=="sophomore"):
print("You are in Grade 10.")
elif(grade.lower()=="junior"):
print("You are in Grade 11.")
elif(grade.lower()=="senior"):
print("You are in Grade 12.")
else:
print("Wrong input!")
Technician A says backup sensors use LEDs to detect objects. Technician B says that a backup sensor won't work correctly if the paint is thicker than 0.002 inch. Which technician is correct
Answers
Answer:
Technician B
Explanation:
As in the question, it is mentioned that according to the Technician A the backup sensors used LED for tracking the objects and as per the technician B the backup sensor does not work correctly unless the paint is thicker than 0.002 inch
Therefore according to the above explanation, the technician B is correct as it provides the valid reason
Which of these jobs would be most appropriate for someone who majors in information systems? A. Managing a group of programers B. Creating a cloud based customer service application app C. Providing telephone tech support D. Designing a database for an online retailer.
Answers
Answer:
B. Creating a cloud based customer service application app
Explanation:
Information Systems is described as an "academic study of various systems encompassing a particular reference associated with the complementary networks and information of the software and hardware that different organizations and people use to collect, create, process, distribute, and filter data.
The information system includes an integrated pair of different components for storing, collecting, and processing data, along with this, it is utilized for providing knowledge, information, and digital products.
In the question above, the correct answer is option-B.
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
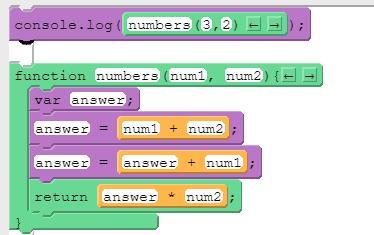
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
EASY POINTS who is your favorite in family
1. mom
2. dad
3. sister
4. brother
Answers
Answer:
Thank you! And it would be my dad.
Explanation: